Windows 10 Secured-Core PCs Can Block Driver-Abusing Malware
By Sergiu Gatlan March 17, 2020 03:30 PM 0
Microsoft says that Windows 10 Secured-core PCs can successfully defend their users against malware designed to take advantage of driver security flaws to disable security solutions.
"Multiple malware attacks, including RobbinHood, Uroburos, Derusbi, GrayFish, and Sauron, and campaigns by the threat actor STRONTIUM, have leveraged driver vulnerabilities (for example, CVE-2008-3431, CVE-2013-3956, CVE-2009-0824, CVE-2010-1592, etc.) to gain kernel privileges and, in some cases, effectively disable security agents on compromised machines," Microsoft says.
However, according to Microsoft, endpoint devices can be defended against such attacks if you are using a Secured-core PC that comes with built-in protection against firmware attacks that have been increasingly used by both state-sponsored hacking attacks and commodity malware.
Secured-core PCs were released as a solution to the number of increasing firmware security issues that attackers can exploit to bypass a Windows machine's Secure Boot, as well as to the lack of visibility at the firmware level commonly present in today's endpoint security solutions.
Malware abusing vulnerable firmware and drivers
"In addition to vulnerable drivers, there are also drivers that are vulnerable by design (also referred to as 'wormhole drivers'), which can break the security promise of the platform by opening up direct access to kernel-level arbitrary memory read/write, MSRs," Microsoft adds.
"In our research, we identified over 50 vendors that have published many such wormhole drivers. We actively work with these vendors and determine an action plan to remediate these drivers."
One instance of a threat actor abusing firmware vulnerabilities is the Russian-backed APT28 cyber-espionage group (also tracked as Tsar Team, Sednit, Fancy Bear, Strontium, and Sofacy) who used a Unified Extensible Firmware Interface (UEFI) rootkit dubbed LoJax during some of its 2018 operations.
More recently, the operators behind the RobbinHood Ransomware exploited a vulnerable GIGABYTE driver to elevate privileges and install malicious unsigned Windows drivers that allowed them to terminate antivirus and security software processes on compromised systems.
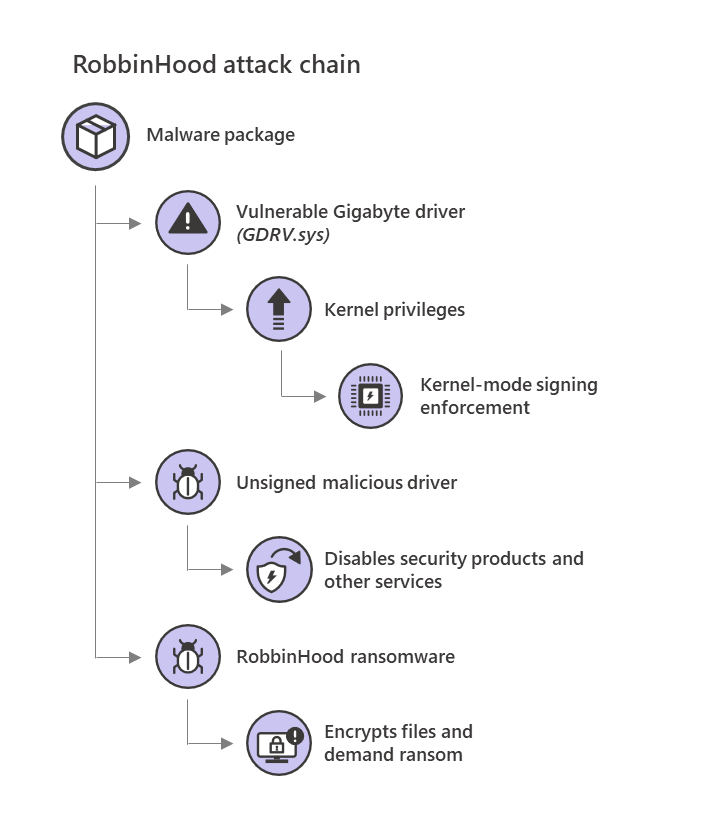 RobbinHood Ransomware attack chain (Microsoft)
RobbinHood Ransomware attack chain (Microsoft)"In this attack scenario, the criminals have used the Gigabyte driver as a wedge so they could load a second, unsigned driver into Windows," Sophos researchers explained at the time.
"This second driver then goes to great lengths to kill processes and files belonging to endpoint security products, bypassing tamper protection, to enable the ransomware to attack without interference."
This tactic enabled the attackers to circumvent anti-ransomware defenses by killing the antivirus software before deploying the ransomware executable used to encrypt the victim's documents.
Sophos was unable to fully analyze this ransomware sample so far therefore the processes and services that are being targeted are currently unknown.
Secured-core PCs feature built-in protection
As Microsoft says, however, Windows 10 comes with hardware and firmware protection features that can successfully fight against attacks such as the one that infected victims with Lojax and RobbinHood Ransomware.
Moreover, Secured-core PCs introduced by Microsoft in October 2019 in partnership with OEM partners Lenovo, HP, Dell, Panasonic, Dynabook, and Getac can block firmware-level attacks as they come with these hardware-backed security features enabled by default removing the need for users to make the required BIOS and OS settings changes manually.
"Because both BIOS settings and OS settings are enabled out of the box with these devices, the burden to enable these features onsite is removed for customers," Microsoft adds, with the following features being turned on all Secured-core PCs:
Security promise Technical features
Protect with hardware root of trust TPM 2.0 or higher
TPM support enabled by default
Virtualization-based security (VBS) enabled
Defend against firmware attack Windows Defender System guard enabled
Defend against vulnerable and malicious drivers Hypervisor-protected code integrity (HVCI) enabled
Defend against unverified code execution Arbitrary code generation and control flow hijacking protection [CFG, xFG, CET, ACG, CIG, KDP] enabled
Defend against limited physical access, data attacks Kernel DMA protection enabled
Protect identities and secrets from external threats Credential Guard enabled
However, users of other devices can also take advantage of similar protection if they configure their hardware and Windows security features correctly.
"Specifically, the following features need to be enabled: Secure boot, HVCI (enables VBS), KDP (automatically turned on when VBS is on), KDMA (Thunderbolt only) and Windows Defender System Guard," Microsoft explains.
"With Secured-core PCs, however, customers get a seamless chip to cloud security pattern that starts from a strong hardware root of trust and works with cloud services and Microsoft Defender ATP to aggregate and normalize the alerts from hardware elements to provide end-to-end endpoint security."




