
By
Jason Cipriani | March 6, 2020 -- 13:00 GMT (13:00 GMT) | Topic:
Coronavirus: Business and technology in a pandemicWhether you've been working from home for years, or are just getting started, it's not as easy and fun as you one might think. There are mental hurdles to overcome, including the feeling of isolation, especially if the only voice you've heard all day long is yours as you talk to your dog or cat.
Sure, the idea of rolling out of bed and going to work in your pajamas sounds like a
dream come true. But in reality, it does more harm than good to your mental health. We asked ZDNet's team of remote workers from all over the world for their best advice when it comes to working from home. From setting a daily routine to desk setups and ensuring you take care of yourself, here's what they had to say.
Daily routine
How and when you start each workday is a crucial piece of the puzzle to ensuring you're productive and comfortable when working from home. It's important to treat each workday like a day in the office, but there's more to it than that.
1. Organize your days with recurring tasks. Example: On Mondays, do X, Tuesdays do Y, Wednesdays do Z, etc.
2. Get dressed in the morning as though you are going to an actual office. Working in your bathrobe for "just an hour or two" is a slippery slope.
3. Don't schedule conference calls back-to-back. At some point, you'll forget who you're talking to and say something unusually silly.
4. Do schedule breaks.
5. Make a task list and be prepared to change your priorities at the drop of a hat. Because you're at home, you're in a fluid environment. You may need to move to another room, change the hours you're working because the fridge decided to flood, or other events. Having a list allows you to switch up and remain productive, regardless of events.
6. Find a hybrid arrangement where you're in the office (or a co-working space) for actual face time if possible.
7. Having different work spots for different parts of the day, for specific tasks or based on your mood.
8. Put your phone on airplane mode when working on a project or a deadline. This allows you to stay focused on the task at hand and not get distracted.
9. Create a healthy routine that involves a proper breakfast, lunch, and dinner.
10. Turn off email and social media at a set time and avoid taking your smartphone to bed.
11. Get a reasonable number of hours of sleep each night.
12. Coffee. Lots of it.
13. Don't bring food to your desk; just drinks. Once you bring food to your desk, it's a slippery slope to the bag of Reese's miniatures.
Equipment and work environment
Using the right equipment -- be it a chair, desk, keyboard or monitor -- can help have a big impact on how your back feels at the end of the day. And, as you'll quickly see, working at the kitchen table is a big no-no.
14. Use an ergonomic (
Kinesis) keyboard, a big 4K screen, and a proper office chair.
15. Flexible monitor arms, touchscreens, wireless keyboards & mouse are your friends.
16.
Adjustable chairs and stand up desks help with comfort and ergonomics.
17. Don't use a laptop on the kitchen table -- or any table or desk, for that matter.
18. If you find the classic desk arrangement quite limiting, know you don't have to stick to it. Keep ergonomics in mind, and switch between positions often. It helps your mind and body.
19. If you have a laptop, connect it to a keyboard, mouse, and monitor for a more formal desktop experience. But do your research before making any purchases.
20. When possible, having a dedicated office space with a door that can be closed is essential.
21. Set boundaries. Be it kids, your partner, or your roommate. Just because you work from home doesn't mean you're always available to run errands, watch a sick kid, or wait for the electrician.
22. Think outside the box if you have a baby or a puppy to take care of. Adjust your work environment so you are comfortable and can focus, while still being able to take care of a sick kid, or yourself.
23. Connect your computer to the big screen TV when needed. It serves as a great conferencing tool, even if you're just working out details on a home project with the family. Plus YouTube is much nicer at 65 inches.
24. Don't work in the kitchen.
25. Run Ethernet everywhere you can. When on a deadline or a push or moving big videos, you don't want to rely solely on Wi-Fi.
26. Get as much bandwidth as you can afford, both up and down.
27. Set up a local NAS for shared files and backups. But also be sure to back up to the cloud. Make sure you back up.
28. If you're going to do videos, make sure you have space where light doesn't cause issues, where you can have quiet, where the sound doesn't reverb, and where you don't have confidential stuff on the whiteboard behind your head.
29. Continually optimize and re-think your work environment.
30. Don't be afraid to invest in a good chair and a large monitor. Both will more than pay for themselves in reduced pain and increased productivity.
Also:
Best office chairs for 2020: Herman Miller, Secretlab, La-Z-Boy, Steelcase, and others 31. Know what local coffee shops and restaurants have good Wi-Fi. Have a VPN for those days. If you need to escape the chaos at home, you'll have a known bolt-location (this is also important if your local network connection goes out).
32. Also, know coffee shops a half hour or more away with Wi-Fi. If your local ISP is down and you're on a deadline, you'll want to know where to drive that has Wi-Fi and bandwidth at a more remote location.
33. Invest in sound-blocking earplugs or earmuffs. They'll save your butt on days where the chaos is too insane and you need quiet to concentrate.
Best wireless noise-canceling headsets for business in 2020: Plantronics, Jabra, Logitech, and more Work from home: Essential gadgets and gear for productivity and good healthApps and services
Use apps that allow you to efficiently communicate, but don't get carried away by interacting with coworkers or clients at all hours of the day. That said, you can use apps like video conferencing tools or Slack and Discord to interact with people outside of work.
34. Zoom, the video conferencing service, is your friend.
35. Consistently using
video conferencing tools will ensure you get up and get dressed each day.
Also:
Best video conferencing software for business in 2020: Zoom, WebEx, AnyMeeting, Slack, and more 36. Use apps like Evernote to manage your workload, organize ideas and just keep on top of things.
37. Avoid constantly checking email and social media, and turn off all the unnecessary notifications on your phone to avoid interruptions.
38. If you
move between computers throughout the workday, keep things in sync with services like Dropbox, iCloud, OneDrive, and other cloud storage services. That way whatever you're working on is available everywhere.
39. Use apps in full-screen mode as much as possible to limit distractions.
40. Join Slack channels or Discord servers with friends or groups with similar interests so you can interact with other people.
Mental health
Maintaining your mental health is the most important aspect of working from home. You miss out on the impromptu encounters and conversations, which, at first glance, feel superficial, but after you've been working in your home office for a few weeks, you'll be longing for any human interaction.
41. Getting out of the home/office during the workday is essential for sanity.
42. Shovel snow, walk down the street, connect with nature or go talk to your cat.
43.
Adopt a dog and take it for walks a couple of times a day. Cats may traditionally be a writer's best friend, but for getting up and moving you can't beat a pup.
44. Build time in your schedule to go to the gym when it's less crowded. It improves your well-being while placing you around people. And while you're at the gym, get on a bike, sweat and read fiction. There's nothing like getting into another world to improve your sanity.
45. Again, set boundaries. One of the biggest challenges, especially for those with a family, is family members thinking that working from home means you are always available for a phone call or errand. Communicate your schedule, and if needed, create "do not disturb days and hours."
46. Work outside. It's astonishing how a little fresh air can improve the mind's functioning.
47. Avoid guilt. Taking a break at home is way harder than walking out of the office and going around the block.
48. Have a designated workspace and office (preferably away from the kitchen).
49. Get out of the house after work or you get a little salty, bonkers, or feel isolated.
50. Get creative and experiment to build your perfect workplace.
51. Use headspace apps, white noise machines, or audiobooks to help you sleep.
52. Leave your smartphone charging in the living room at night, and if you use it to listen to music or podcasts, connect it to a Bluetooth speaker in your bedroom.
53. Do things you enjoy -- start a new hobby, join a club, etc. Something to get you out of the house regularly.
Taking care of your eyes, back, and overall physical health is just as important as mental health. A lot of these tips overlap with the equipment and work environment section above.
54. For five to 10 minutes every hour: Get up, move around and take your eyes off the screen.
55. Eat healthily! Don't rely on microwave meals and delivery orders.
56.
Don't work on a laptop. In the long run, it will probably cripple you, and the cost of physiotherapy soon adds up to more than the cost of ergonomic equipment.
57. You can do some work on a laptop, but using a laptop on a kitchen table for sustained periods is a bad idea. You might get by if you take regular screen breaks, but if you're under deadline pressure, wh does?
Tips for managers
Not only do employees have to learn how to work from home and remain efficient, but managers also have to learn how to effectively lead and manage remote workers. Below are suggestions from ZDNet's editor-in-chief, Larry Dignan:
58. Hire well.
59. Remote work works best when there are deliverables and deadlines.
60. Communicate well.
61. Don't micromanage.
62. Use the flexibility remote work gives you to your competitive advantage.
63. Utilize chat and video platforms.
64. Video conferencing office hours may be interesting. Try out open office hours via Zoom so people could just drop in.
The biggest takeaway here is that there isn't a one-size-fits-all solution. There are some core ideas, such as taking breaks, getting out of the house, and ensuring your office is conducive to allowing you to be productive. But outside of that, keep an open mind and experiment with different approaches. Perhaps most importantly -- don't be afraid to switch things up!
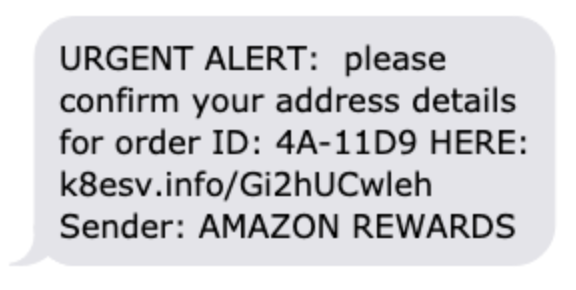
 Όταν μιλάμε για hacking επιθέσεις και παραβιάσεις συσκευών, ένα από τα πρώτα πράγματα που μας έρχονται στο μυαλό είναι τα passwords. Οι εδικοί ασφαλείας λένε συνέχεια ότι δεν πρέπει να χρησιμοποιούμε μικρούς, εύκολους και προβλέψιμους (ή και προεπιλεγμένους) κωδικούς. Το σπάσιμο των passwords είναι το πρώτο πράγμα που δοκιμάζουν οι hackers, όταν προσπαθούν να αποκτήσουν πρόσβαση σε μια συσκευή ή σύστημα.
Όταν μιλάμε για hacking επιθέσεις και παραβιάσεις συσκευών, ένα από τα πρώτα πράγματα που μας έρχονται στο μυαλό είναι τα passwords. Οι εδικοί ασφαλείας λένε συνέχεια ότι δεν πρέπει να χρησιμοποιούμε μικρούς, εύκολους και προβλέψιμους (ή και προεπιλεγμένους) κωδικούς. Το σπάσιμο των passwords είναι το πρώτο πράγμα που δοκιμάζουν οι hackers, όταν προσπαθούν να αποκτήσουν πρόσβαση σε μια συσκευή ή σύστημα.








.png)



