 SCAMS
SCAMSCoronavirus scams, found and explained
Posted: March 20, 2020 by
David RuizLast updated: March 19, 2020
Coronavirus has changed the face of the world, restricting countless individuals from dining at restaurants, working from cafes, and visiting their loved ones. But for cybercriminals, this global pandemic is expanding their horizons.
In the past week, Malwarebytes discovered multiple email scams that prey on the fear, uncertainty, and confusion regarding COVID-19, the illness caused by the novel coronavirus. With no vaccine yet developed, and with much of the world undergoing intense social distancing measures and near-total lockdown procedures, threat actors are flooding cyberspace with emailed promises of health tips, protective diets, and, most dangerously, cures. Attached to threat actors’ emails are a variety of fraudulent e-books, informational packets, and missed invoices that hide a series of keyloggers, ransomware, and data stealers.
The problem expands beyond pure
phishing scams.
On March 14, Twitter user @dustyfresh
published a web tracker that found
3,600 coronavirus- and COVID-19-related hostnames that sprung up in just 24 hours.
On March 17, security researcher and python developer @sshell_ built a tool,
hosted by the team at ThugCrowd, that provides real-time scans for potentially malicious, coronavirus-related domains.
Just click the link and watch possible scam sites get registered every minute.
Further, RiskIQ reportedly tracked more than 13,000 suspicious, coronavirus-related domains last weekend,
and more than 35,000 domains the next day, too.
Much of these numbers mean nothing without real, useful examples, though. Yes, coronavirus scams and scam sites are out there, but what do they look like, and how do they work? We’re here to explain.
Here are some of the many email scams that Malwarebytes spotted in the wild, with full details on what they say, what they’re lying about, and what types of malware they’re trying to install on your machines. The good news?
Malwarebytes protects against every threat described.
Impersonating the World Health Organization
Earlier this week,
we found an email phishing campaign sent by threat actors impersonating the World Health Organization (WHO), one of the
premier scientific resources on COVID-19. That campaign, which pushed a fake e-book to victims, delivered malicious code for a downloader called GuLoader. That download is just the first step in a more complex scheme.

As we wrote:
“GuLoader is used to load the real payload, an
information-stealing Trojan called FormBook, stored in encoded format on Google Drive.
Formbook is one of the most popular info-stealers, thanks to its simplicity and its wide range of capabilities, including swiping content from the Windows clipboard, keylogging, and stealing browser data. Stolen data is sent back to a command and control server maintained by the threat actors.”
Unfortunately, this GuLoader scam is just one of many in which threat actors posed as WHO professionals as a way to trick victims into downloading malicious attachments.
On March 18, we uncovered an email campaign that pushed victims into unwittingly downloading an invasive keylogger called Agent Tesla. The keylogger, which experienced a reported
100 percent increase in activity across three months in 2018, can steal a variety of sensitive data.
As cybersecurity researchers at LastLine wrote: “Acting as a fully-functional information stealer, [Agent Tesla] is capable of extracting credentials from different browsers, mail, and FTP clients. It logs keys and clipboards data, captures screen and video, and performs form-grabbing (Instagram, Twitter, Gmail, Facebook, etc.) attacks.”
The Agent Tesla campaign that we tracked on Wednesday involved an email with the subject line: Covid19″ Latest Tips to stay Immune to Virus !!
The email came to individuals’ inboxes allegedly from the WHO, with a sender email address of “sarah@who.com.” Notice that the sender’s email address ends with “.com” when legitimate WHO email addresses instead end with “.int.”

The email alleges to include a PDF file about “various diets and tips to keep us safe from being effected with the virus.” It is signed by a “Dr. Sarah Hopkins,” a supposed media relations consultant for the WHO.
A quick online search reveals that the WHO has a
public website for contacting its media relations representatives, and that none of those representatives is named Sarah Hopkins. Also, note how “Dr. Hopkins” has a phone number that doesn’t work, at +1 470 59828. Calling the number from a US-based phone resulted in an error message from the mobile service provider.
Interestingly, the above scam is just one example of an email campaign that both impersonates the WHO and attempts to deliver Agent Tesla.
On the same day we found the above-mentioned Agent Tesla scam, we
found another that mirrored its tactics and payload.
The second Agent Tesla scam arrives in individuals’ inbox with the email subject line “World Health Organization/Let’s fight Corona Virus together”
Already, savvy readers should spot a flaw. The unnecessary space placed between the words “Corona” and “Virus” mirrors a similar grammatical error, an unnecessary hyphen, in the GuLoader scam we covered on Malwarebytes Labs this week.

The entire body of the email reads, in verbatim:
We realise that the spread of the COVID-19 coronavirus may leave you feeling concerned, so we want to take a moment to reassure you that your safety and well-being remains our absolutely top priority.
Please be assured that our teams are working hard and we are monitoring the situation and developments closely with the health and governmental authorities of all countries we operate in. See attached WHO vital information to stay healthy.
we personally thank you for your understanding and assure you that we will do our utmost to limit disruptions this event brings to your travel plans while keeping your well-being our top priority.
This campaign attempts to trick victims into downloading a fake informational packet on coronavirus, with the file title “COVID-19 WHO RECOMMENDED V.gz.” Instead of trustworthy information, victims are infected with Agent Tesla.
While this campaign does not include as many smoke-and-mirror tactics, such as a fake media representative and a fake phone number, it can still do serious damage simply by stoking the fears surrounding COVID-19.
Finally, we found a possible WHO impersonator pushing the NetWire
Remote Access Trojan (RAT). RATS can allow hackers to gain unauthorized access to a machine from a remote location.
As we explain in our Threat Center profile on RATs, these types of Trojan can have devastating effects:
If Remote Access Trojan programs are found on a system, it should be assumed that any personal information (which has been accessed on the infected machine) has been compromised. Users should immediately update all usernames and passwords from a clean computer, and notify the appropriate system administrator of the potential compromise. Monitor credit reports and bank statements carefully over the following months to spot any suspicious activity on financial accounts.
The NetWire campaign included a slapdash combo of a strange email address, an official-looking WHO logo inside the email’s body, and plenty of typos.

Sent from “Dr. Stella Chungong” using the email address “brennan@caesars.com,” the email subject line is “SAFETY COVID-19 (Coronavirus Virus) AWARENESS – Safety Measures.” The body of the text reads:
To whom it may concern,
Go through the attac=ed document on safety measures regarding the spreading of Corona-virus.
Common symptoms include fever, cough, shortness in breath, and breathi=g difficulties.
Regards.
Dr. Stella Chungong
Specialist whuan=virus-advisory
The litany of misplaced “=” characters should immediately raise red flags for potential victims. These common mistakes show up in a wide variety of malicious email campaigns, as threat actors seem to operate under the mindset of “Send first, spellcheck later.”
Other malspam campaigns
Most of the coronavirus scams we spotted online are examples of
malspam—malicious spam email campaigns that cross the line from phony, snake-oil salesmanship into downright nefarious malware delivery.
Here are a number of malspam campaigns that our threat intelligence team found since March 15.
First up is this strange email titled “RE: Due to outbreak ofCoronavirus,” which arrives to users’ inboxes from the vague sender “Marketing,” with an email address of “info@bcsl.co.ke.” A Google search reveals that bcsl.co.ke appears to point to Boresha Credit Service Limited, a debt collector based in Kenya.

The short email reads:
Hello,
We have been instructed by your customer to make this transfer to you.
we are unable to process your payment as the SWIFT CODE in your bank account information is wrong,
please see that enclosed invoice and correct SWIFT CODE so we can remit payment ASAP before bank close.”
Again, scrutinizing the details of the email reveals holes in its authenticity.
The email is signed by “Rafhana Khan,” a supposed “Admin Executive” from the United Arab Emirates. The email sender includes this extra bit of info that leads us nowhere: TRN No. 100269864300003.
What is a TRN, and why would it be included? At best, we can assume this is the individual’s “tax registration number,” but think about the last time anyone signed an email with the US equivalent—their tax identification number. You’ve probably never seen that before, right? That’s because tax IDs are meant to be private, and not shared in email signatures. We can assume that the threat actors included this bogus bit of info to add some imaginary credibility. Really, it’s just nonsense.
The email’s attached invoice, once again, pushes GuLoader to the potential victim.
Another spotted malspam example pushes neither GuLoader or Agent Telsa. Instead, it tries to
trick users into downloading a malware called HawkEye, a credential stealer that has plagued users since at least 2013.
According to the cybersecurity news outlet
Security Affairs, HawkEye “is offered for sale on various hacking forums as a keylogger and stealer, [and] it allows to monitor systems and exfiltrate information.”
The HawkEye scam comes packaged in an email with the subject line “CORONA VIRUS CURE FOR CHINA,ITALY” from the alleged sender “DR JINS (CORONA VIRUS).” Again, potential victims receive a short message. The entire email body reads:
Dear Sir/Ma,
Kindly read the attached file for your quick remedy on CORONA VIRUS.
The email sender lists their place of work as the non-existent, misspelled RESEARCH HOSPITAL ISREAL at the address NO 29 JERUSALEM STREET, P.O.C 80067, ISREAL.

On March 15, we also found an email scam targeting victims in the UK and pushing, yet again, GuLoader. This time, threat actors promised updated statistics on the number of confirmed coronavirus cases in the United Kingdom.
The malicious email comes from the sender “PHE” with the email address paris@mfa.go.ke, which, like one of the examples above, appears to come from Kenya.

Because threat actors have one, overplayed tactic in these types of campaigns—putting in low effort—the content of the email is simple and short. The email reads:
Latest figures from public health authorities on the spread of Covid-19 in the United Kingdom.
Find out how many cases have been reported near you.
There is no email signature, and not even a greeting. Talk about a lack of email etiquette.
Finally, we found another campaign on March 18 that
targets Spanish-speaking victims in Spain. The email, titled “Vacuna COVID-19: prepare la vacuna en casa para usted y su familia para evitar COVID-19,” pushes GuLoader.

The email is signed by “Adriana Erico,” who offers no phone number, but does offer a fax number at 93 784 50 17. Unlike the fake phone number we tested above, we could not test the authenticity of this fax number, because the Bay Area is under a shelter-in-place order, and, truthfully, I don’t own a fax machine in my home.
Protect yourself
Threat actors are always looking for
the next crisis to leverage for their own attacks. For them, coronavirus presents a near-perfect storm. Legitimate confusion about accurate confirmed cases, testing availability, and best practices during social distancing makes for a fearful public, hungry for answers anywhere.
Like we said the
last time we looked at COVID-19 scams, the best places for information remain the WHO and the US Centers for Disease Control and Prevention (CDC).
You can find updated statistics about confirmed COVID-19 cases from the
WHO’s daily, situation reports here.
You can also find information on coronavirus myths at the WHO’s
Myth Busters webpage, along with its
Q&A page.
To help prevent the spread of the illness, remember, wash your hands for at least 20 seconds, refrain from touching your face, and practice social distancing by maintaining a distance of six feet from people not in your household.
This is difficult, this is new, and for many of us, it presents a life-altering shift. It’s important to consider that, right now, banding together as a global community is our best shot at beating this. That advice extends to the online world, too.
While coronavirus might have brought out the worst in cybercriminals, it’s also bringing out the best across the Internet. This week, a supposed “Covid19 Tracker App”
infected countless users’ phones with ransomware, demanding victims pay $100 to unlock their devices or risk a complete deletion of their contacts, videos, and pictures. After news about the ransomware was posted on Reddit, a user decompiled the malicious app
and posted the universal passcode to defeat the ransomware. The passcode was then
shared on Twitter for everyone to use.
Stay safe, everyone.
/cdn.vox-cdn.com/uploads/chorus_image/image/66566645/1212262073.jpg.0.jpg) Photo by Andrew Lichtenstein/Corbis via Getty Images
Photo by Andrew Lichtenstein/Corbis via Getty Images:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/19854779/Screen_Shot_2020_03_27_at_11.00.36_AM3_27.png)
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/19854787/Screen_Shot_2020_03_27_at_11.02.12_AM3_27.png)
/cdn.vox-cdn.com/uploads/chorus_image/image/66566645/1212262073.jpg.0.jpg) Photo by Andrew Lichtenstein/Corbis via Getty Images
Photo by Andrew Lichtenstein/Corbis via Getty Images:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/19854779/Screen_Shot_2020_03_27_at_11.00.36_AM3_27.png)
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/19854787/Screen_Shot_2020_03_27_at_11.02.12_AM3_27.png)


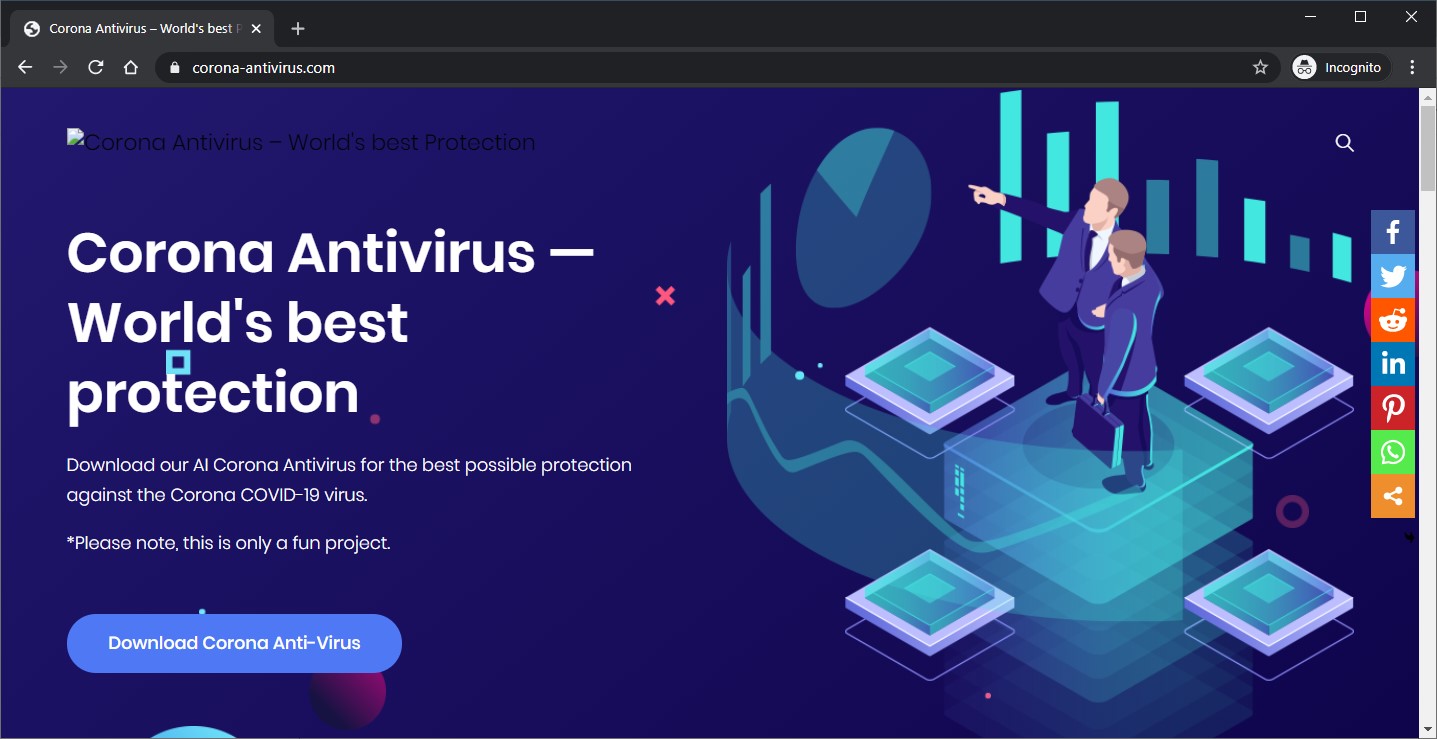
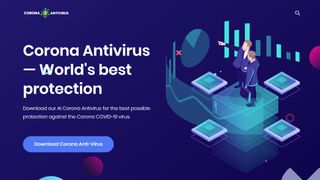 (Image credit: Malwarebytes)
(Image credit: Malwarebytes)
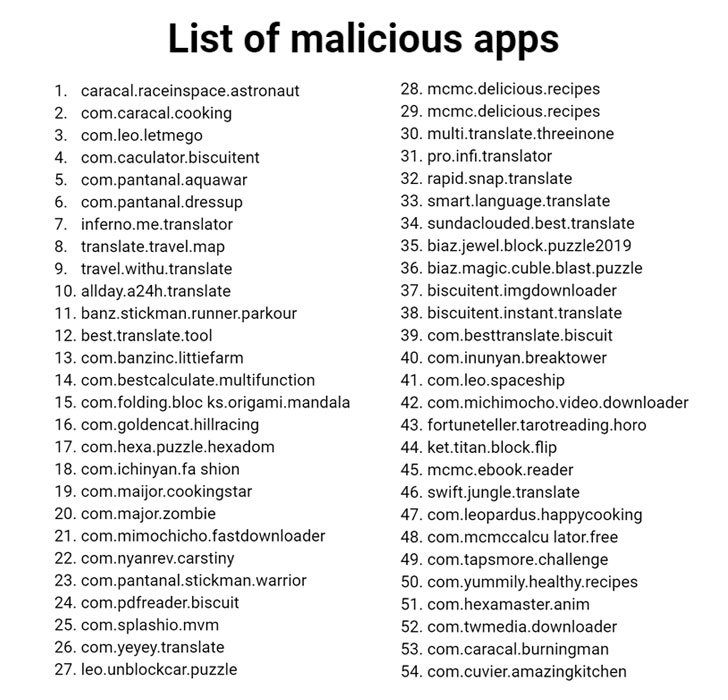






 BlackNET command panel
BlackNET command panel








