"Corona antivirus" infects victims with malware
By Anthony Spadafora 2 days ago
New site claims its antivirus software can protect users from getting the coronavirus
 (Image credit: Malwarebytes)
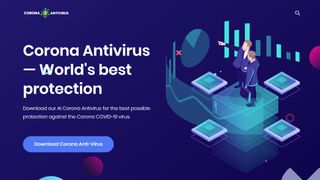
(Image credit: Malwarebytes)Cybercriminals continue to leverage the ongoing coronavirus outbreak for their own gain by launching numerous scam campaigns which use Covid-19 as a lure to trick users into installing a variety of malware and data stealers.
In the latest scam, discovered by Malwarebytes, cybercriminals have set up a website advertising “Corona Antivirus - World's best protection” which tries to trick users into installing antivirus software that supposedly has the capabilities to protect users from becoming infected with the virus in real life. The creators of the site have even provided more details on how their solution works, saying:
“Our scientists from Harvard University have been working on a special AI development to combat the virus using a windows app. Your PC actively protects you against the Coronaviruses (Cov) while the app is running.”
Beware these new coronavirus email scams
Malware strains using coronavirus to avoid detection
Phones from US government came packed with Chinese malware
While most users will likely understand that there is no way for any type of software to protect them from becoming infected with the coronavirus, there is a possibility that some will fall for this scheme as the cybercriminals behind it have taken the necessary steps to make their website appear legitimate.
BlackNET RAT
Once a user installs the application available on the Corona Antivirus site, their computer will be infected with malware. The installation file, which contains the commercial packer Themida, will turn a user's PC into a bot ready to receive commands.
After inspecting the command and control server, Malwarebytes discovered a control panel for the BlackNET botnet. The full source code for the BlackNET toolkit was published on GitHub a month ago and some of its features include deploying DDoS attacks, taking screenshots, stealing Firefox cookies, stealing saved passwords, implementing a keylogger, executing scripts and stealing Bitcoin wallets, among others.
While working from home, it is important that all users keep their computers up to date and exercise caution when downloading and installing new programs to avoid falling victim to the many coronavirus-themed scams that are currently making their way around the web.
After investigating the Corona Antivirus site, Malwarebytes informed CloudFlare of its discovery and the CDN took immediate action to flag the website as a malicious.
No comments:
Post a Comment