AWARENESSThe effects of climate change on cybersecurity
Posted: March 13, 2020 by
Pieter ArntzOutside the
coronavirus pandemic and its related healthcare and economic fallout, climate change and cybersecurity are seen by many as the two most urgent problems facing our planet now and in the near future. They are two distinct and separate problems, to be sure. There are some areas, however, where security and climate change overlap, interlock, and influence one another. Let’s have a look.
To understand how climate change and the methods to counteract its rapid ascent will affect cybersecurity, we first have to look at how computing contributes to global warming. Your first instinct about their relationship is probably right: computing involves energy consumption and heat production. As long as we cannot produce enough “clean energy” to satisfy our needs for electricity, the energy consumed by computing—and security within it—will continue to contribute to global warming.
The big energy consumers
There are a few fields in computing and cybersecurity that guzzle up huge amounts of energy and produce heat as a byproduct:
Supercomputers
Blockchain mining
Data centers
The Internet as a whole
Before you dismiss the problem of the supercomputers (because you assume there are only a few of them)—even I was astounded to find out that there are over
500 systems that deliver a petaflop or more on the High Performance Linpack (HPL) benchmark. Most of these supercomputers consume vast amounts of electrical power and produce so much heat that large cooling facilities must be constructed to ensure proper performance. But in recent years, vendors have started to produce
supercomputers that are more energy efficient.
In 2019, the mining of
Bitcoin alone consumed more energy than the entire nation of Switzerland, which equals about one quarter percent of the world’s entire energy consumption. There are many more blockchains and cryptocurrencies, although Bitcoin is by far the largest energy consumer among them. This is mostly due to their operation on the
proof-of-work concept and the high value of Bitcoin.
While cybercrime experienced a huge jolt in
cryptomining in 2018, the frenzy has mostly died down as Bitcoin value dipped and plateaued. However, cryptomining continues as both a legitimate and illegitimate activity—especially because miners can switch to other cryptocurrencies when Bitcoin drops off.
An even bigger impact on energy consumption are data centers, which
already use over 2 percent of the world’s total energy consumption, and that number is expected to rise fast. The prediction is based on the growing number of content delivery networks (CDN), more Internet of Things (IoT) devices, the growth of the
cloud, and other colocation services. So, not only do computer centers consume massive amounts of energy, their use is expected to grow astronomically.
The Internet can’t be completely separated from the data centers that enable it. But despite the overlap, it’s still worth mentioning that the total
energy consumption of the Internet as a whole lies at around 10 percent, which is more than the world’s total energy production from renewable sources such as wind and solar.
However, it’s fair to note that the Internet has taken over a lot of tasks that would have cost more energy or created a greater carbon footprint if they had been performed in the “old ways.” Consider, for example, the energy saved by
working remote: the energy expended on the Internet and inside one’s home is far less damaging than the carbon monoxide released into the atmosphere by fossil fuels from a daily commute to the office.
Global warming’s trickle down effects
Conversely, global warming and its effects on the climate, environment, and economy do have a direct impact on our everyday lives, and that trickles down to cybersecurity. Some of the projected dangers include:
Flooding of certain areas
Prolongation of the wild-fire season
Spread of diseases
Economic costs
Scarcity of fresh water in certain areas
By 2030, climate change costs are projected to cost the global economy $700 billion annually, according to the
Climate Vulnerability Monitor. And The International Organization for Migration estimates that
200 million people could be forced to leave their homes due to environmental changes by 2050.
Climate change and its implications will act as a destabilizing factor on society. When livelihoods are in danger, this will spark insecurity and drive resource competition. This does not only have implications for physical security, but in modern society, this also has an impact on cybersecurity and its associated threats.
From a big picture, worst-case-scenario perspective, climate change could trigger profound international conflicts, which go hand-in-hand with cyberwar. Beyond nation-state activity, individuals that have no other means of providing for their families could turn to cybercrime, which is often seen as a low-risk activity with a potentially high yield.
But on a smaller scale, we’re already seeing the impacts of climate change on cybersecurity, whether via social engineering scare tactics embraced by threat actors or disruptions to Internet-connected home heating and cooling devices meant to track energy consumption.
Global warming scams
NO, we’re not saying that climate change is a
hoax or a
scam. But we want to issue a warning related to the subject. As with any newsworthy topic, there are and will be scammers trying to make a profit using the feeling of urgency that gets invoked by matters like climate change.
For example, the Intergovernmental Panel on Climate Change (IPCC) issued a
warning against several scams abusing their name.
“IPCC has been made aware of various correspondences, being circulated via e-mail, from Internet Web sites, and via regular mail or facsimile, falsely stating that they are issued by, or in association with, IPCC and/or its officials. These scams, which may seek to obtain money and/or in many cases personal details from the recipients of such correspondence, are fraudulent.”
Natural disaster scams are increasing in the same frequency as natural disasters themselves, often claiming to be collecting donations for a particular cause but putting money in their own pockets instead. We’ve seen social engineering tricks ranging from phishing emails and malspam to social media misinformation campaigns on hurricanes, tornadoes, fires, and flooding. Expect this sort of gross capitalization on tragedy and fear to continue as the effects of climate change become more dramatic.
Improving efficiency and preparing for changes
The number of datacenters is down, but their size has grown to meet the demand. This is potentially a step in the right direction since it decreases the power needed for the overhead, but not as big as the step that could be made if they would actually work on their power efficiency.
Online companies typically run their facilities at maximum capacity around the clock, regardless of the demand. As a result, data centers are wasting 90 percent or more of their power. Smart management could make a substantial difference in energy consumption and costs.
Cryptomining could improve on energy consumption if the most popular currencies would not be based on proof of work but proof of stake. Proof of work rewards the largest number of CPU cycles with that the highest energy consumption.
NEO and Hyperledger are next generation blockchain technologies with much lower electricity cost. NEO uses what it calls delegated Byzantine Fault Tolerance (dBFT), which is an optimized proof-of-stake model. Hyperledger Fabric centralizes block creation into a single resource pool and has multiple validators in the participants. It’s an enterprise collaboration engine, using blockchain smart contracts, where validation is much easier than creation, and creation will be centralized on a single, optimized platform.
More effective methods of cooling would both help supercomputers and large data centers. At the moment, we are (ironically) using electricity to power cooling systems to control the heat caused by electricity usage. In fact, cooling gobbles up about 35 percent of the total power in high performance computing with air cooled systems.
Hot-water liquid cooling might be a key technology in future green supercomputers as it maximizes cooling efficiency and energy reuse.
Interaction between climate change and cybersecurity
As we have seen, there are opportunities for those in security and computing to slow the progression of climate change. But there are also opportunities for those in cybercrime to take advantage of the destabilization caused by climate change, as some already have through related scams and malware campaigns. As long as we don’t drop security in attempts to counteract global warming, we’ll be able to protect against some of the more advanced threats coming down the pike. But while we still can, let’s rein in our carbon footprint, improve on computing efficiency, and remember our cybersecurity lessons when criminals come calling.
Stay safe, everyone!




 Η Microsoft κυκλοφόρησε το
Η Microsoft κυκλοφόρησε το 









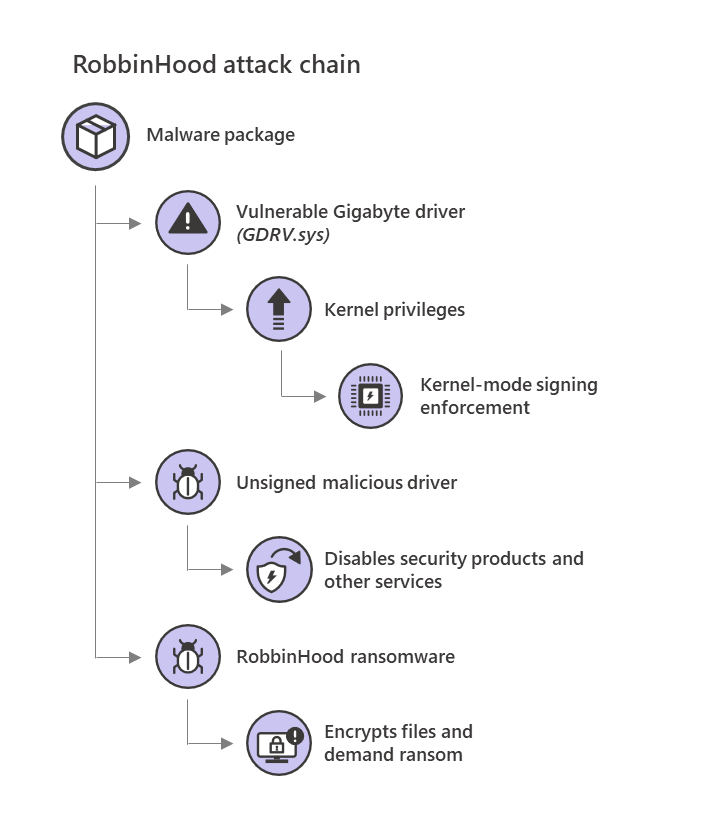 RobbinHood Ransomware attack chain (Microsoft)
RobbinHood Ransomware attack chain (Microsoft)




