Από Teo Ehc -18 Μαΐου 2020, 17:26
Η Microsoft έχει προσθέσει ένα ενσωματωμένο packet network sniffer στην ενημέρωση των Windows 10 Οκτωβρίου 2018 που έχει περάσει απαρατήρητο.
Ένα πακέτο sniffer, ή network sniffer, είναι ένα πρόγραμμα που παρακολουθεί τη δραστηριότητα δικτύου που ρέει πάνω από έναν υπολογιστή σε ένα επίπεδο πακέτου.
Αυτό μπορεί να χρησιμοποιηθεί από τους διαχειριστές δικτύου για τη διάγνωση ζητημάτων δικτύωσης, για να δείτε ποιοι τύποι προγραμμάτων χρησιμοποιούνται σε ένα δίκτυο ή ακόμα και για ακρόαση σε συνομιλίες δικτύου που αποστέλλονται μέσω καθαρού κειμένου.
Ενώ οι χρήστες Linux είχαν πάντα το εργαλείο tcpdump για να εκτελούν sniffing στο δίκτυο, οι χρήστες των Windows έπρεπε να εγκαταστήσουν προγράμματα τρίτων, όπως το Microsoft Network Monitor και το Wireshark.
Όλα αυτά άλλαξαν όταν η Microsoft κυκλοφόρησε την ενημέρωση του Οκτωβρίου 2018, καθώς τώρα τα Windows 10 έρχονται με ένα νέο πρόγραμμα “Packet Monitor” που ονομάζεται pktmon.exe.
Το ενσωματωμένο packet sniffer έρχεται στα Windows 10
Με την κυκλοφορία της ενημερωμένης έκδοσης των Windows 10 Οκτωβρίου 2018, η Microsoft πρόσθεσε ήσυχα ένα νέο πρόγραμμα διαγνωστικού δικτύου και παρακολούθησης πακέτων που ονομάζεται C: \ Windows \ system32 \ pktmon.exe.
Αυτό το πρόγραμμα έχει μια περιγραφή “Παρακολούθηση εσωτερικής διάδοσης πακέτων και αναφορών πακέτων πτώσης”, η οποία υποδεικνύει ότι έχει σχεδιαστεί για τη διάγνωση προβλημάτων δικτύου.
Παρόμοια με την εντολή «netsh trace» των Windows, μπορεί να χρησιμοποιηθεί για την πλήρη επιθεώρηση πακέτων των δεδομένων που αποστέλλονται μέσω του υπολογιστή.
Αυτό το πρόγραμμα δεν έχει καμία αναφορά στον ιστότοπο της Microsoft που θα μπορούσαμε να βρούμε και έπρεπε να μάθουμε πώς να το χρησιμοποιούμε παίζοντας με το πρόγραμμα.
Ευτυχώς περιλαμβάνει ένα αρκετά εκτεταμένο σύστημα βοήθειας που μπορεί να χρησιμοποιηθεί πληκτρολογώντας ‘pktmon [command] help’.
Για παράδειγμα, pktmon filter help, θα σας δώσει την οθόνη βοήθειας για την εντολή φίλτρου.
Για να μάθετε πώς να χρησιμοποιείτε το Pktmon, σας προτείνω να διαβάσετε την τεκμηρίωση βοήθειας και να “παίξετε” με το πρόγραμμα. Παρέχουμε επίσης ένα παράδειγμα στην επόμενη ενότητα για να σας βοηθήσουμε να ξεκινήσετε.
Χρήση του Pktmon για παρακολούθηση της κυκλοφορίας δικτύου
Δυστυχώς, η κατάδυση στο πλήρες σύνολο λειτουργιών του Pktmon δεν εμπίπτει στο πεδίο εφαρμογής αυτού του άρθρου, αλλά θέλαμε να σας δείξουμε ένα βασικό παράδειγμα για το πώς μπορείτε να χρησιμοποιήσετε το εργαλείο.
Για παράδειγμα, θα χρησιμοποιήσουμε το Pktmon για την παρακολούθηση της κίνησης FTP από τον υπολογιστή στον οποίο εκτελείται.
Για να γίνει αυτό, πρέπει πρώτα να ξεκινήσουμε μια γραμμή εντολών με αναβαθμισμένα Windows 10, καθώς το Pktmon απαιτεί δικαιώματα διαχειριστή.
Στη συνέχεια, πρέπει να δημιουργήσουμε δύο φίλτρα πακέτων που θα λένε στην Pktmon ποια κίνηση θα παρακολουθεί, η οποία στο παράδειγμά μας θα είναι η κίνηση στις θύρες TCP 20 και 21.
Αυτά τα φίλτρα μπορούν να δημιουργηθούν χρησιμοποιώντας το pktmon filter add -p [port] εντολή για κάθε θύρα που θέλουμε να παρακολουθούμε.
Στη συνέχεια, μπορείτε να χρησιμοποιήσετε το pktmon filter list εντολή για να δείτε τα φίλτρα πακέτων που μόλις δημιουργήσαμε.
Για να ξεκινήσουμε την παρακολούθηση για πακέτα που επικοινωνούν με τις θύρες TCP 20 και 21, πρέπει να χρησιμοποιήσουμε το pktmon start –etw εντολή.
Μόλις εκτελεστεί, το pktmon θα καταγράψει όλα τα πακέτα σε όλες τις διασυνδέσεις δικτύου στη συσκευή σε ένα αρχείο που ονομάζεται PktMon.etl και θα καταγράψει μόνο τα πρώτα 128 bytes ενός πακέτου.
Για να το καταγράψετε ολόκληρο το πακέτο και μόνο από μια συγκεκριμένη συσκευή ethernet, μπορείτε να χρησιμοποιήσετε τα ορίσματα -p 0 (capture ολόκληρο το πακέτο) και -c 13 (λήψη μόνο από τον προσαρμογέα με ID 13).
Για να προσδιορίσετε ποιο αναγνωριστικό είναι οι προσαρμογείς σας, μπορείτε να εκτελέσετε την εντολή pktmon comp list εντολή
Όταν συνδυάζουμε όλα τα επιχειρήματα, παίρνουμε μια τελική εντολή:

Το Pktmon θα τρέξει τώρα αθόρυβα ενώ καταγράφει όλα τα πακέτα που ταιριάζουν με τα εισερχόμενα φίλτρα μας.
Για να σταματήσετε τη λήψη πακέτων, εισαγάγετε το pktmon stop εντολή και ένα αρχείο καταγραφής που ονομάζεται PktMon.etl θα έχει δημιουργηθεί στον ίδιο φάκελο που περιέχει τα ανεπεξέργαστα δεδομένα.

Αυτά τα δεδομένα σε αυτό το αρχείο δεν μπορούν να χρησιμοποιηθούν άμεσα, οπότε πρέπει να το μετατρέψετε σε μορφή κειμένου που είναι αναγνώσιμη από τον άνθρωπο με την ακόλουθη εντολή:
Ακόμα και μετατροπή σε κείμενο, δεν πρόκειται να σας δώσει τα πλήρη πακέτα, αλλά μόνο μια περίληψη της κίνησης δικτύου, όπως φαίνεται παρακάτω.
Για να επωφεληθείτε από τα καταγεγραμμένα δεδομένα, σας προτείνω να κάνετε λήψη και εγκατάσταση του Microsoft Network Monitor και να το χρησιμοποιήσετε για να δείτε το αρχείο ETL.
Χρησιμοποιώντας το Network Monitor, μπορείτε να δείτε το πλήρες πακέτο που στάλθηκε, συμπεριλαμβανομένων οποιωνδήποτε πληροφοριών σαφούς κειμένου.
Για παράδειγμα, παρακάτω μπορείτε να δείτε ένα πακέτο που περιέχει τον κωδικό πρόσβασης σαφούς κειμένου που εισαγάγαμε κατά τη σύνδεση σε αυτόν τον ιστότοπο δοκιμών FTP.
Όταν ολοκληρώσετε τη χρήση του προγράμματος Pktmon, μπορείτε να καταργήσετε όλα τα δημιουργημένα φίλτρα χρησιμοποιώντας την εντολή:
Σύντομα, παρακολούθηση σε πραγματικό χρόνο και υποστήριξη pcapng
Με την επερχόμενη έκδοση της ενημέρωσης των Windows 10 Μαΐου 2020 (Windows 10 2004), η Microsoft ενημέρωσε το εργαλείο Pktmon για να σας επιτρέπει να εμφανίζετε πακέτα που παρακολουθούνται σε πραγματικό χρόνο και να μετατρέψετε αρχεία ETL σε μορφή PCAPNG.
Στην έκδοση του Pktmon που έρχεται στην επόμενη ενημέρωση δυνατοτήτων, μπορείτε να ενεργοποιήσετε την παρακολούθηση σε πραγματικό χρόνο χρησιμοποιώντας το -l real-time διαφωνία.
Αυτό θα προκαλέσει την εμφάνιση των πακέτων που έχουν “τραβηχτεί απευθείας” στην οθόνη, ενώ θα τα αποθηκεύετε επίσης στο αρχείο ETL.
Η Microsoft προσθέτει επίσης τη δυνατότητα μετατροπής αρχείων ETL σε μορφή PCAPNG, έτσι ώστε να μπορούν να χρησιμοποιηθούν σε προγράμματα όπως το Wireshark.
Μόλις το αρχείο μετατραπεί σε μορφή PCAPNG, μπορεί να ανοίξει στο Wireshark, ώστε να μπορείτε να δείτε καλύτερα την επικοινωνία δικτύου.
Για άλλη μια φορά, αυτές οι δυνατότητες δεν είναι διαθέσιμες στα Windows 10 1903/1909 και θα έρθουν στα Windows 10 2004 όταν κυκλοφορήσουν στο τέλος του μήνα.
Η Microsoft έχει προσθέσει ένα ενσωματωμένο packet network sniffer στην ενημέρωση των Windows 10 Οκτωβρίου 2018 που έχει περάσει απαρατήρητο.
Ένα πακέτο sniffer, ή network sniffer, είναι ένα πρόγραμμα που παρακολουθεί τη δραστηριότητα δικτύου που ρέει πάνω από έναν υπολογιστή σε ένα επίπεδο πακέτου.
Αυτό μπορεί να χρησιμοποιηθεί από τους διαχειριστές δικτύου για τη διάγνωση ζητημάτων δικτύωσης, για να δείτε ποιοι τύποι προγραμμάτων χρησιμοποιούνται σε ένα δίκτυο ή ακόμα και για ακρόαση σε συνομιλίες δικτύου που αποστέλλονται μέσω καθαρού κειμένου.
Ενώ οι χρήστες Linux είχαν πάντα το εργαλείο tcpdump για να εκτελούν sniffing στο δίκτυο, οι χρήστες των Windows έπρεπε να εγκαταστήσουν προγράμματα τρίτων, όπως το Microsoft Network Monitor και το Wireshark.
Όλα αυτά άλλαξαν όταν η Microsoft κυκλοφόρησε την ενημέρωση του Οκτωβρίου 2018, καθώς τώρα τα Windows 10 έρχονται με ένα νέο πρόγραμμα “Packet Monitor” που ονομάζεται pktmon.exe.

Το ενσωματωμένο packet sniffer έρχεται στα Windows 10
Με την κυκλοφορία της ενημερωμένης έκδοσης των Windows 10 Οκτωβρίου 2018, η Microsoft πρόσθεσε ήσυχα ένα νέο πρόγραμμα διαγνωστικού δικτύου και παρακολούθησης πακέτων που ονομάζεται C: \ Windows \ system32 \ pktmon.exe.
Αυτό το πρόγραμμα έχει μια περιγραφή “Παρακολούθηση εσωτερικής διάδοσης πακέτων και αναφορών πακέτων πτώσης”, η οποία υποδεικνύει ότι έχει σχεδιαστεί για τη διάγνωση προβλημάτων δικτύου.
Παρόμοια με την εντολή «netsh trace» των Windows, μπορεί να χρησιμοποιηθεί για την πλήρη επιθεώρηση πακέτων των δεδομένων που αποστέλλονται μέσω του υπολογιστή.

Αυτό το πρόγραμμα δεν έχει καμία αναφορά στον ιστότοπο της Microsoft που θα μπορούσαμε να βρούμε και έπρεπε να μάθουμε πώς να το χρησιμοποιούμε παίζοντας με το πρόγραμμα.
Ευτυχώς περιλαμβάνει ένα αρκετά εκτεταμένο σύστημα βοήθειας που μπορεί να χρησιμοποιηθεί πληκτρολογώντας ‘pktmon [command] help’.
Για παράδειγμα, pktmon filter help, θα σας δώσει την οθόνη βοήθειας για την εντολή φίλτρου.

Για να μάθετε πώς να χρησιμοποιείτε το Pktmon, σας προτείνω να διαβάσετε την τεκμηρίωση βοήθειας και να “παίξετε” με το πρόγραμμα. Παρέχουμε επίσης ένα παράδειγμα στην επόμενη ενότητα για να σας βοηθήσουμε να ξεκινήσετε.
Χρήση του Pktmon για παρακολούθηση της κυκλοφορίας δικτύου
Δυστυχώς, η κατάδυση στο πλήρες σύνολο λειτουργιών του Pktmon δεν εμπίπτει στο πεδίο εφαρμογής αυτού του άρθρου, αλλά θέλαμε να σας δείξουμε ένα βασικό παράδειγμα για το πώς μπορείτε να χρησιμοποιήσετε το εργαλείο.
Για παράδειγμα, θα χρησιμοποιήσουμε το Pktmon για την παρακολούθηση της κίνησης FTP από τον υπολογιστή στον οποίο εκτελείται.
Για να γίνει αυτό, πρέπει πρώτα να ξεκινήσουμε μια γραμμή εντολών με αναβαθμισμένα Windows 10, καθώς το Pktmon απαιτεί δικαιώματα διαχειριστή.
Στη συνέχεια, πρέπει να δημιουργήσουμε δύο φίλτρα πακέτων που θα λένε στην Pktmon ποια κίνηση θα παρακολουθεί, η οποία στο παράδειγμά μας θα είναι η κίνηση στις θύρες TCP 20 και 21.
Αυτά τα φίλτρα μπορούν να δημιουργηθούν χρησιμοποιώντας το pktmon filter add -p [port] εντολή για κάθε θύρα που θέλουμε να παρακολουθούμε.
Στη συνέχεια, μπορείτε να χρησιμοποιήσετε το pktmon filter list εντολή για να δείτε τα φίλτρα πακέτων που μόλις δημιουργήσαμε.

Για να ξεκινήσουμε την παρακολούθηση για πακέτα που επικοινωνούν με τις θύρες TCP 20 και 21, πρέπει να χρησιμοποιήσουμε το pktmon start –etw εντολή.
Μόλις εκτελεστεί, το pktmon θα καταγράψει όλα τα πακέτα σε όλες τις διασυνδέσεις δικτύου στη συσκευή σε ένα αρχείο που ονομάζεται PktMon.etl και θα καταγράψει μόνο τα πρώτα 128 bytes ενός πακέτου.
Για να το καταγράψετε ολόκληρο το πακέτο και μόνο από μια συγκεκριμένη συσκευή ethernet, μπορείτε να χρησιμοποιήσετε τα ορίσματα -p 0 (capture ολόκληρο το πακέτο) και -c 13 (λήψη μόνο από τον προσαρμογέα με ID 13).
Για να προσδιορίσετε ποιο αναγνωριστικό είναι οι προσαρμογείς σας, μπορείτε να εκτελέσετε την εντολή pktmon comp list εντολή
Όταν συνδυάζουμε όλα τα επιχειρήματα, παίρνουμε μια τελική εντολή:

Το Pktmon θα τρέξει τώρα αθόρυβα ενώ καταγράφει όλα τα πακέτα που ταιριάζουν με τα εισερχόμενα φίλτρα μας.
Για να σταματήσετε τη λήψη πακέτων, εισαγάγετε το pktmon stop εντολή και ένα αρχείο καταγραφής που ονομάζεται PktMon.etl θα έχει δημιουργηθεί στον ίδιο φάκελο που περιέχει τα ανεπεξέργαστα δεδομένα.
Αυτά τα δεδομένα σε αυτό το αρχείο δεν μπορούν να χρησιμοποιηθούν άμεσα, οπότε πρέπει να το μετατρέψετε σε μορφή κειμένου που είναι αναγνώσιμη από τον άνθρωπο με την ακόλουθη εντολή:
Ακόμα και μετατροπή σε κείμενο, δεν πρόκειται να σας δώσει τα πλήρη πακέτα, αλλά μόνο μια περίληψη της κίνησης δικτύου, όπως φαίνεται παρακάτω.

Για να επωφεληθείτε από τα καταγεγραμμένα δεδομένα, σας προτείνω να κάνετε λήψη και εγκατάσταση του Microsoft Network Monitor και να το χρησιμοποιήσετε για να δείτε το αρχείο ETL.
Χρησιμοποιώντας το Network Monitor, μπορείτε να δείτε το πλήρες πακέτο που στάλθηκε, συμπεριλαμβανομένων οποιωνδήποτε πληροφοριών σαφούς κειμένου.
Για παράδειγμα, παρακάτω μπορείτε να δείτε ένα πακέτο που περιέχει τον κωδικό πρόσβασης σαφούς κειμένου που εισαγάγαμε κατά τη σύνδεση σε αυτόν τον ιστότοπο δοκιμών FTP.

Όταν ολοκληρώσετε τη χρήση του προγράμματος Pktmon, μπορείτε να καταργήσετε όλα τα δημιουργημένα φίλτρα χρησιμοποιώντας την εντολή:
Σύντομα, παρακολούθηση σε πραγματικό χρόνο και υποστήριξη pcapng
Με την επερχόμενη έκδοση της ενημέρωσης των Windows 10 Μαΐου 2020 (Windows 10 2004), η Microsoft ενημέρωσε το εργαλείο Pktmon για να σας επιτρέπει να εμφανίζετε πακέτα που παρακολουθούνται σε πραγματικό χρόνο και να μετατρέψετε αρχεία ETL σε μορφή PCAPNG.
Στην έκδοση του Pktmon που έρχεται στην επόμενη ενημέρωση δυνατοτήτων, μπορείτε να ενεργοποιήσετε την παρακολούθηση σε πραγματικό χρόνο χρησιμοποιώντας το -l real-time διαφωνία.
Αυτό θα προκαλέσει την εμφάνιση των πακέτων που έχουν “τραβηχτεί απευθείας” στην οθόνη, ενώ θα τα αποθηκεύετε επίσης στο αρχείο ETL.

Η Microsoft προσθέτει επίσης τη δυνατότητα μετατροπής αρχείων ETL σε μορφή PCAPNG, έτσι ώστε να μπορούν να χρησιμοποιηθούν σε προγράμματα όπως το Wireshark.

Μόλις το αρχείο μετατραπεί σε μορφή PCAPNG, μπορεί να ανοίξει στο Wireshark, ώστε να μπορείτε να δείτε καλύτερα την επικοινωνία δικτύου.

Για άλλη μια φορά, αυτές οι δυνατότητες δεν είναι διαθέσιμες στα Windows 10 1903/1909 και θα έρθουν στα Windows 10 2004 όταν κυκλοφορήσουν στο τέλος του μήνα.


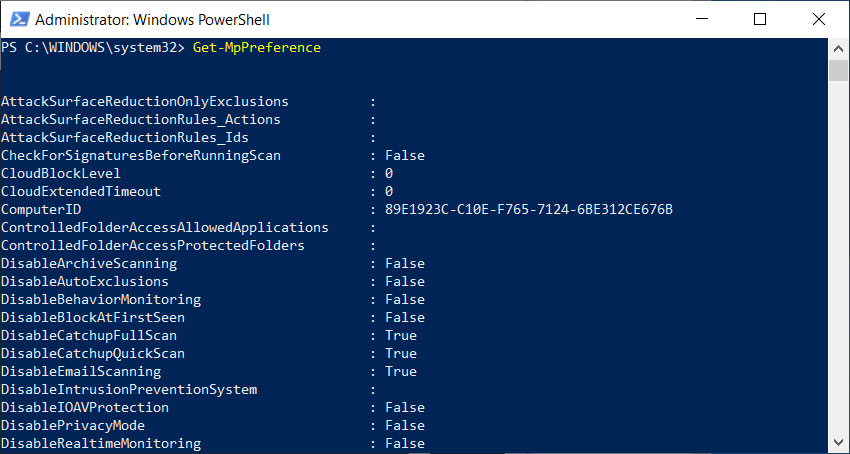 The output of the Get-MpPreference command
The output of the Get-MpPreference command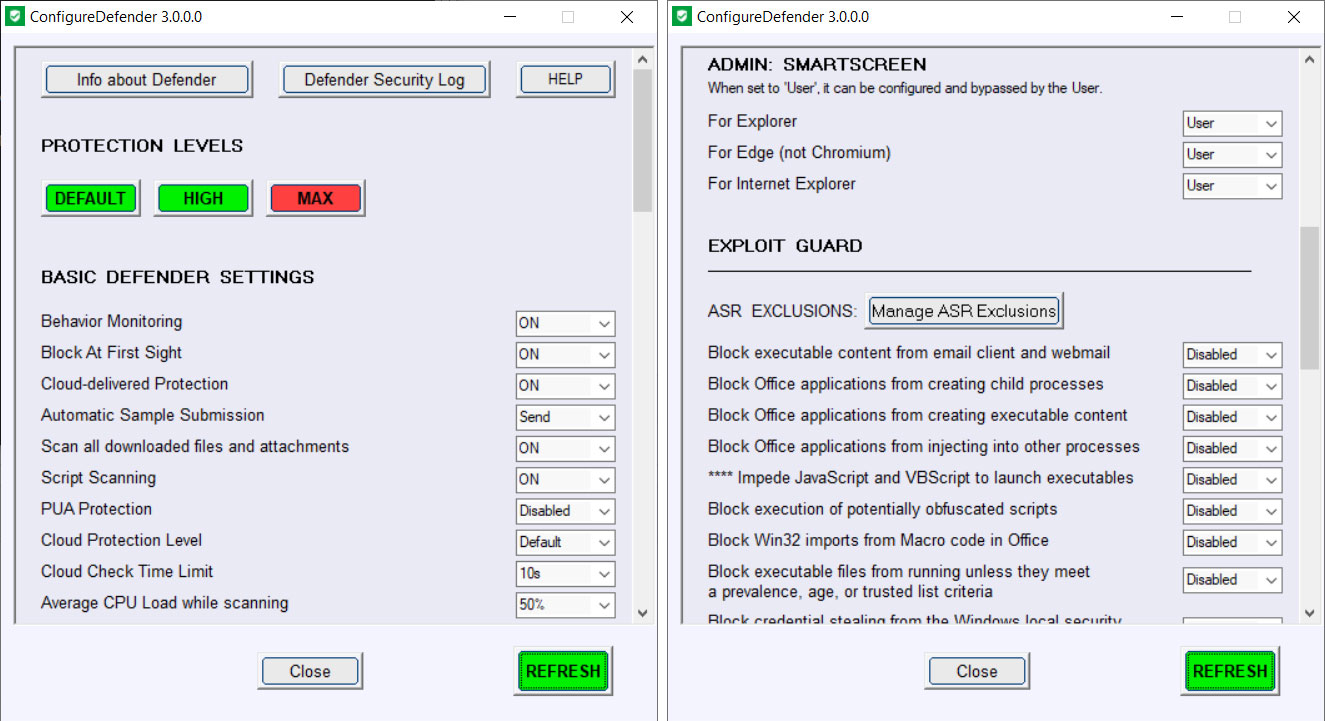 ConfigureDefender options
ConfigureDefender options






 Click to see a larger version
Click to see a larger version Weaponized attachment
Weaponized attachment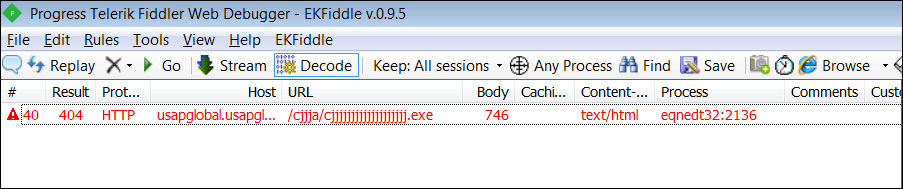 The vulnerability being exploited to download malware
The vulnerability being exploited to download malware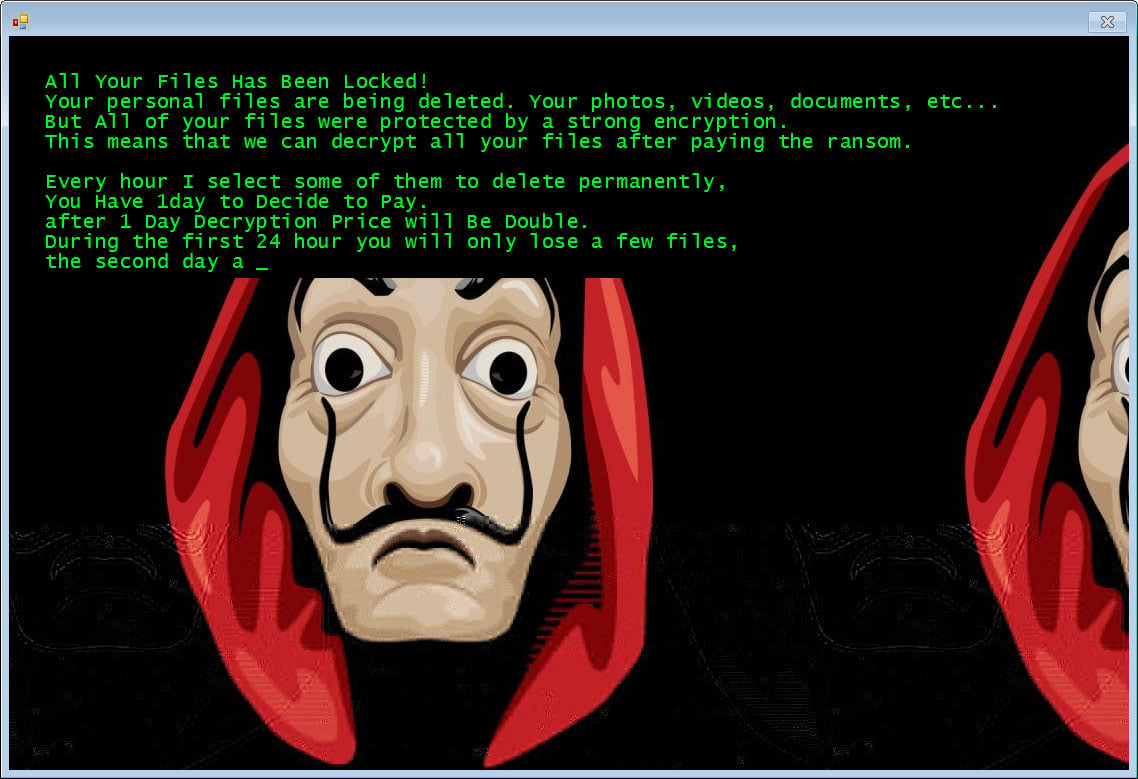 Jigsaw Ransomware
Jigsaw Ransomware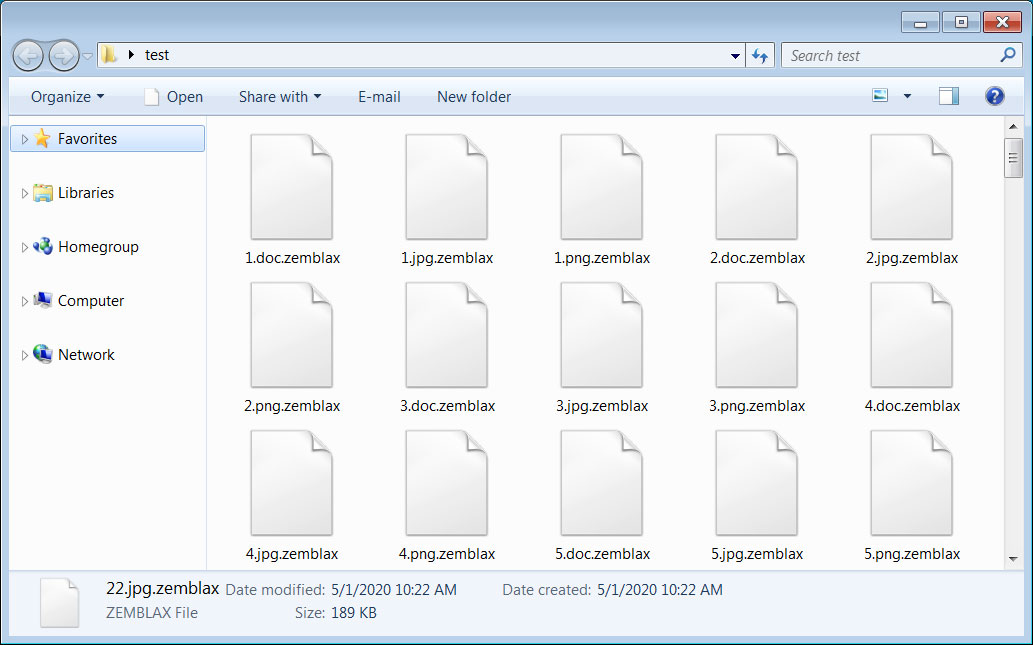 Encrypted Files
Encrypted Files
 READ MORE
READ MORE Apps targeted by EventBot (Cybereason Nocturnus)
Apps targeted by EventBot (Cybereason Nocturnus)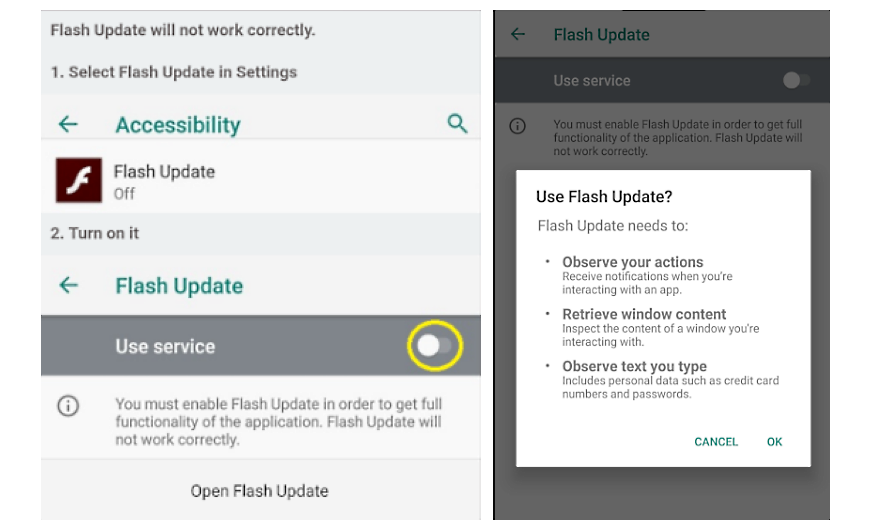 EventBot requesting permissions (Cybereason Nocturnus)
EventBot requesting permissions (Cybereason Nocturnus)
 Number of Malwarebytes detections of Ransom.Troldesh from July 2018 till April 2020
Number of Malwarebytes detections of Ransom.Troldesh from July 2018 till April 2020
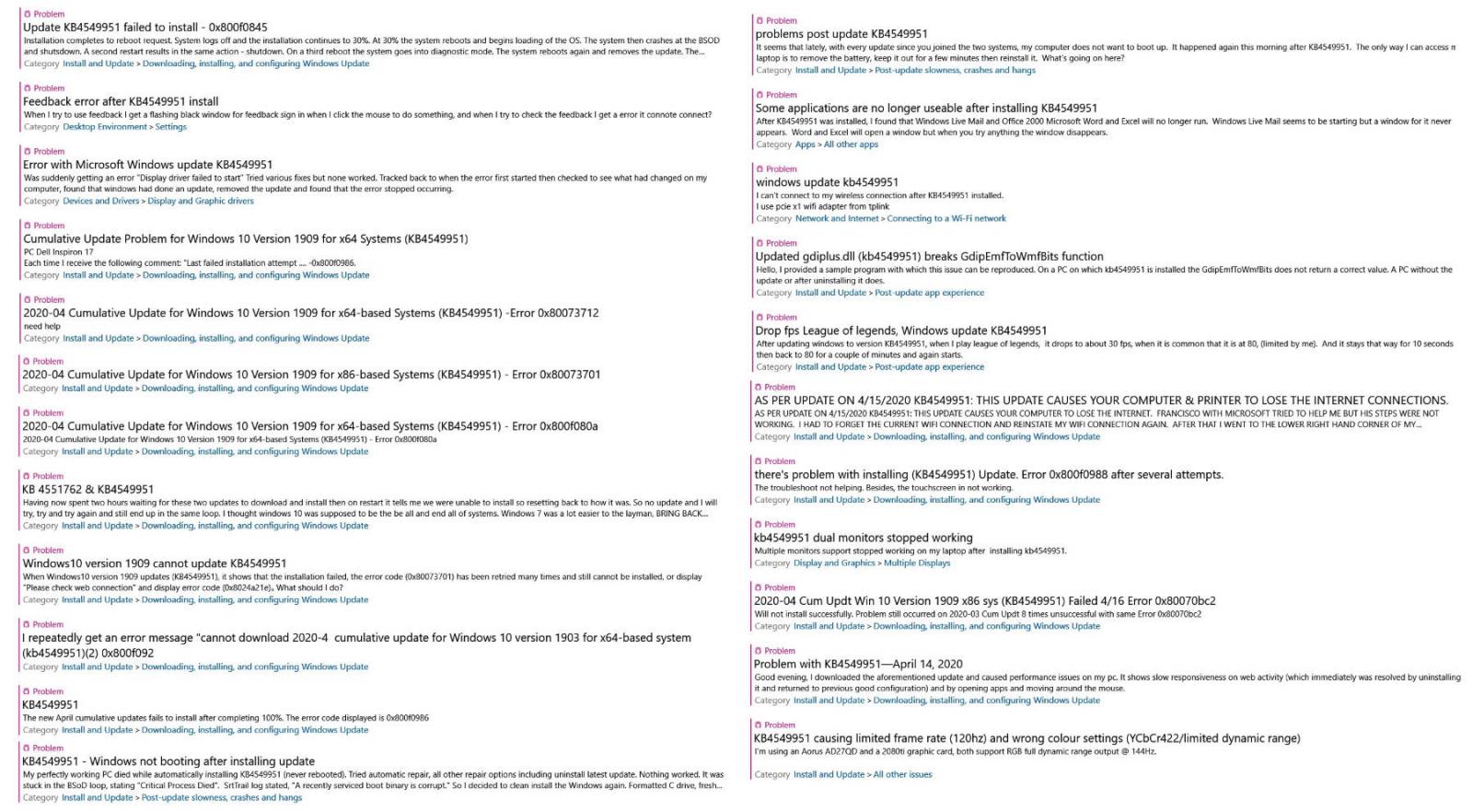 Some of the KB4549951 issues reported via the Feedback Hub
Some of the KB4549951 issues reported via the Feedback Hub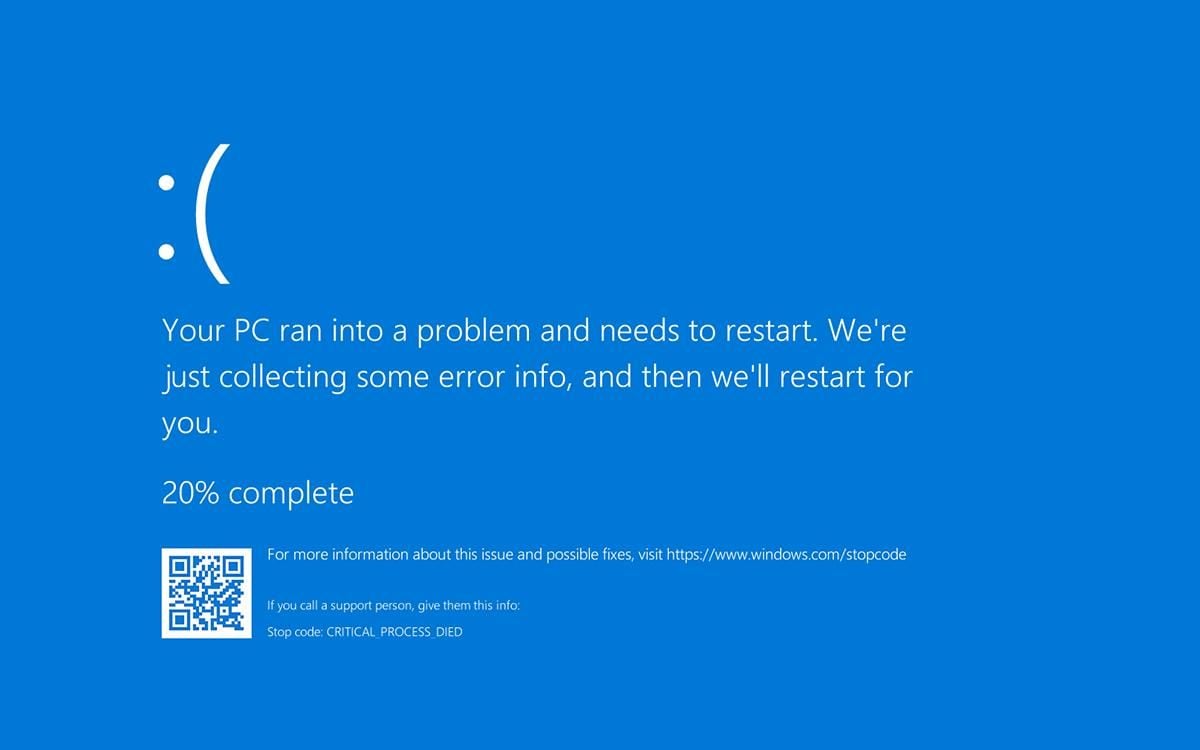 Windows 10 BSOD after CRITICAL_PROCESS_DIED error
Windows 10 BSOD after CRITICAL_PROCESS_DIED error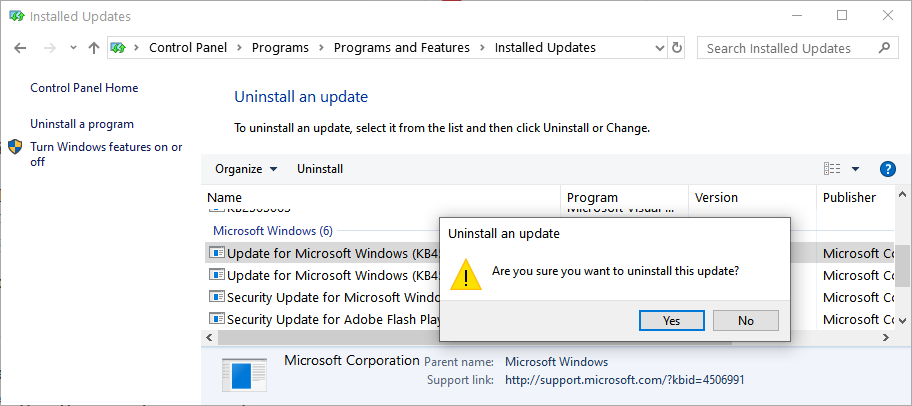 Uninstalling the KB4549951 update
Uninstalling the KB4549951 update






