By
Lawrence Abrams March 31, 2020

Since countries have begun enforcing shelter-in-place and stay-at-home orders during the Coronavirus pandemic, the Zoom video conferencing software has become a popular way to keep in touch with friends and family, and even to join online fitness classes.
However. with Zoom's rise in popularity, a type of attack called 'Zoom-bombing' has also seen more and more activity.
Zoom-bombing is when someone gains unauthorized access to a Zoom meeting to harass the meeting participants in various ways to spread and hate and divisiveness, or to record pranks that will be later shown on social media.
Just yesterday,
the FBI released an advisory warning Zoom users that they should properly secure their browsers from Zoom-bombing attacks.
"The FBI has received multiple reports of conferences being disrupted by pornographic and/or hate images and threatening language," the alert published by the FBI warned.
This guide will walk you through securing your Zoom meetings so that virtual get-togethers, meetings, exercise classes, and even happy hours are not Zoom-bombed by unauthorized users.
Privacy considerations when using Zoom
Before we get into learning how to use Zoom, it is important to consider the privacy ramifications of participating in Zoom meetings.
One of the most important things to remember is that a Host can record a Zoom session, including the video and audio, to their computer. Therefore, be careful saying or physically 'revealing' anything that you would not want someone else to potentially see or know about.
Meeting participants will know when a meeting is being recorded as there will be a 'Recording...' indicator displayed in the top left of the meeting as shown below.
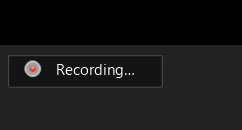
It is also important to remember that a user can download their chat logs before leaving a meeting. These logs will only contain messages that you could see, but not the private chat messages of other users.
Finally, it has
been reported that there is no true end-to-end encryption (E2E) between Zoom users' endpoints.
What this means is that only the communication between a meeting participant and Zoom's servers is encrypted, while the related meeting data traversing over Zoom's network is not.
This theoretically means that a Zoom employee could monitor a meeting's traffic and snoop on it, but Zoom has told The Intercept that there are safeguards in place to prevent this type of activity.
"Zoom has layered safeguards in place to protect our users’ privacy, which includes preventing anyone, including Zoom employees, from directly accessing any data that users share during meetings, including — but not limited to — the video, audio and chat content of those meetings. Importantly, Zoom does not mine user data or sell user data of any kind to anyone."
Securing your Zoom meetings
Now that you know the potential privacy risks of using Zoom, before scheduling a meeting with friends or coworkers, you can familiarize yourself with the various ways you can secure Zoom meetings using the steps below.
Add a password to all meetings!
When creating a new Zoom meeting, Zoom will automatically enable the "Require meeting password" setting and assign a random 6 digit password.
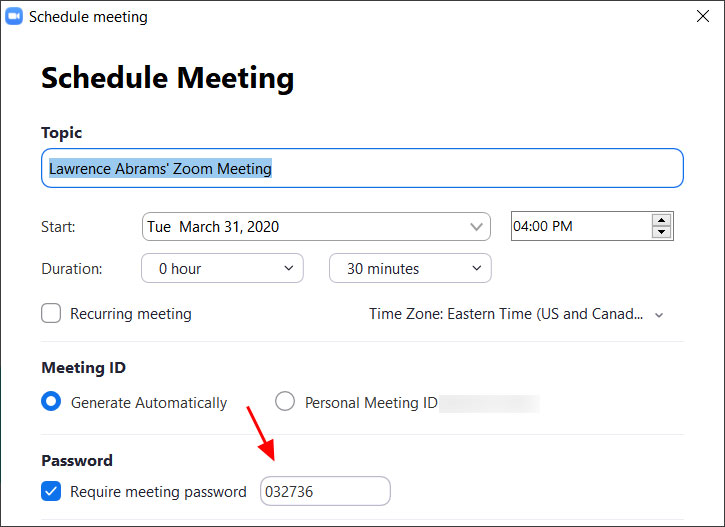
You should not uncheck this option as doing so will allow anyone to gain access to your meeting without your permission.
Use waiting rooms
Zoom allows the host (the one who created the meeting) to enable a waiting room feature that prevents users from entering the meeting without first being admitted by the host.
This feature can be enabled during the meeting creation by opening the advanced settings, checking the 'Enable waiting room' setting, and then clicking on the 'Save' button.
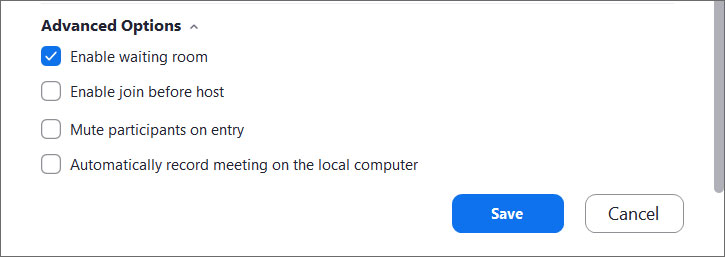
Enable waiting room setting
When enabled, anyone who joins the meeting will be placed into a waiting room where they will be shown a message stating "Please wait, the meeting host will let you in soon."
The meeting host will then be alerted when anyone joins the meeting and can see those waiting by clicking on the 'Manage Participants' button on the meeting toolbar.
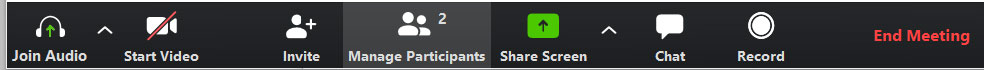
You can then hover your mouse over each waiting user and 'Admit' them if they belong in the meeting.
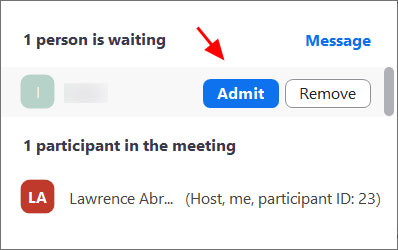
Admit a person into the meeting
Keep Zoom client updated
If you are prompted to update your Zoom client, please install the update.
The latest Zoom updates enable Meeting passwords by default and add protection from people scanning for meeting IDs.
With Zoom being so popular at this time, more threat actors will also focus on it to find vulnerabilities. By installing the latest updates as they are released, you will be protected from any discovered vulnerabilities.
Do not share your meeting ID
Each Zoom user is given a permanent 'Personal Meeting ID' (PMI) that is associated with their account.
If you give your PMI to someone else, they will always be able to check if there is a meeting in progress and potentially join it if a password is not configured.
Instead of sharing your PMI, create new meetings each time that you will share with participants as necessary.
Disable participant screen sharing
To prevent your meeting from being hijacked by others, you should prevent participants other than the Host from sharing their screen.
As a host, this can be done in a meeting by clicking on the up arrow next to 'Share Screen' in the Zoom toolbar and then clicking on 'Advanced Sharing Options' as shown below.
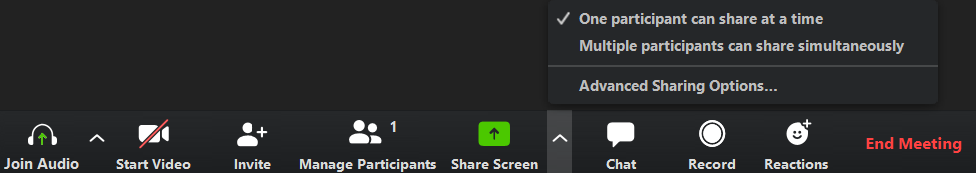
When the Advanced Sharing Options screen opens, change the 'Who Can Share?' setting to 'Only Host'.
You can then close the settings screen by clicking on the X.
Lock meetings when everyone has joined
If everyone has joined your meeting and you are not inviting anyone else, you should Lock the meeting so that nobody else can join.
To do this, click on the 'Manage Participants' button on the Zoom toolbar and select 'More' at the bottom of the Participants pane. Then select the 'Lock Meeting' option as shown below.
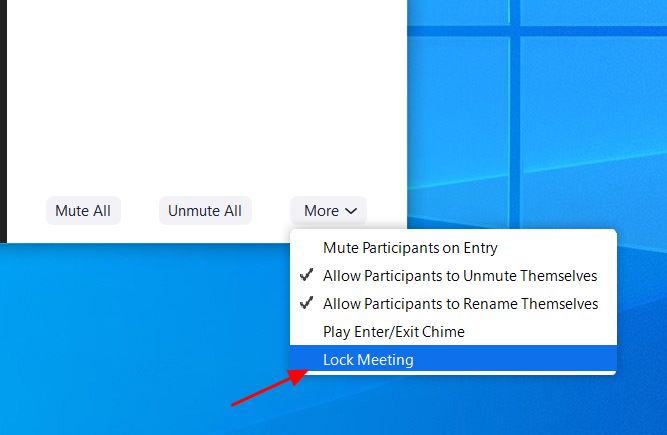
Do not post pictures of your Zoom meetings
If you take a picture of your Zoom meeting than anyone who sees this picture will be able to see its associated meeting ID. This can then be used uninvited people to try and access the meeting.
For example, the UK Prime Minister Boris Johnson tweeted a picture today of the "first even digital Cabinet" and included in the picture was the meet ID.
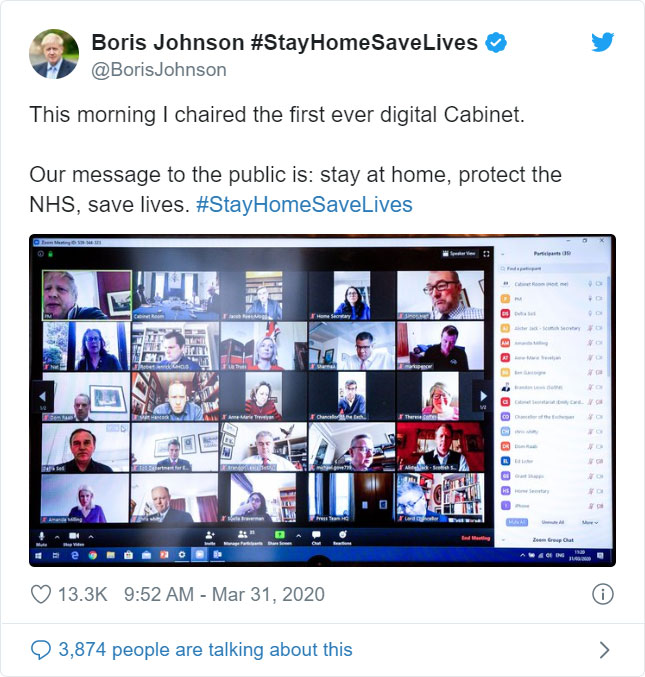
This could have been used by attackers to try and gain unauthorized access to the meeting by manually joining via the displayed ID.
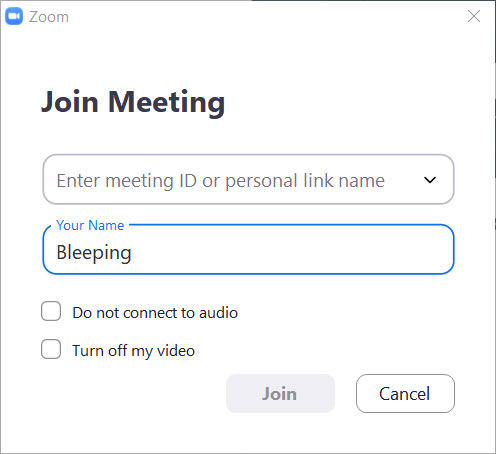
Manually join a meeting by ID
Thankfully, the virtual cabinet meeting was password-protected but does illustrate why all meetings need to use a password or at least a waiting room.
Do not post public links to your meetings
When creating Zoom meetings, you should never publicly post a link to your meeting.
Doing so will cause search engines such as Google to index the links and make them accessible to anyone who searches for them.
As the default setting in Zoom is to embed passwords in the invite links, once a person has your Zoom link they can Zoom-bomb your meeting.
Be on the lookout for Zoom-themed malware
Since the Coronavirus outbreak, there has been a rapid increase in the number of threat actors creating
malware,
phishing scams, and other attacks related to the pandemic.
This includes malware and adware installers being created that
pretend to be Zoom client installers.
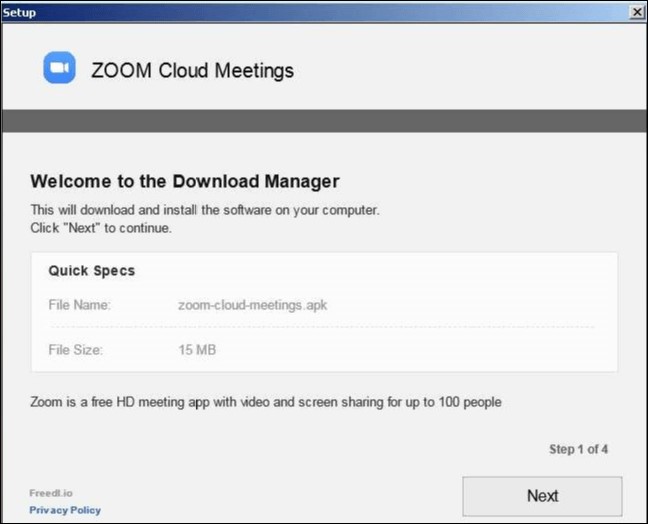
Malicious Zoom installer
To be safe, only download the Zoom client directly from the legitimate
Zoom.us site and not from anywhere else.




 Enable waiting room setting
Enable waiting room setting Admit a person into the meeting
Admit a person into the meeting



 Manually join a meeting by ID
Manually join a meeting by ID Malicious Zoom installer
Malicious Zoom installer



 Vulnerable REST route (Defiant)
Vulnerable REST route (Defiant)