By Sergiu Gatlan April 3, 2020 11:20 AM

Zoom users are currently reporting that they are unable to use the Zoom web client or start and attend webinars, with reports saying that the web client is throwing '403 Forbidden' errors.
Other reports mention time out errors saying that "Your connection has timed out and you cannot join the meetings. Verify your networkk connectivity and try again."
Based on user reports on DownDetector, Zoom users from the US East Coast and Western Europe are most affected by these ongoing issues,
According to the platform's status page, the Zoom web client is under maintenance and, as detailed on the company's dev forum, Zoom is "working to get the Zoom Web Client and Zoom Web SDK back online."
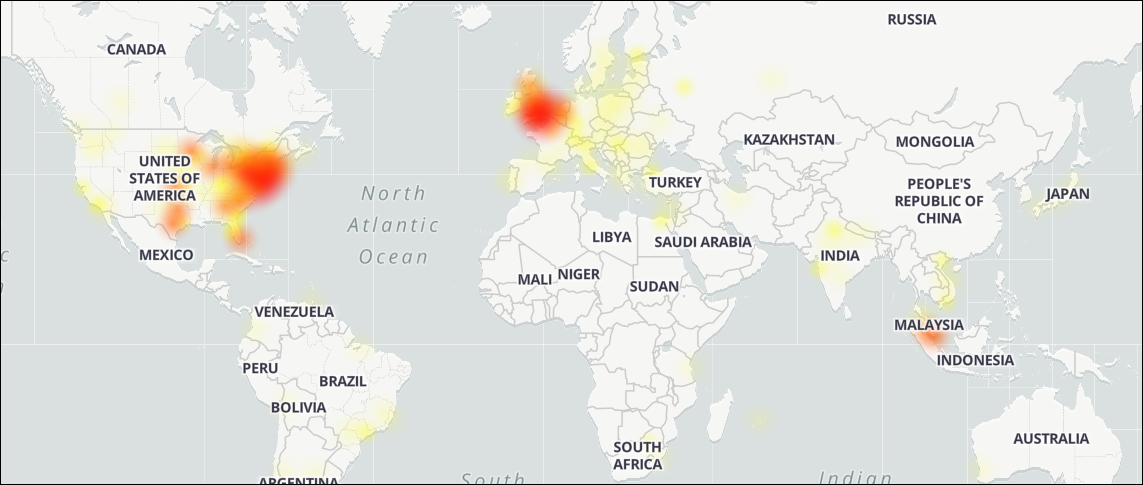 Zoom outage map (DownDeetector)
Zoom outage map (DownDeetector)
A Zoom spokesperson confirmed the web client outage, and advised users to download and install the desktop application until the issues are resolved.
"Our team is currently aware of issues with users joining Zoom meetings and webinars using Zoom’s web client," a statement from a Zoom spokesperson says.
"In the interim, we recommend downloading and installing Zoom from zoom.us/download to connect to your meeting. We are working on it and will post further information and updates on status.zoom.us shortly.
"Sorry for the inconvenience. Thank you very much for your patience."
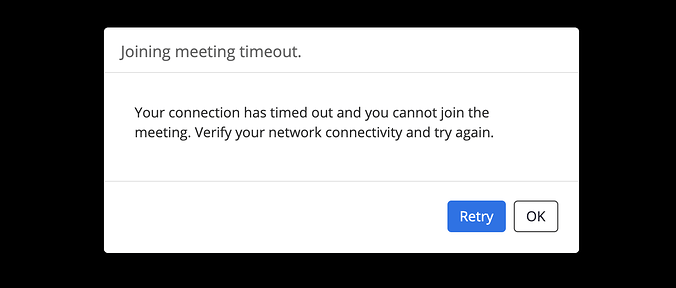 Zoom timeout error (aleksandr.borovsky)
Zoom timeout error (aleksandr.borovsky)
Software company Zoom provides users with a cloud-based communication platform that can be used for video conferencing, online meetings, and chat and collaboration via mobile, desktop, and telephone systems.
Zoom has seen a quick increase of new monthly active users since the start of 2020, with millions of employees and students who are now working and learning from home using the platform.
Zoom has gained around 2.22 million new users this year alone, while only 1.99 million were added last year. In total, it now has over 12.9 million monthly active users, with Bernstein Research analysts saying last month that Zoom saw a user growth of about 21% since the end of 2019 as reported by CNBC.

Zoom users are currently reporting that they are unable to use the Zoom web client or start and attend webinars, with reports saying that the web client is throwing '403 Forbidden' errors.
Other reports mention time out errors saying that "Your connection has timed out and you cannot join the meetings. Verify your networkk connectivity and try again."
Based on user reports on DownDetector, Zoom users from the US East Coast and Western Europe are most affected by these ongoing issues,
According to the platform's status page, the Zoom web client is under maintenance and, as detailed on the company's dev forum, Zoom is "working to get the Zoom Web Client and Zoom Web SDK back online."
 Zoom outage map (DownDeetector)
Zoom outage map (DownDeetector)A Zoom spokesperson confirmed the web client outage, and advised users to download and install the desktop application until the issues are resolved.
"Our team is currently aware of issues with users joining Zoom meetings and webinars using Zoom’s web client," a statement from a Zoom spokesperson says.
"In the interim, we recommend downloading and installing Zoom from zoom.us/download to connect to your meeting. We are working on it and will post further information and updates on status.zoom.us shortly.
"Sorry for the inconvenience. Thank you very much for your patience."
 Zoom timeout error (aleksandr.borovsky)
Zoom timeout error (aleksandr.borovsky)Software company Zoom provides users with a cloud-based communication platform that can be used for video conferencing, online meetings, and chat and collaboration via mobile, desktop, and telephone systems.
Zoom has seen a quick increase of new monthly active users since the start of 2020, with millions of employees and students who are now working and learning from home using the platform.
Zoom has gained around 2.22 million new users this year alone, while only 1.99 million were added last year. In total, it now has over 12.9 million monthly active users, with Bernstein Research analysts saying last month that Zoom saw a user growth of about 21% since the end of 2019 as reported by CNBC.







 A website dedicated to technology news from Africa… and Ralph Lauren gear?
A website dedicated to technology news from Africa… and Ralph Lauren gear?