
Criminals are using the Covid-19 pandemic to scam the public – don’t become a victim.
Law enforcement, government and private sectors partners are working together to encourage members of the public to be more vigilant against fraud, particularly about sharing their financial and personal information, as criminals seek to capitalise on the Covid-19 pandemic.
Criminals are experts at impersonating people, organisations and the police.
They spend hours researching you for their scams, hoping you’ll let your guard down for just a moment.
Stop: Taking a moment to stop and think before parting with your money or information could keep you safe.
Challenge: Could it be fake? It’s ok to reject, refuse or ignore any requests. Only criminals will try to rush or panic you.
Protect: Contact your bank immediately if you think you’ve fallen for a scam and report it to Action Fraud*.
Your bank or the police will NEVER ask you to transfer money or move it to a safe account.
Criminals are targeting people looking to buy medical supplies online, sending emails offering fake medical support and scamming people who may be vulnerable or increasingly isolated at home. These frauds try to lure you in with offers that look too good to be true, such as high return investments and ‘healthcare opportunities’, or make appeals for you to support bogus charities or those who are ill.
Reports from the public have already included online shopping scams where people have ordered protective face masks, hand sanitiser, and other products, which have never arrived and a number of cases have been identified where fake testing kits have been offered for sale.
Criminals are also using Government branding to try to trick people, including reports of using HMRC branding to make spurious offers of financial support through unsolicited emails, phone calls and text messages.
This situation is likely to continue, with criminals looking to exploit further consequences of the pandemic, such as exploiting financial concerns to ask for upfront fees for bogus loans, offering high-return investment scams, or targeting pensions.
Huge increases in the number of people working remotely mean that significantly more people will be vulnerable to computer service fraud where criminals will try and convince you to provide access to your computer or divulge your logon details and passwords. It is also anticipated that there will be a surge in phishing scams or calls claiming to be from government departments offering grants, tax rebates, or compensation.
Please see below for more information on the most common COVID-19 frauds and the steps you can take to keep yourself safe.
Online Shopping and Auction FraudMore people may fall victim to #onlineshopping fraud as they self-isolate due to #COVID19. You are a victim of online shopping fraud if you buy goods from an online seller that never arrive.
Computer Software Service FraudAs more people work from home due to #COVID19, fraudsters may capitalise on slow networks and IT problems, to commit computer software service fraud. Be wary of cold calls or unsolicited emails offering you help with your device or to fix a problem
Lender Loan FraudPeople may be worrying about their finances during the #COVID19 outbreak. Lender loan fraudsters will use the opportunity to:
- approve your application for a fast loan regardless of your credit history
- ask you to pay an upfront fee
- take your payment and never provide the loan
Pension Liberation Fraud and
Investment FraudFraudsters could try to take advantage of the financial uncertainty surrounding #COVID19 by offering people sham investment opportunities. If you get a cold call or unsolicited email offering you a deal that sounds too good to be true, it probably is.
Mandate FraudAs more people work from home due to #COVID19, fraudsters may try to get you to change a direct debit, standing order or bank transfer mandate, to divert funds to their bank account, by purporting to be an organisation you make regular payments to.
PhishingA number of #COVID19 related phishing emails have been reported to Action Fraud. These emails attempt to trick you into opening malicious attachments which could lead to fraudsters stealing your personal information, logins, passwords, or banking details.
Update 26/03: The Government has only sent one text message to the public regarding new rules about staying at home to prevent the spread of COVID-19. Any others claiming to be from UK Government are false.
“Criminals are able to use spoofing technology to send texts and emails impersonating organisations that you know and trust. We would remind anyone who receives an unexpected text or email asking for personal or financial details not click on the links or attachments, and don’t respond to any messages that ask for your personal or financial details.
 BySecNews 31 Μαρτίου 2020,
BySecNews 31 Μαρτίου 2020,


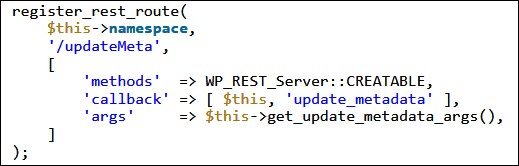 Vulnerable REST route (Defiant)
Vulnerable REST route (Defiant)
 GETTY IMAGES
GETTY IMAGES