By Lawrence Abrams April 12, 2020 11:15 AM 0

A malware distributor has decided to play a nasty prank by locking victim's computers before they can start Windows and then blaming the infection on two well-known and respected security researchers.
Over the past 24 hours, after downloading and installing software from what appears to be free software and crack sites, people suddenly find that they are locked out of their computer before Windows starts.
When locked out, the PC will display a message stating that they were infected by Vitali Kremez and MalwareHunterTeam, who are both well-known malware and security researchers and have nothing to do with this malware.
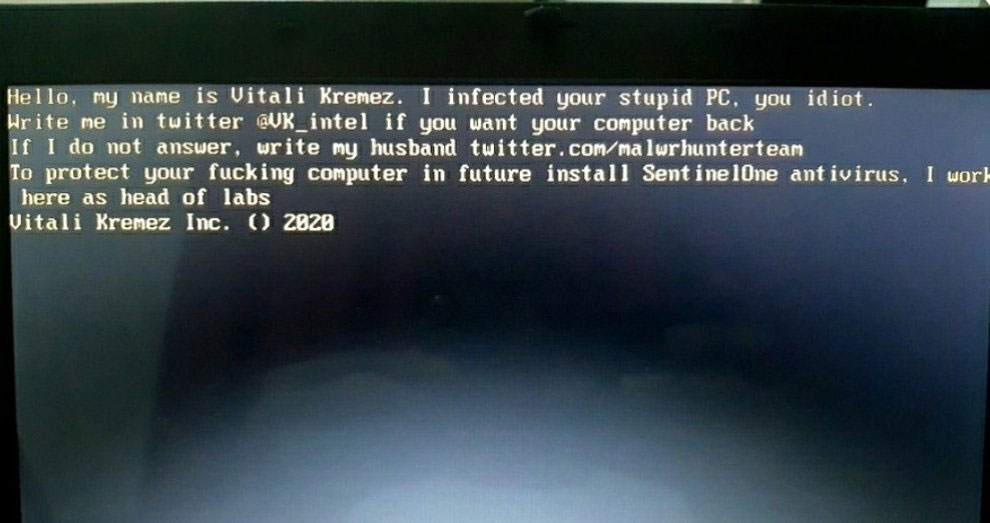 MBR locker impersonating Vitali and MalwareHunterTeam
MBR locker impersonating Vitali and MalwareHunterTeamThe full text of this MBRLocker can be read below: Hello, my name is Vitali Kremez. I infected your stupid PC. you idiot. Write me in twitter @VK_intel if you want your computer back If I do not answer, write my husband twitter.com/malwrhunterteam To protect your ***ing computer in future install SentinelOne antivirus. I work here as head of labs. Vitali Kremez Inc. () 2020
MBRLockers are programs that replace the 'master boot record' of a computer so that it prevents the operating system from starting and displays a ransom note or other message instead.
This type of infection is used in ransomware attacks such as Petya or as a destructive wiper to prevent people from accessing their files.
In this particular case, it looks like a malware developer or distributor is trying to tarnish the name of Kremez and MalwareHunterTeam and released this infection as a destructive prank.
To reiterate, MalwareHunterTeam and Kremez have nothing to do with this infection.
Recovery may be possible
Recently, there has been a flurry of new MBRLockers being released that appear to be created for 'fun' or as part of 'pranks'.
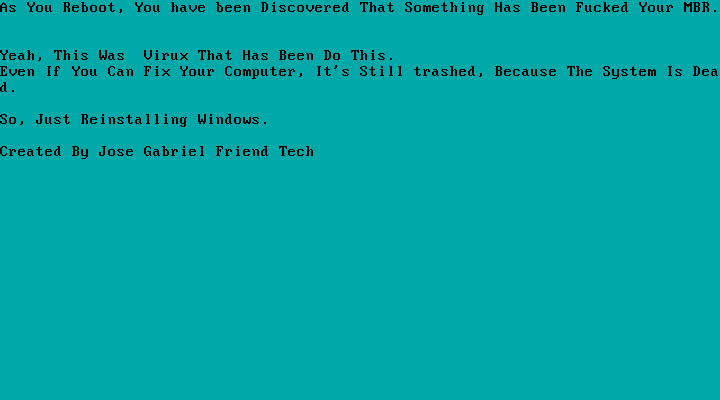 Example of recent MBRLocker
Example of recent MBRLockerRecently, a flurry of MBRLockers have been created using a publicly available tool being promoted on YouTube and Discord. BleepingComputer believes that this tool was used to create this MBRLocker to troll both Kremez and MalwareHunterTeam.
When creating MBRLockers using this tool, the malware will first make a backup of the original MBR of the computer to a safe location before replacing it.
If this wiper is using the same MBRLocker builder, then it will be possible to recover the MBR so people can gain access to their computer.
In one sample, there was also a fail-safe keyboard combination of pressing the CTRL+ALT+ESC keys at the same time to restore the MBR and boot the computer.
Unfortunately, we have not been able to get the sample of this malware as of yet to determine if its the same builder or if the keyboard combination works.
If you have been infected and know where you downloaded the file, please submit a sample here or contact us on Twitter with the site you downloaded the file.
No comments:
Post a Comment