By
GURUBARAN S - March 27, 2020
0
Google implements a number of ways to filter the malicious apps getting into the play store, but still, attackers continue to find ways to infiltrate the app store and infect user devices.
Security researchers from Check Point identified 56 malicious apps in play store that aimed to commit mobile fraud with new malware families dubbed ‘Tekya’.
Tekya Malware Play Store
The malware aims to steal user data such as credentials, emails, text messages, and geographical location.
The Tekya malware founded to be hidden with 56 apps that were downloaded more than 1 million times worldwide. Out of 56 apps, 24 of the infected apps targeting apps used by kids such as puzzles to racing games.
Researchers
found that “Tekya malware obfuscates native code to avoid detection by Google Play Protect and utilizes the ‘
MotionEvent’ mechanism in Android to imitate the user’s actions and generate clicks”.
MotionEvent is a mechanism in an Android device that used to report movements such as a mouse, pen, finger, trackball events.
With this
campaign, attackers cloned the legitimate versions of the app and host fake versions with malware embedded.
Once this malware gets installed in the device, a receiver gets registered and multiple actions performed in the device.
The receiver “us.pyumo.TekyaReceiver” get’s registered to perform the following actions
‘BOOT_COMPLETED’ to allow code running at device startup (“cold” startup)
‘USER_PRESENT’ in order to detect when the user is actively using the device
‘QUICKBOOT_POWERON’ to allow code running after device restart

The main goal of the malware is to click on the ads banner from agencies such as Google’s AdMob, AppLovin, Facebook, and Unity.
Here you can find the full list of the infected apps
Package_name Gp Installs
caracal.raceinspace.astronaut 100000
com.caracal.cooking 100000
com.leo.letmego 100000
com.caculator.biscuitent 50000
com.pantanal.aquawar 50000
com.pantanal.dressup 50000
inferno.me.translator 50000
translate.travel.map 50000
travel.withu.translate 50000
allday.a24h.translate 10000
banz.stickman.runner.parkour 10000
best.translate.tool 10000
com.banzinc.littiefarm 10000
com.bestcalculate.multifunction 10000
com.folding.blocks.origami.mandala 10000
com.goldencat.hillracing 10000
com.hexa.puzzle.hexadom 10000
com.ichinyan.fashion 10000
com.maijor.cookingstar 10000
com.major.zombie 10000
com.mimochicho.fastdownloader 10000
com.nyanrev.carstiny 10000
com.pantanal.stickman.warrior 10000
com.pdfreader.biscuit 10000
com.splashio.mvm 10000
com.yeyey.translate 10000
leo.unblockcar.puzzle 10000
mcmc.delicious.recipes 10000
mcmc.delicious.recipes 10000
multi.translate.threeinone 10000
pro.infi.translator 10000
rapid.snap.translate 10000
smart.language.translate 10000
sundaclouded.best.translate 10000
biaz.jewel.block.puzzle2019 5000
biaz.magic.cuble.blast.puzzle 5000
biscuitent.imgdownloader 5000
biscuitent.instant.translate 5000
com.besttranslate.biscuit 5000
com.inunyan.breaktower 5000
com.leo.spaceship 5000
com.michimocho.video.downloader 5000
fortuneteller.tarotreading.horo 5000
ket.titan.block.flip 5000
mcmc.ebook.reader 5000
swift.jungle.translate 5000
com.leopardus.happycooking 1000
com.mcmccalculator.free 1000
com.tapsmore.challenge 1000
com.yummily.healthy.recipes 1000
com.hexamaster.anim 500
com.twmedia.downloader 100
com.caracal.burningman 50
com.cuvier.amazingkitchen 50
bis.wego.translate 0
com.arplanner.sketchplan 0
com.arsketch.quickplan 0
com.livetranslate.best 0
com.lulquid.calculatepro 0
com.smart.tools.pro 0
com.titanyan.igsaver 0
hvt.ros.digiv.weather.radar 0
md.titan.translator 0
scanner.ar.measure 0
toolbox.artech.helpful 0
toolkit.armeasure.translate 0
This shows that attackers still finding ways to bypass the Google Play Store and infiltrate with malicious apps.
Before installing apps users are recommended to check the background of the application and its developer company reputation.
 BySecNews 31 Μαρτίου 2020,
BySecNews 31 Μαρτίου 2020,


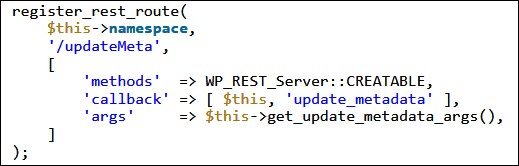 Vulnerable REST route (Defiant)
Vulnerable REST route (Defiant)
 GETTY IMAGES
GETTY IMAGES
 Marc Wilczek, COO, Link11
Marc Wilczek, COO, Link11





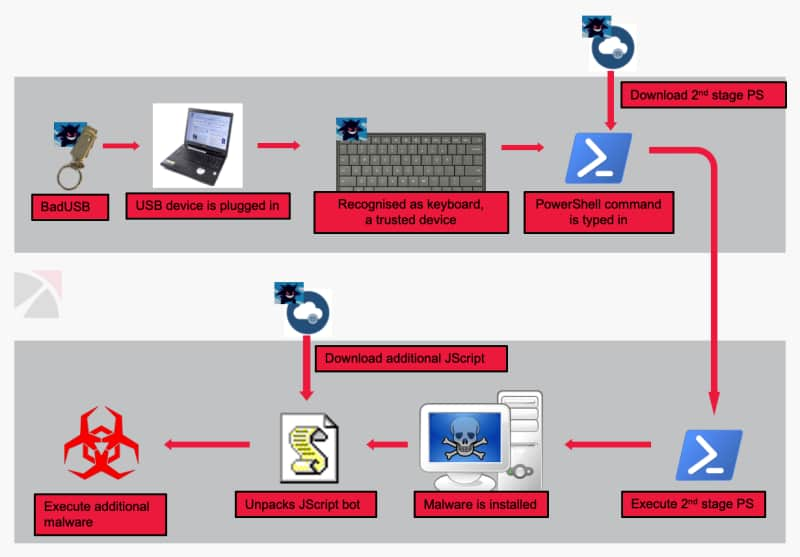
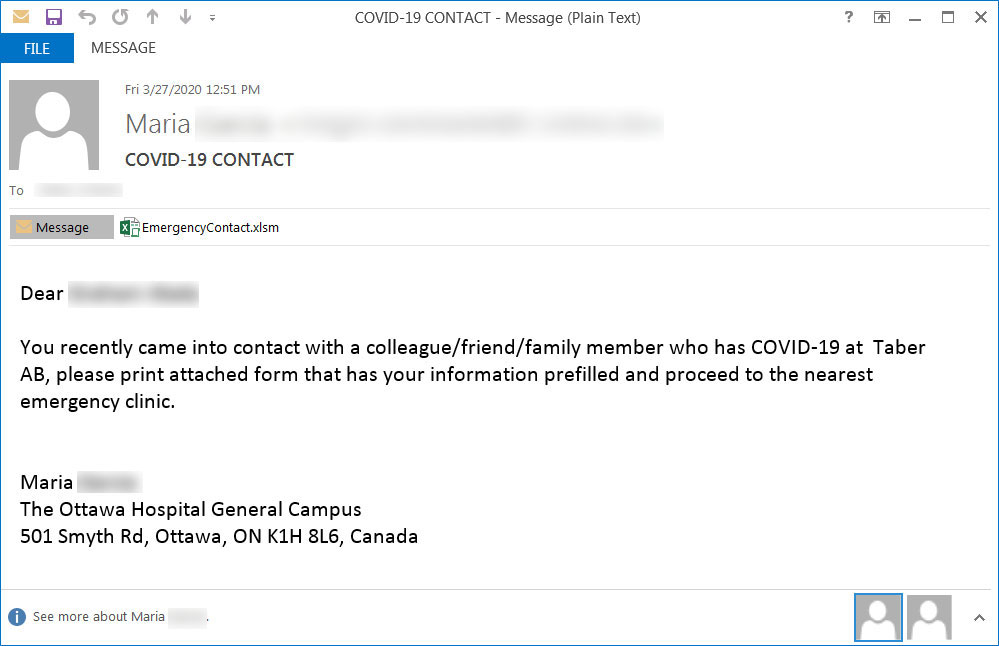 Coronavirus-themed phishing email
Coronavirus-themed phishing email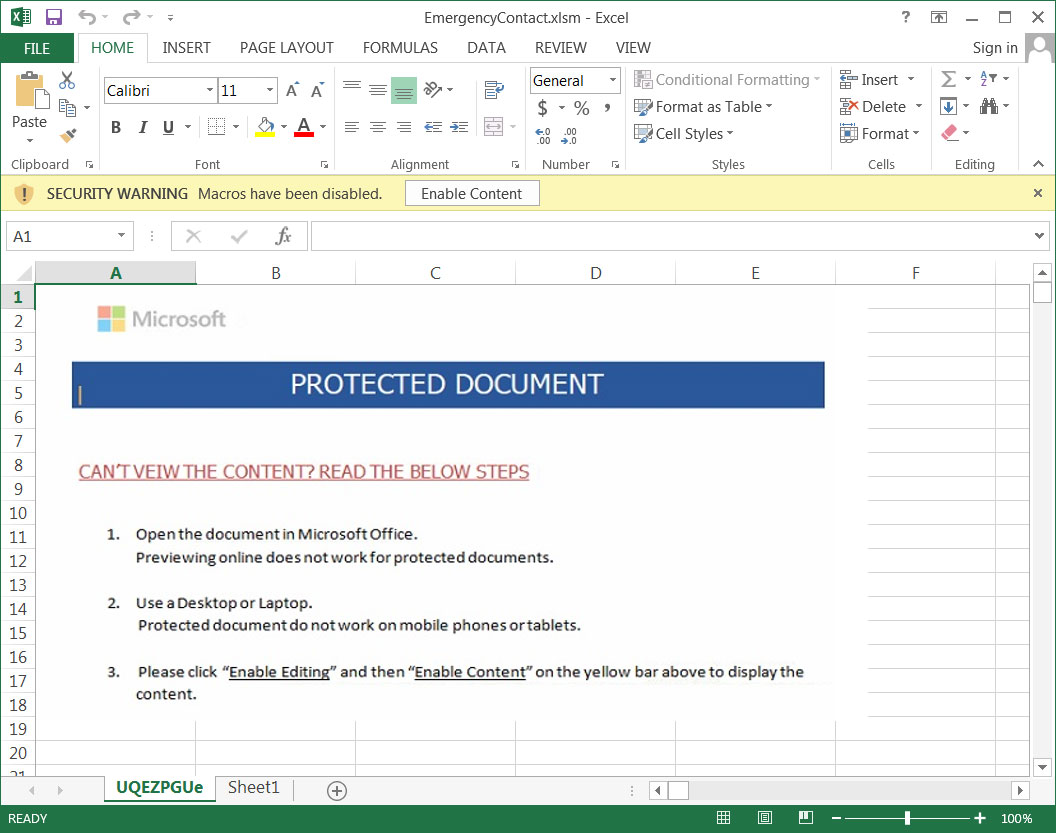 Malicious attachment
Malicious attachment