By Lawrence Abrams March 29, 2020 12:12 PM 0
A new phishing campaign has been spotted that pretends to be from a local hospital telling the recipient that they have been exposed to the Coronavirus and that they need to be tested.
With the Coronavirus pandemic affecting all corners of the world, we continue to see phishing actors try to take advantage of the fear and anxiety it is provoking to scare people into opening malicious email attachments.
In a new low, a threat actor is pretending to be from a local hospital telling the recipient that they have been in contact with a colleague, friend, or family member who has tested positive for the COVID-19 virus.
The email then tells the recipient to print the attached EmergencyContact.xlsm attachment and bring it with them to the nearest emergency clinic for testing.
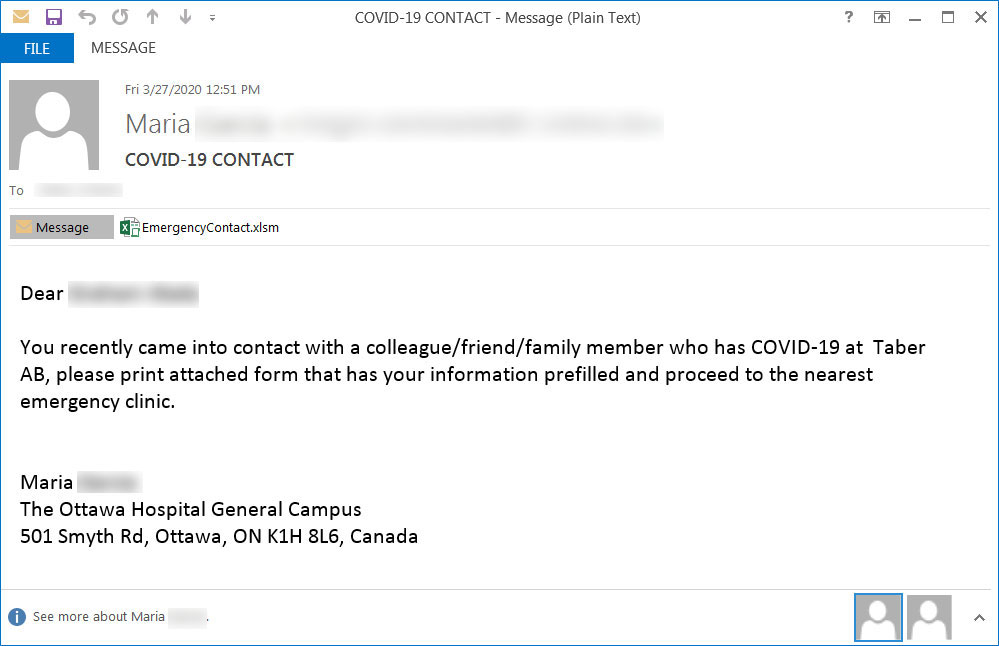 Coronavirus-themed phishing email
Coronavirus-themed phishing email
The text of this email reads:Dear XXX You recently came into contact with a colleague/friend/family member who has COVID-19 at Taber AB, please print attached form that has your information prefilled and proceed to the nearest emergency clinic. Maria xxx The Ottawa Hospital General Campus 501 Smyth Rd, Ottawa, ON K1H 8L6, Canada
When a user opens the attachment. they will be prompted to 'Enable Content' to view the protected document.
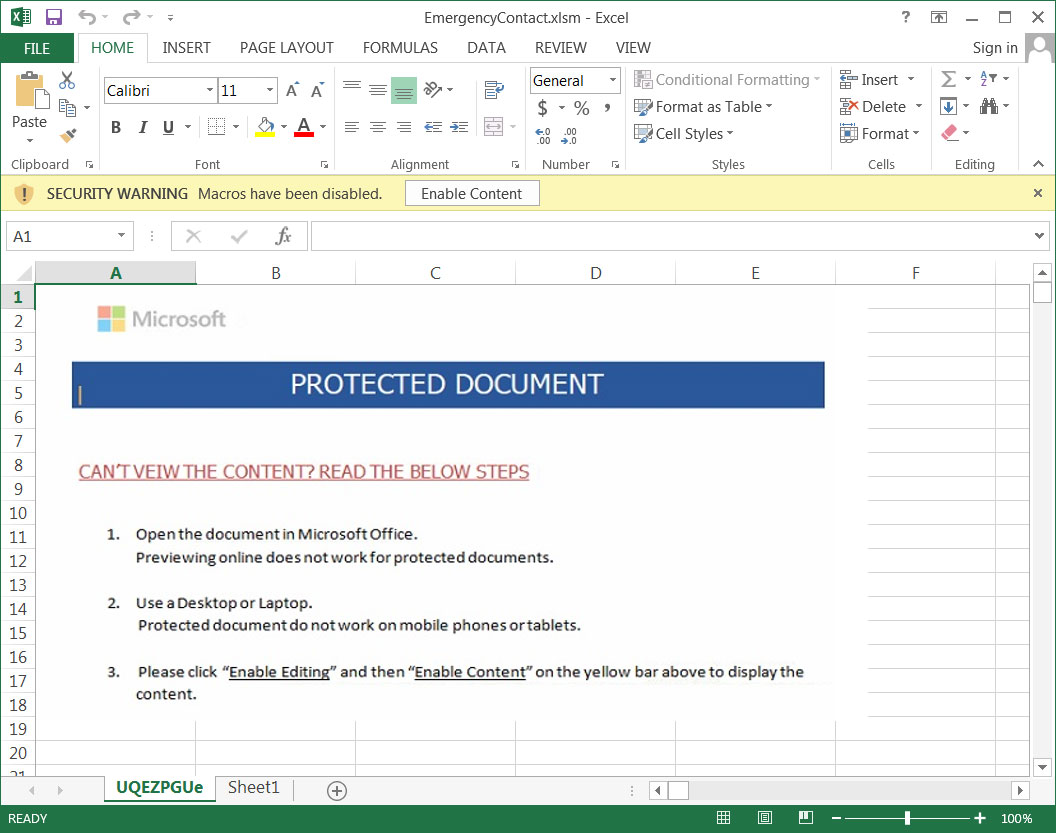 Malicious attachment
Malicious attachment
If a user enables content, malicious macros will be executed to download a malware executable to the computer and launch it.
This executable will now inject numerous processes into the legitimate Windows msiexec.exe file. This is done to hide the presence of the running malware and potentially evade detection by security programs.
In a cursory analysis, BleepingComputer saw that the malware performed the following behavior:
Search for and possibly steal cryptocurrency wallets.
Steals web browser cookies that could allow attackers to log in to sites with your account.
Gets a list of programs running on the computer.
Looks for open shares on the network with the net view /all /domain command.
Gets local IP address information configured on the computer.
During this crisis, it is important for everyone to be especially careful of any Coronavirus-related emails that they receive and to not open any attachments.
Instead, you should look up the number for the alleged sender and contact them via phone to confirm the email and the enclosed information.
Furthermore, if you are looking for the latest trust Coronavirus information you should go to the sites for the CDC, WHO, or your local health department instead rather than risk opening an attachment from a stranger.

A new phishing campaign has been spotted that pretends to be from a local hospital telling the recipient that they have been exposed to the Coronavirus and that they need to be tested.
With the Coronavirus pandemic affecting all corners of the world, we continue to see phishing actors try to take advantage of the fear and anxiety it is provoking to scare people into opening malicious email attachments.
In a new low, a threat actor is pretending to be from a local hospital telling the recipient that they have been in contact with a colleague, friend, or family member who has tested positive for the COVID-19 virus.
The email then tells the recipient to print the attached EmergencyContact.xlsm attachment and bring it with them to the nearest emergency clinic for testing.
 Coronavirus-themed phishing email
Coronavirus-themed phishing emailThe text of this email reads:Dear XXX You recently came into contact with a colleague/friend/family member who has COVID-19 at Taber AB, please print attached form that has your information prefilled and proceed to the nearest emergency clinic. Maria xxx The Ottawa Hospital General Campus 501 Smyth Rd, Ottawa, ON K1H 8L6, Canada
When a user opens the attachment. they will be prompted to 'Enable Content' to view the protected document.
 Malicious attachment
Malicious attachmentIf a user enables content, malicious macros will be executed to download a malware executable to the computer and launch it.
This executable will now inject numerous processes into the legitimate Windows msiexec.exe file. This is done to hide the presence of the running malware and potentially evade detection by security programs.
In a cursory analysis, BleepingComputer saw that the malware performed the following behavior:
Search for and possibly steal cryptocurrency wallets.
Steals web browser cookies that could allow attackers to log in to sites with your account.
Gets a list of programs running on the computer.
Looks for open shares on the network with the net view /all /domain command.
Gets local IP address information configured on the computer.
During this crisis, it is important for everyone to be especially careful of any Coronavirus-related emails that they receive and to not open any attachments.
Instead, you should look up the number for the alleged sender and contact them via phone to confirm the email and the enclosed information.
Furthermore, if you are looking for the latest trust Coronavirus information you should go to the sites for the CDC, WHO, or your local health department instead rather than risk opening an attachment from a stranger.
No comments:
Post a Comment