By Balaji N - February 9, 2020 3
Both the VPN and proxy are used to facilitate the connection between the client and server by hiding it’s IP address and they are slightly different in the way it handles the data.
In the modern cyber world, we have faced a lot of concerns about our privacy, both the VPNs and proxy handle it significantly.
It is quite significant to have the knowledge of the difference between the VPN vs Proxy and the scenario where can we use and where we cannot.
What is a Proxy?
Proxy or proxy server is an intermediate node between client and internet that takes a request from Client and pass it to the various server and provide indirect network services to the client. primary purpose of the proxy is to filter the dangerous internet traffic by applying the strict rule to ensure the anonymity for the client.
It enables us to hide the client’s IP and the location from the site he visits. by connecting to one of the proxy servers, the client request is forwarded to the proxy then it processes the client request and the result will be returned to the client.

What is a VPN?
VPN or Virtual Private Network is a technology that developed to provide secure access over the internet for clients’ requests via encrypted tunnels. VPN redirects the client’s side request via the remote server which is run by VPN service providers. it helps to ensure the sensitive data remain private during the transmission over the internet from one place to another place.
VPN Shield the users browsing activity and bypassing Internet censorship. VPN software encrypts the user request even before your Internet Service Provider see it and it redirected to various VPN node and response to the client.

Proxy vs VPN Security
When it comes to security VPN stands ahead of the proxy servers, VPNs do have an encrypted tunnel to transfer the data securely, but that is not the case with Proxy.

Virtual Private Network (VPN) Security
With the VPN you will get a unique IP address and a secure tunnel established between you and the target that you are to get connected with it.
The VPN encryption tunnel supports the traffic that routed with all the Internet protocols with sophisticated privacy and security capabilities.
VPNs are well-known for security and reliability, it is easy for anyone to switch off or to on the VPN service.
By having an encrypted tunnel the VPNs secures your data from hackers even if you are connected with open WiFi hotspots.
VPN application supports for a number of platforms PlayStation, SmartTVs, OS/X, iPhone, Windows, Android, also other devices such as AppleTV, Chromecast, Roku, Xbox, and its support network devices as well.
With the AES -256 encryption and SSL certificates, there is no chance for an attacker to get into your data and even the government authorities can’t get your data. To construct tunnel it uses highly secured protocols PPTP, L2TP, SSTP, OpenVPN.
It helps in hiding the real location, and you can reach out to the blocked websites, videos, and other content in that blocked in your location securely.
Proxy Security
Proxy servers bridge the internet connection, it only masks the IP address of your computer and it will not encrypt the contents.
They use to communicate with HTTP or SOCKS protocol so there is encryption with the proxy servers, cybercriminals can sniff out the data that are traveling through a proxy server.
In some cases, even the cybercriminals advertise a proxy server to steal your identity. Also generally proxy servers are overloaded with visitors and terribly affect the connection speed.
HTTP proxies are more familiar and they are around being a long time and the Socket Secure (SOCKS5) proxies are used for connecting with torrent services, FTP and web servers. When compared to the regular proxy SOCKS5 Improved security.
SOCKS5 proxy is very good if you are to use a torrent or a P2P service, but it lacks privacy. If you do a lot of web surfing and simply want to bypass the websites blocked geographically and through firewall then proxy servers are ideal for you.
Proxy vs VPN Speed
VPN vs Proxy Speed is one of the most important concerns while accessing the internet using Proxy and VPN. When we talk about speed, the Proxy server is always faster than the VPN.
Proxy vs. VPN Cost
Multiple Cities and Subnets, minimum downtime, API Accessible Proxy list, and all proxy servers uplink speed.
aid Proxies are containing many servers that allow users to choose any servers in available countries. In this case, free proxies are limited and they give low bandwidth and slow down the access.
plan to spend anywhere from $5 a month for basic plans and the price also depends on the quality of proxies and the providers.
VPN and Proxy Usability
Proxy server Provide an additional layer of security between the endpoint and outside Traffic that mainly used to improve Corporate and Institutional Security.
VPN encrypts all the traffic flow between the internet and your device to prevent from ISP to monitoring your activities and collecting your browsing data.
Proxies are playing major role in anonymity web traffic and it adding identity protection for corporate officers, Reporters, and whistleblowers.
VPN also providing the high-level anonymity and encrypt the user’s request that passed through a various remote server that makes impossible to track back to you.
The organization is running its internal networks on a proxy server to control internet usage and prevent inappropriate site usage on the internal networks.
VPN Bypass Internet Censorship and let you access anything you want to access on the internet and complete away your acclivities from government and law enforcement agencies.
Proxies servers are providing Extreme Protection from hackers while using public Wi-Fi, and break the censored websites.
VPN’s are slower because of the encryption, while proxy servers are faster since Proxies do not encrypt the traffic between the internet and the user’s device.
VPN let allow you access the corporate network securely from outside internet Connectivity such as hotel, coffee shop, etc.
If you don’t have any corporate VPN then proxies are providing alternative access with high security also it provides very easy to access the client software.
VPN provides a high-security future to access the Secures Apps and Desktop/Laptop Programs but proxies are not much familiar with this case.
Proxies don’t use any tunneling operation but the proxy server is a great way to add a layer between your enterprise and the Internet
VPN Provides tunneled connections when the data send privately over the internet packet gives a layer of security that guards the substance against general visibility.
VPNs are best for…
VPNs secure your data from prying eyes, everyone from hackers to government officials using VPN services to protect the personal data. It enables users to send and receive data and remain anonymous on the Internet.
Most VPNs offer multiple concurrent connections so that the users can connect all the devices in the household to the VPN.
With the VPN all your traffic passes through a tunneled network, so even the ISP cannot see the traffic that goes with the tunnel network.
If you are an employee you can connect with your office network securely via Smartphone, tablet, and computer through a VPN.
VPN is best for protecting valuable information online.
It enables to safely shop online with Credit cards.
Enables you to browse safely with public Wi-Fi Hotspots.
By having a VPN you can reach out to your favorite movie sites, even though it blocked in your country.
With the VPN user’s ca Bypass the Web Censorship and Content Surveillance.
VPN enables you to establish communication between sites securely.
Some of the VPN providers do offer the Ad blockers as well.
Protects while logged in with the torrent sites.
With the VPN in place, you can access the websites that blocked geographically.
VPNs provide integrity, which ensures the packet is not altered when it is in transit.
A VPN anonymize would allow Peer-to-peer file-sharing which is blocked in many countries.
To say technically VPN is a wide area network that retains the functionality and the security as in the private network. These are the main uses of the VPN and the usage varies depends on the user requirements.
VPNs are not for..
VPNs may slow down the Internet Connection
You may experience a drop in speed with your internet connection when routed through VPN due to its high-quality 256-bit encryption. Sometimes VPN connection it may slow down the internet speed if too many users active in the server.
Generally, the VPN speed depends upon your internet speed, if you are in India and using a VPN server in the USA then your connection tunnel over a number of endpoints which may slow down the connection. So it is recommended users not to use the VPN wisely.
I’m under a VPN, so I can do anything online
If you are under VPN then we can’t say you are 100% anonymous, the VPN provider can see your access logs and they would hold the log’s for a period of at least 6 months based on the country location.
All the VPNs are not the same and there are a number of factors that are to be considered in classifying them based on need, supported platforms, the number of available servers.
Also, users should aware that VPNs would not secure you from Phishing or from the malware and ransomware attacks.
You can get the Free VPN, but the connection would be terrible and it suffers severely with the limitations on low bandwidth and some providers even sell your private data.
Proxies are best for…
Proxies are widely used to bypass the blocked websites in the ISP or the organization levels.
Proxy servers used in the corporate environments to shield their internal network infrastructure.
The Proxies contains a very good cache mechanism, so it can be used to speed up the browsing process.
It hides your original IP address and shows the spoofing IP address, so the destination website cannot read your original IP.
The proxy makes you remain anonymous online, but it will not encrypt the traffic as like the VPN.
With some of the proxies you can get double protection as they do have the firewall inbuilt that stops the intrusions.
Servers administrators can use proxy servers to block websites associated to social networking, gaming, adult sites for employees in the organization.
There are thousands of free and paid proxy available on the Internet, choosing a proxy you should carefully consider the downtime.
With the help of the proxy servers, one can reach to the websites that have been blocked geographically.
Implementation of the proxy is very simple and the proxies are so confined with the browsers. Some of the premium proxies would save companies bandwidth.
Proxies are not for…
The proxy servers are not secure for email communication and file transfer protocols and the proxy servers are good only for web communication.
It is less secure than storing all the user passwords in active directory, They are not compatible with all the network protocols.
With the proxy firewalls, the configuration is very difficult when compared to other modern days firewalls.
If the proxy server is compromised then there is a chance for identity theft, then you should avoid entering bank login credentials when connected through a proxy server.
The Proxy server administrator can sniff out all the details that are traveling through the server and also they are poor in handling things such as Flash, Java, and JavaScript scripts.
Proxy servers have some serious security disadvantages if the single port left open with the proxy server and then attackers can enumerate with it.
If there is an issue in establishing a connection then with the proxy server it is hard to troubleshoot and they are not compatible with all the network protocols.
We already discussed the cache increases the speed, but on the other hand, there are some disadvantages. The cache displays the display of the old contents.
Not all the proxies are good, you should spend a lot of time to find a right proxy. A good proxy chain only provides better performance.
Conclusion
Simply both the proxy and VPN were made to hide the internet traffic and with the VPN the traffic will be passed through a network tunnel, but the low-quality VPNs would expose serious threats.
The proxy servers are very hard to set up and they won’t encrypt the data, using a VPN and proxy can slow down the connection dramatically. When it comes to the encryption VPNs are the best and they offer encryption with industry standard keysize.
One should be very careful in picking a proxy server because attackers also do run the proxy servers to sniff the network traffic.
When it comes to a proxy, you can hide only the HTTP traffic, but with VPNs, you can hide the traffic sent through all the protocols.
If you are to compare VPN and Proxy which is better, it completely depends on your requirement. It doesn’t matter if you pick to use a proxy server or the VPN, but need to ensure the service you selected may solve the requirement
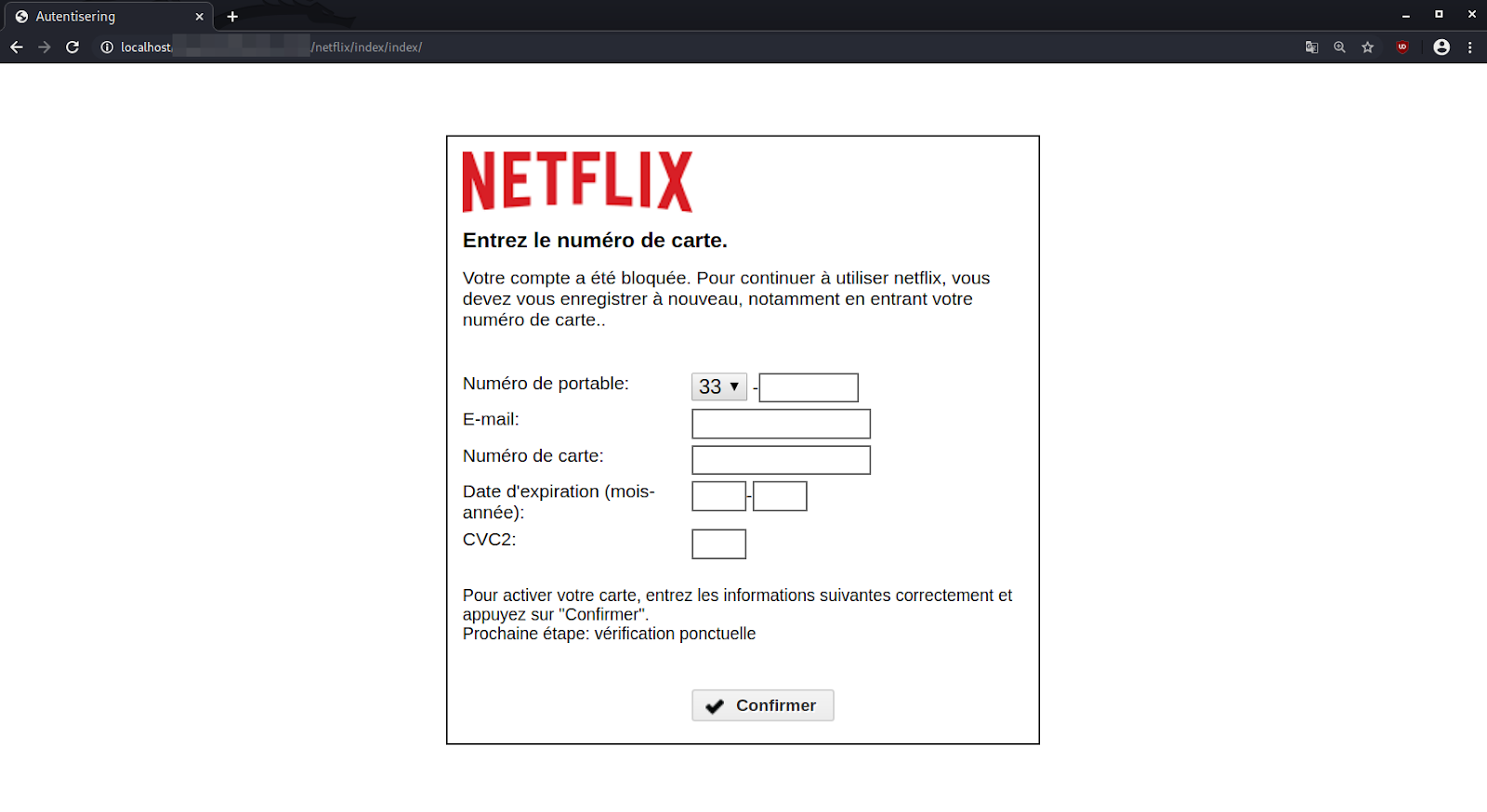
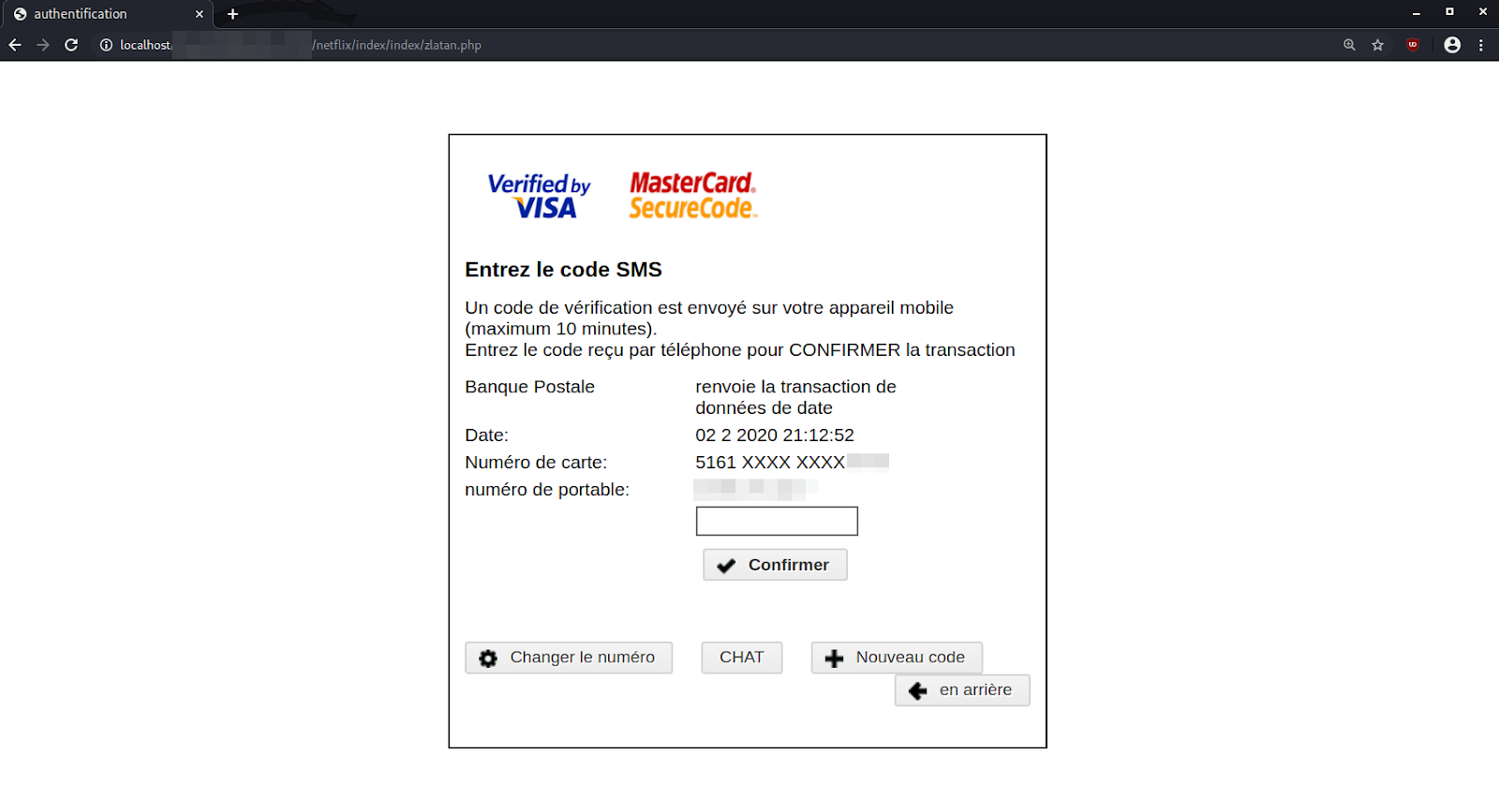
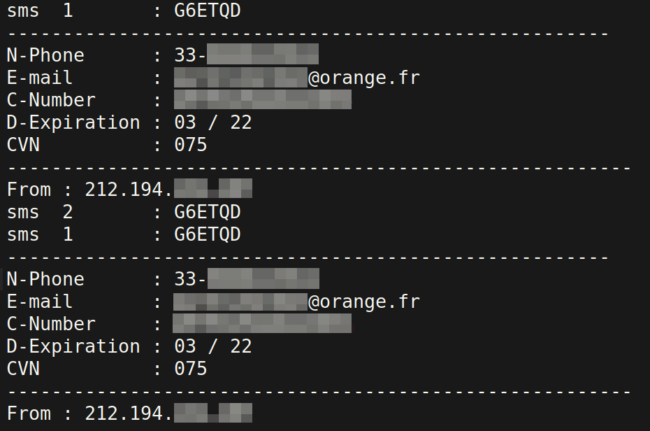 A generated .txt file within the phishing kit that contains the phished details
A generated .txt file within the phishing kit that contains the phished details
 Folding@home options
Folding@home options Folding@Home
Folding@Home Όταν μιλάμε για hacking επιθέσεις και παραβιάσεις συσκευών, ένα από τα πρώτα πράγματα που μας έρχονται στο μυαλό είναι τα passwords. Οι εδικοί
Όταν μιλάμε για hacking επιθέσεις και παραβιάσεις συσκευών, ένα από τα πρώτα πράγματα που μας έρχονται στο μυαλό είναι τα passwords. Οι εδικοί 
