By WAQAS HACKREAD
campaign.
The IT security researchers at Trustwave SpiderLabs have identified a new and tricky attack campaign utilizing especially designed USB dongle that acts as a keyboard. In their research, the Trustwave shared details of one of its clients in the US who received malicious USB dongle shipped to their company as a gift card from Best Buy.
The incident has received so much attention that the FBI had to issue a warning stating that this is the work of cybercrime syndicate known as Fin7, and it is specifically targeting businesses by sending them infected USB devices.
See: Employee infects US govt network with malware after visiting 9,000 porn sites
The attack work in such a way that once these devices are plugged into the PC it downloads and runs a JavaScript backdoor. This technique is usually associated with security researchers for training purposes and it is perhaps the first time that hackers have attempted to use it on a large scale.
According to Trustwave SpiderLabs’ vice president Ziv Mador, the company was notified about this campaign from one of their team members’ business associate, and that a US-based hospitality sector firm received the malicious USB dongle in February.
The USB drive was intelligently packaged by the attackers as the company that received the Best Buy $50 gift card with the drive revealed that the package contained a genuine-looking letter bearing the logo of Best Buy.
Best Buy company thanks you for being our regular customer for a long period of time, so we would like to send you a gift card in the amount of $50. You can spend it on any product from the list of items presented on a USB stick. Thank you again for choosing us!, said the letter sent to the company.
Here is a full preview of the letter:

Image provided by Trustwave
Furthermore, they were asked to spend the amount on different items, and the list of items was supposedly stored on the USB drive, which the recipient has to plug into the device to check the list. However, the recipient was well-trained and didn’t do as directed and instead, sent the device for further analysis.
Researchers maintain that this USB drive is an Arduino microcontroller ATMEGA32U4 and infected with GRIFFON malware. The USB is designed to behave like a USB keyboard primarily because such keyboards are compatible with almost all kinds of systems and injecting malicious commands is easier.
In this campaign, the USB drive executes an array of obscured PowerShell commands to upload the device’s system configuration data on a C&C server operated by the attacker(s) and wait for more instructions from the attacker(s).
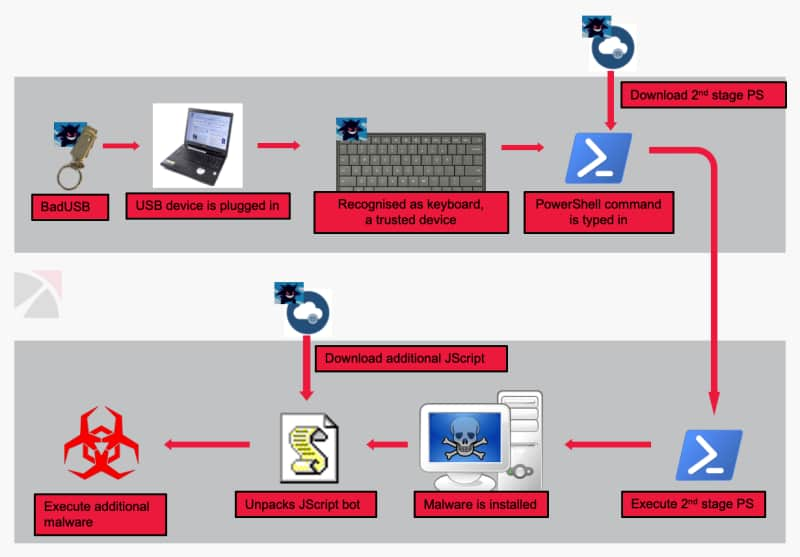
How the attack works – Image via Trustwave
Researchers urge that businesses must not insert any USB devices that they receive unexpectedly into their systems no matter how attractively it has been disguised or how large the attached gift card is.
See: 8 Technologies That Can Hack Into Your Offline Computer and Phone
While this time it is the FIN7 hacking group sending out malicious USBs, in May 2017, IBM sent off USB sticks infected with malware while in September 2018, Schneider electric also shipped USB drives loaded with malware. In January 2018, Police in Taiwan distributed malware-infected USBs as cybersecurity quiz prizes – oh the irony!
If you care for your business, you need to educate yourself and employees on cyber security. Check our in-depth post explaining how a USB could become a security risk for your device and impact your business

Image provided by Trustwave
Furthermore, they were asked to spend the amount on different items, and the list of items was supposedly stored on the USB drive, which the recipient has to plug into the device to check the list. However, the recipient was well-trained and didn’t do as directed and instead, sent the device for further analysis.
Researchers maintain that this USB drive is an Arduino microcontroller ATMEGA32U4 and infected with GRIFFON malware. The USB is designed to behave like a USB keyboard primarily because such keyboards are compatible with almost all kinds of systems and injecting malicious commands is easier.
In this campaign, the USB drive executes an array of obscured PowerShell commands to upload the device’s system configuration data on a C&C server operated by the attacker(s) and wait for more instructions from the attacker(s).

How the attack works – Image via Trustwave
Researchers urge that businesses must not insert any USB devices that they receive unexpectedly into their systems no matter how attractively it has been disguised or how large the attached gift card is.
See: 8 Technologies That Can Hack Into Your Offline Computer and Phone
While this time it is the FIN7 hacking group sending out malicious USBs, in May 2017, IBM sent off USB sticks infected with malware while in September 2018, Schneider electric also shipped USB drives loaded with malware. In January 2018, Police in Taiwan distributed malware-infected USBs as cybersecurity quiz prizes – oh the irony!
If you care for your business, you need to educate yourself and employees on cyber security. Check our in-depth post explaining how a USB could become a security risk for your device and impact your business
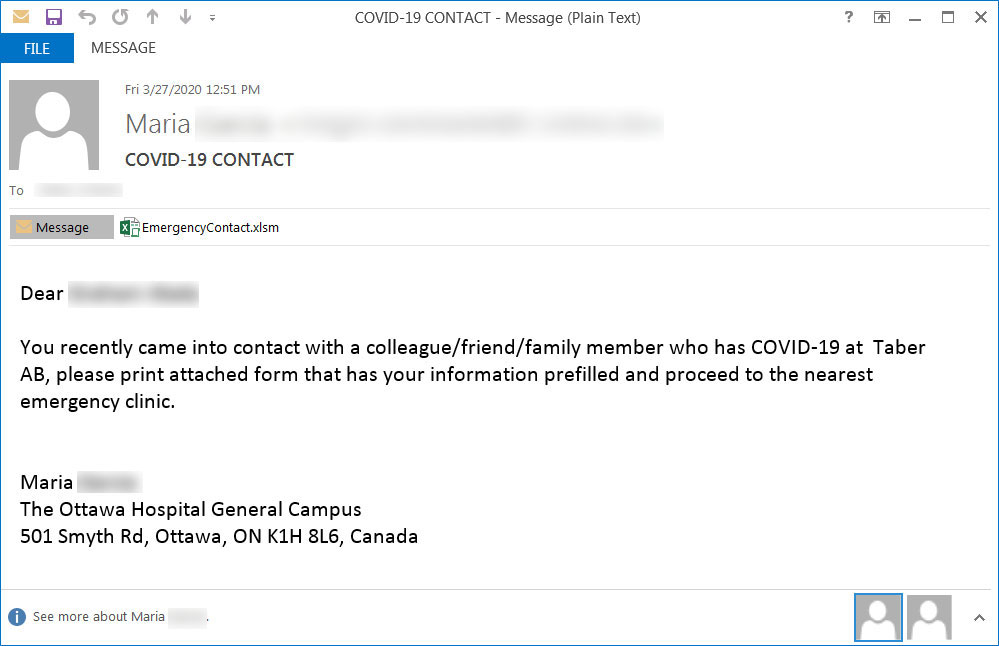 Coronavirus-themed phishing email
Coronavirus-themed phishing email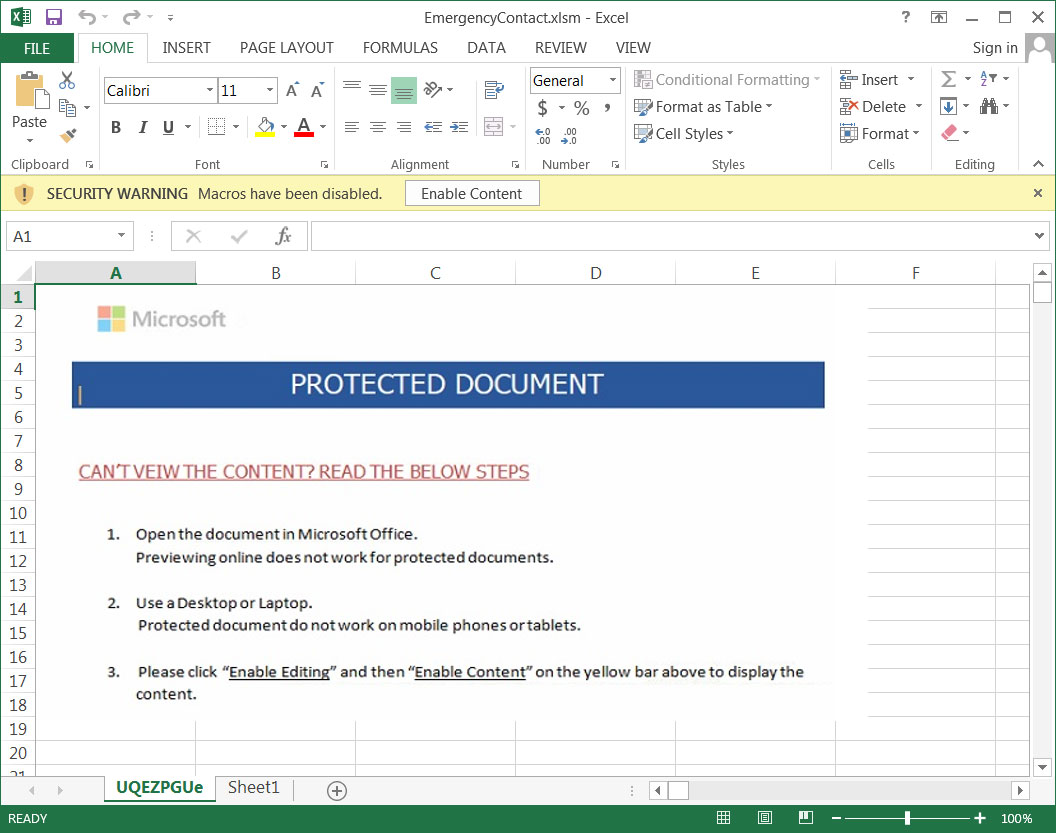 Malicious attachment
Malicious attachment