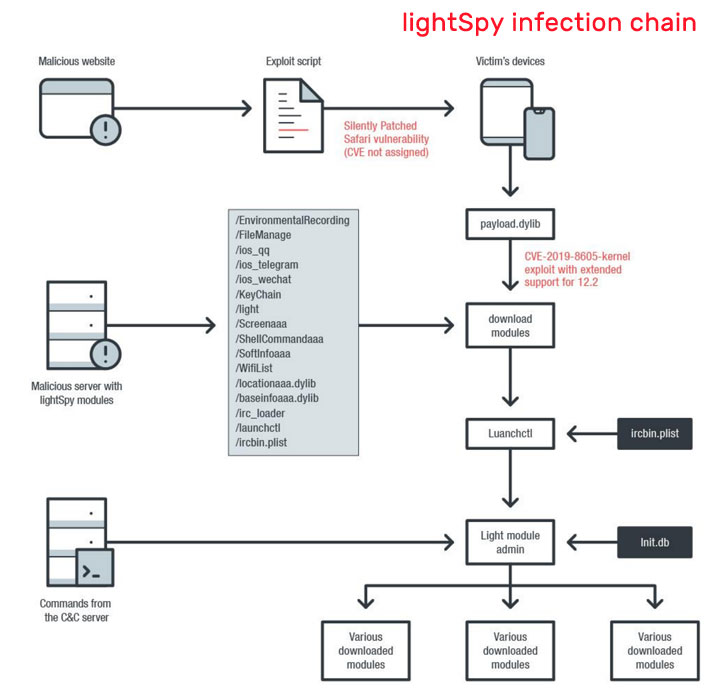
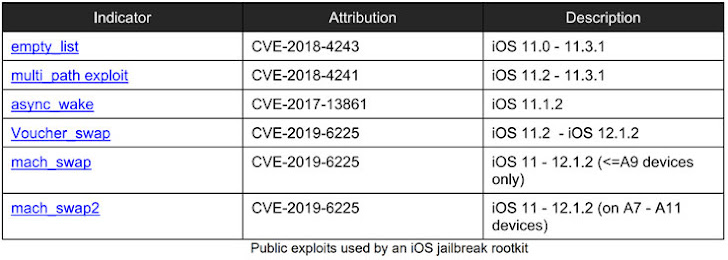
By Steven J. Vaughan-Nichols for Networking | March 30, 2020
In the newly released Linux 5.6 kernel, you'll finally find the long anticipated open-source Virtual Private Network, WireGuard.
Linus Torvalds has released the newest version of the Linux 5.6. It includes many new and neat features like USB4 support, a fix for the 32-bit Epoch problem, multi-path TCP, and numerous driver patches. The biggest news of all s that Linux now has the popular open-source Virtual Private Network (VPN) WireGuard baked in.
WireGuard is a radical new approach to VPNs. With its minimal codebase -- about 4,000 lines of code -- it's much easier to debug and secure than its rivals such as OpenVPN with its over 100,000 lines.
Torvalds himself loves WireGuard for its simplicity. Long before he incorporated WireGuard into Linux, Tovalids said "Can I just once again state my love for it and hope it gets merged soon? Maybe the code isn't perfect, but I've skimmed it, and compared to the horrors that are OpenVPN and IPSec, it's a work of art."
It may be simple, but it supports the most up-to-date cryptography technologies such as the Noise protocol framework, Curve25519, ChaCha20, Poly1305, BLAKE2, SipHash24, and HKD. It's also been shown to be secure by an academic mechanized cryptographic proof.
The final major hurdle WireGuard faced in its acceptance was maintaining compatibility with Linux's built-in cryptographic subsystem. In the end, WireGuard's primary developer Jack Donenfeld built-in cryptographic compatibility. The traditional subsystem also now includes features from Donenfeld's Zinc cryptographic library.
While it's home is on Linux, WireGuard is designed as a general-purpose VPN for everything from Internet-of-Things (IoT) devices to supercomputers. It's also cross-platform with support for the BSD Unixes, MacOS, Windows on computers, and Android and iOS on smartphones.
Linux users, who don't usually touch early Linux kernel builds, will soon be able to give it a try. Donenfeld wrote: "The usual up-to-date distributions like Arch, Gentoo, and Fedora 32 will be getting WireGuard automatically by virtue of having 5.6."
But even if you don't run leading, bleeding-edge Linux distros like these, you'll be getting WireGuard soon, too. Donenfeld added: "On the backports front, WireGuard was backported to Ubuntu 20.04 and Debian Buster." It may end up backported to Linux 5.4, long-term support (LTS) kernel. This will bring WireGuard to almost all 2020 Linux distro releases.
Simple, fast, and secure. WireGuard promises to not only be the future of Linux VPNs but of all VPN programs. Some companies, such as Mullvad VPN, are always shipping it. Others, all the others, soon will be.
WireGuard is a radical new approach to VPNs. With its minimal codebase -- about 4,000 lines of code -- it's much easier to debug and secure than its rivals such as OpenVPN with its over 100,000 lines.
Torvalds himself loves WireGuard for its simplicity. Long before he incorporated WireGuard into Linux, Tovalids said "Can I just once again state my love for it and hope it gets merged soon? Maybe the code isn't perfect, but I've skimmed it, and compared to the horrors that are OpenVPN and IPSec, it's a work of art."
It may be simple, but it supports the most up-to-date cryptography technologies such as the Noise protocol framework, Curve25519, ChaCha20, Poly1305, BLAKE2, SipHash24, and HKD. It's also been shown to be secure by an academic mechanized cryptographic proof.
The final major hurdle WireGuard faced in its acceptance was maintaining compatibility with Linux's built-in cryptographic subsystem. In the end, WireGuard's primary developer Jack Donenfeld built-in cryptographic compatibility. The traditional subsystem also now includes features from Donenfeld's Zinc cryptographic library.
While it's home is on Linux, WireGuard is designed as a general-purpose VPN for everything from Internet-of-Things (IoT) devices to supercomputers. It's also cross-platform with support for the BSD Unixes, MacOS, Windows on computers, and Android and iOS on smartphones.
Linux users, who don't usually touch early Linux kernel builds, will soon be able to give it a try. Donenfeld wrote: "The usual up-to-date distributions like Arch, Gentoo, and Fedora 32 will be getting WireGuard automatically by virtue of having 5.6."
But even if you don't run leading, bleeding-edge Linux distros like these, you'll be getting WireGuard soon, too. Donenfeld added: "On the backports front, WireGuard was backported to Ubuntu 20.04 and Debian Buster." It may end up backported to Linux 5.4, long-term support (LTS) kernel. This will bring WireGuard to almost all 2020 Linux distro releases.
Simple, fast, and secure. WireGuard promises to not only be the future of Linux VPNs but of all VPN programs. Some companies, such as Mullvad VPN, are always shipping it. Others, all the others, soon will be.

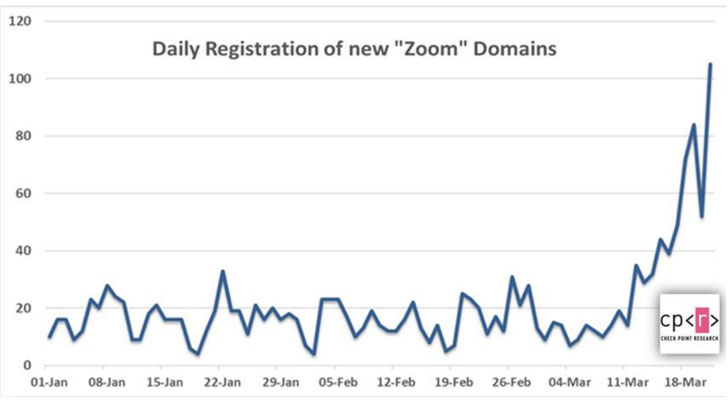

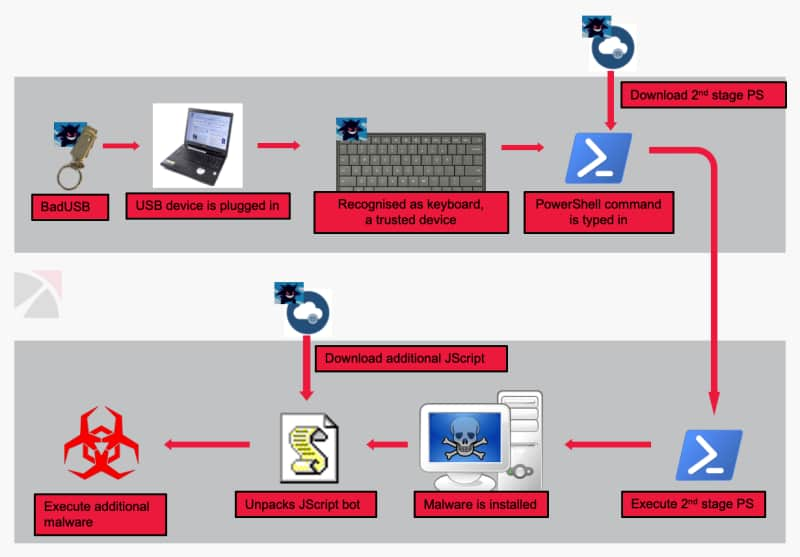
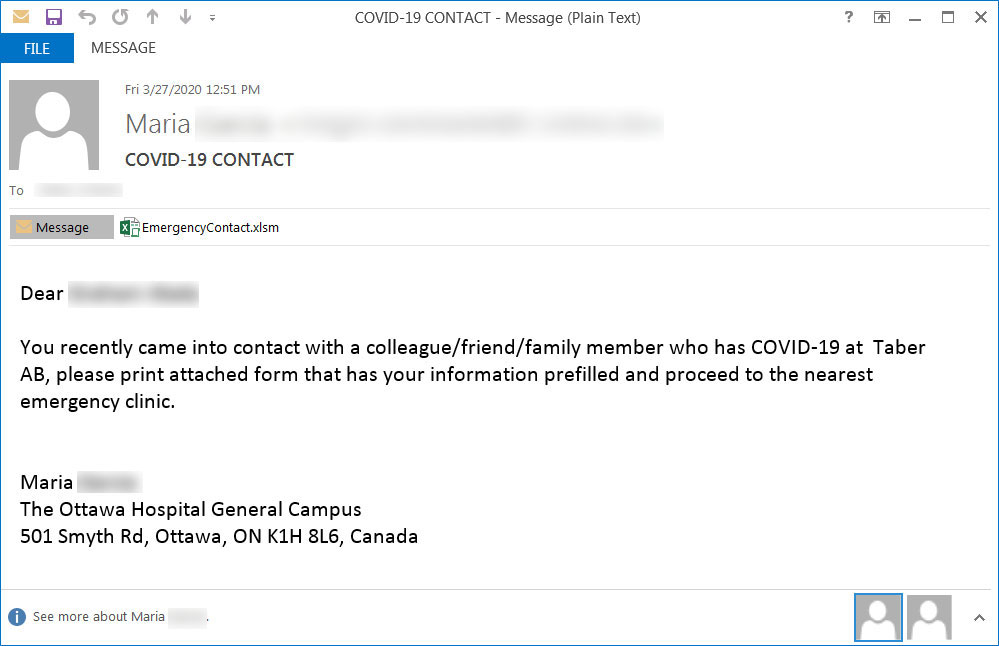 Coronavirus-themed phishing email
Coronavirus-themed phishing email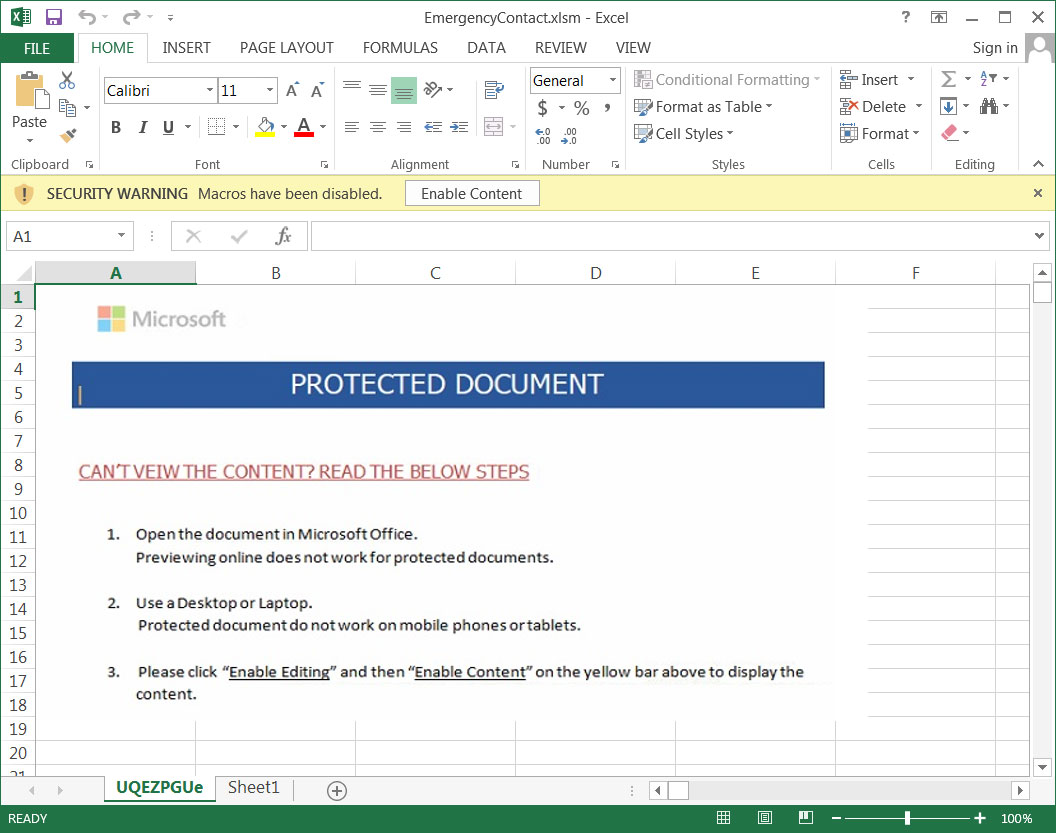 Malicious attachment
Malicious attachment