Αν δεν ξέρετε πώς να κάνετε δωρεάν αναβάθμιση στα 10, ή γνωρίζετε κάποιον που χρειάζεται βοήθεια, δείτε αναλυτικά τη διαδικασία video
Posted by DASOS security info on Thursday, February 13, 2020
Thursday, February 13, 2020
Πώς να κάνετε δωρεάν αναβάθμιση στα win10!! video
Tuesday, February 11, 2020
Critical Android Bluetooth Flaw Exploitable without User Interaction
By
Ionut Ilascu February 6, 2020 07:44 PM 3

Android users are urged to apply the latest security patches released for the operating system on Monday that address a critical vulnerability in the Bluetooth subsystem.
An attacker could leverage the security flaw, now identified as CVE-2020-0022 without user participation to run arbitrary code on the device with the elevated privileges of the Bluetooth daemon when the wireless module is active.
Short-distance worm
Discovered and reported by Jan Ruge at the Technische Universität Darmstadt, Secure Mobile Networking Lab, the bug is considered critical on Android Oreo (8.0 and 8.1) and Pie (9) because exploiting it leads to code execution.
According to Ruge, attackers could use this security fault to spread malware from one vulnerable device to another, like a worm. However, the transmission is limited to the short distance covered by Bluetooth.
The Android security bulletin notes that CVE-2020-0022 "could enable a remote attacker using a specially crafted transmission to execute arbitrary code within the context of a privileged process."
The only prerequisite for taking advantage of the issue is knowing the Bluetooth MAC address. This is not difficult to find, though.
"For some devices, the Bluetooth MAC address can be deduced from the WiFi MAC address," says the researcher on the the blog site of German IT security consultant ERNW.
On Android 10, the severity rating drops to moderate since it all it does is crash the Bluetooth daemon, the researcher says. Android versions earlier than 8.0 may also be affected but the impact on them has not been assessed.
Technical details, PoC to be published
The severity of the issue is what keeps the researcher from disclosing technical details and proof of concept (PoC) code demonstrating the findings.
Despite a patch being available, OEM vendors and mobile carriers also have to push it to user terminals. For devices still under support, it can take weeks until the update rolls out.
If a patch does not become available, Ruge recommends enabling Bluetooth only "if strictly necessary." If you need to activate it, consider keeping the device non-discoverable, a feature that hides it from other gadgets looking for a pair.
Ruge says that a technical report will be available for this vulnerability "as soon as we are confident that patches have reached the end users."
Ionut Ilascu February 6, 2020 07:44 PM 3

Android users are urged to apply the latest security patches released for the operating system on Monday that address a critical vulnerability in the Bluetooth subsystem.
An attacker could leverage the security flaw, now identified as CVE-2020-0022 without user participation to run arbitrary code on the device with the elevated privileges of the Bluetooth daemon when the wireless module is active.
Short-distance worm
Discovered and reported by Jan Ruge at the Technische Universität Darmstadt, Secure Mobile Networking Lab, the bug is considered critical on Android Oreo (8.0 and 8.1) and Pie (9) because exploiting it leads to code execution.
According to Ruge, attackers could use this security fault to spread malware from one vulnerable device to another, like a worm. However, the transmission is limited to the short distance covered by Bluetooth.
The Android security bulletin notes that CVE-2020-0022 "could enable a remote attacker using a specially crafted transmission to execute arbitrary code within the context of a privileged process."
The only prerequisite for taking advantage of the issue is knowing the Bluetooth MAC address. This is not difficult to find, though.
"For some devices, the Bluetooth MAC address can be deduced from the WiFi MAC address," says the researcher on the the blog site of German IT security consultant ERNW.
On Android 10, the severity rating drops to moderate since it all it does is crash the Bluetooth daemon, the researcher says. Android versions earlier than 8.0 may also be affected but the impact on them has not been assessed.
Technical details, PoC to be published
The severity of the issue is what keeps the researcher from disclosing technical details and proof of concept (PoC) code demonstrating the findings.
Despite a patch being available, OEM vendors and mobile carriers also have to push it to user terminals. For devices still under support, it can take weeks until the update rolls out.
If a patch does not become available, Ruge recommends enabling Bluetooth only "if strictly necessary." If you need to activate it, consider keeping the device non-discoverable, a feature that hides it from other gadgets looking for a pair.
Ruge says that a technical report will be available for this vulnerability "as soon as we are confident that patches have reached the end users."
Νέο κύμα του Emotet Malware χακάρει δίκτυα Wi-Fi!
10 Φεβρουαρίου, 2020, 5:36 μμ by Teo Ehc Leave a Comment
Ένα νέο κύμα του malware Emotet με το νέο Wi-Fi Spreader εκμεταλλεύεται το interface wlanAPI για να απαριθμήσει όλα τα δίκτυα Wi-Fi στην περιοχή και να εξαπλωθεί η μόλυνση.
Το Emotet είναι ένα Trojan banking που εντοπίστηκε το 2014 και σχεδιάστηκε για να κλέβει ευαίσθητες και ιδιωτικές πληροφορίες.
Είναι ένα από τα πιο επικίνδυνα malware και είναι σε θέση να αποδώσει payloads βασισμένα σε συγκεκριμένα tasks.
Το Emotet διανέμεται κυρίως μέσω τεχνικών social engineering όπως τα emails με links για να κατέβει το malware.
Με τη νέα καμπάνια Emotet καταφθάνει ένα νέο Wi-Fi Spreader module που μεταφορτώνεται στο σύστημα C:\ProgramData. Το ληφθέν δυαδικό αρχείο περιέχει ένα RAR αυτόματης εξαγωγής που διαθέτει δυο δυαδικά αρχεία (service.exe και worm.exe) για τη διάδοση του μέσω Wi-Fi.

Το worm.exe είναι το εκτελέσιμο αρχείο που χρησιμοποιείται για την εξάπλωση του malware, αφού εκτελείται, αντιγράφει το service.exe σε μια μεταβλητή για τη χρήση του κατά τη διάδοση.
Στη συνέχεια καλεί την κλάση wlanAPI.dll που χρησιμοποιείται από το Native Wi-Fi για τη διαχείριση των προφίλ και των συνδέσεων ασύρματου δικτύου για τη διάδοση του malware σε άλλα δίκτυα.

“Το Worm απαριθμεί όλες τις συσκευές Wi-Fi που είναι επί του παρόντος ενεργοποιημένες στον τοπικό υπολογιστή, το οποίο επιστρέφει σε μια σειρά δομών. Αυτές οι δομές περιέχουν όλες τις πληροφορίες που σχετίζονται με τη συσκευή Wi-Fi, συμπεριλαμβανομένου του GUID και της περιγραφής της συσκευής”, διαβάζουμε στην ανάλυση του worm.
Συγκεντρώνει πιθανές πληροφορίες από όλα τα διαθέσιμα δίκτυα Wi-Fi που υπάρχουν στη λίστα των δικτύων.

Σπάζοντας το αδύναμο δίκτυο Wi-Fi
Μόλις συνδεθεί με το δίκτυο Wi-Fi, απαριθμεί τους χρήστες και επιχειρεί brute-force για όλους τους χρήστες του δικτύου.
Στη συνέχεια, το Service.exe είναι το payload που έχει εγκατασταθεί από το worm.exe στο μηχάνημα, μόλις εγκατασταθεί επικοινωνεί με το server C2 και εκτελεί το δυαδικό ενσωματωμένο στο service.exe.
Προηγουμένως, το Emotet, ο οποίος γνωρίζει ότι διανέμεται μόνο μέσω δικτύων malspam και μολυσμένων δικτύων, με αυτόν τον νέο loader εξαπλώνεται μέσω κοντινών ασύρματων δικτύων που χρησιμοποιούν αδύναμους κωδικούς πρόσβασης.
Phishing Attack Disables Google Play Protect, Drops Anubis Trojan
By
Sergiu Gatl an February 6, 2020 02:36 PM 1
Android users are targeted in a phishing campaign that will infect their devices with the Anubis banking Trojan that can steal financial information from more than 250 banking and shopping applications.
The campaign uses a devious method to get the potential victims to install the malware on their devices: it asks them to enable Google Play Protect while actually disabling it after being granted permissions on the device.
To deliver the malware, the attackers use a malicious link embedded within the phishing email that will download an APK file camouflaged as an invoice as Cofense found.
After being asked if he wants to use Google Play Protect and installing the downloaded APK, the victim's device will be infected with the Anubis Trojan.
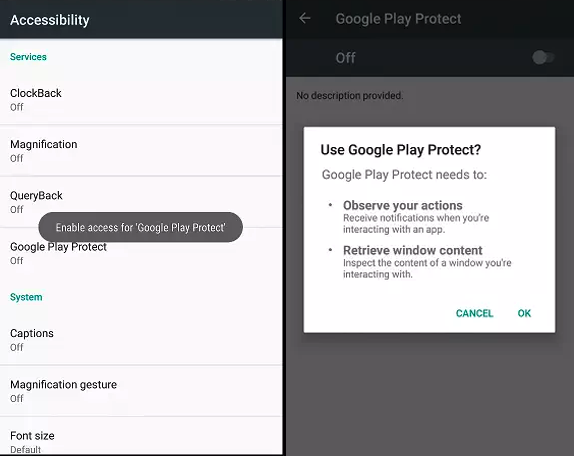 Google Play Protect used as cover (Cofense)
Google Play Protect used as cover (Cofense)Targets over 250 financial applications
Cofense discovered that, once the Android smartphone or tablet is compromised, Anubis will start harvesting "a list of installed applications to compare the results against a list of targeted applications.
The malware mainly targets banking and financial applications, but also looks for popular shopping apps such as eBay or Amazon.
Once an application has been identified, Anubis overlays the original application with a fake login page to capture the user’s credentials."
After analyzing the malware's source code, Cofense found that the banking Trojan has a wide range of capabilities included but not limited to:
• capturing screenshots
• toggling off and altering administration settings
• disabling Google's Play Protect built-in malware protection for Android
• recording audio
• making calls and sending SMS
• stealing the contact list
• stealing the contacts from the addressbook
• receiving commands from its operators via Telegram and Twitter
• controlling the device over a VNC
• opening URLs
• locking device screen
• and collecting device and location information
The malware also comes with a keylogger module that can capture keystrokes from every app installed on the compromised Android device.
However, this keylogging module has to be specifically enabled by the attackers via a command sent through Anubis' command and control (C2) server.
Also comes with a ransomware module
On top of all of these, Anubis is also capable of encrypting files on the internal storage and from external drives using the RC4 stream cipher with the help of a dedicated ransomware module, adding the .AnubisCrypt extension to the encrypted files and sending it to the C2 server.
Anubis Trojan samples with ransomware capabilities are not new, as Sophos previously discovered Anubis-infected apps in the Play Store in August 2018 that also added the .AnubisCrypt file extension to the encrypted files.
"Remember, this runs on a phone, which is even less likely to be backed up than a laptop or desktop, and more likely to have personal photos or other valuable data," Sophos said at the time.
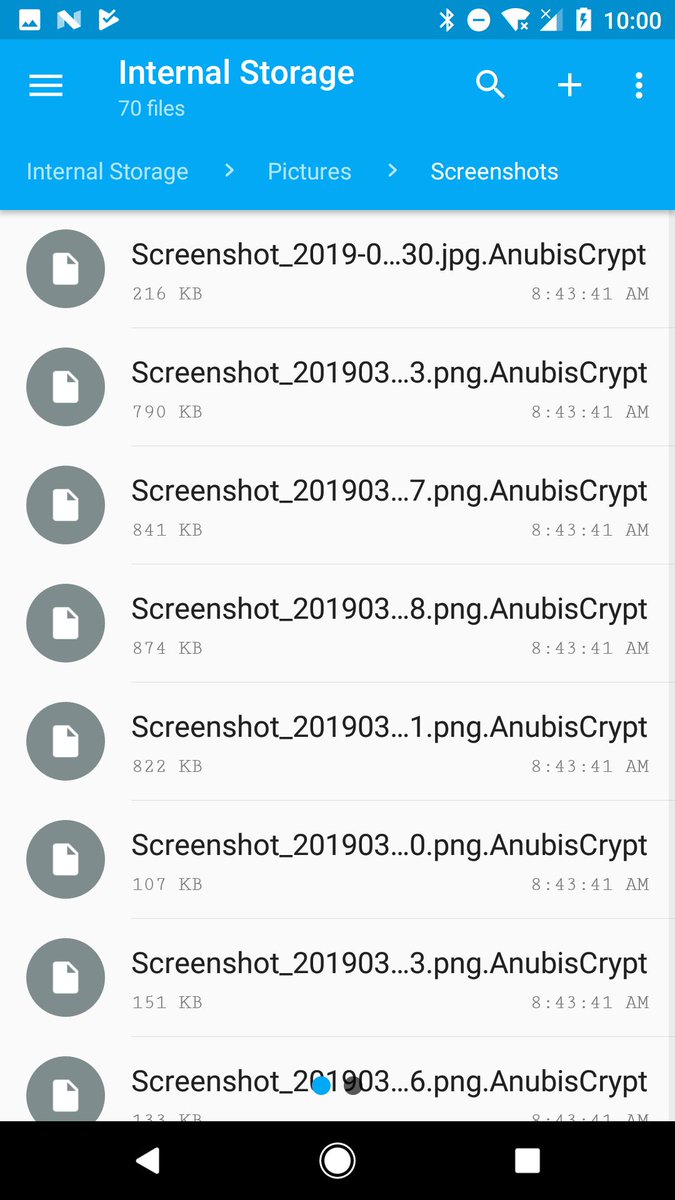 AnubisCrypt encrypted files
AnubisCrypt encrypted filesAccording to the Cofense report, "this version of Anubis is built to run on several iterations of the Android operating system, dating back to version 4.0.3, which was released in 2012."
Trend Micro's researchers also found in January 2019 that the Anubis Trojan was used in a campaign that targeted 377 bank apps from 93 countries all over the globe, with banks like Santander, Citibank, RBS, and Natwest, as well as shopping apps such as Amazon, eBay, and PayPal being listed as targets.
An extensive list of indicators of compromised (IOCs) including hashes of the malicious APK installer used in the campaign, associated URLs, and all application IDs for the apps targeted by this Anubis sample is available at the end of Cofense's report.
Saturday, February 8, 2020
National Cyber Awareness System Alerts Emotet Malware
Systems Affected
Network Systems
Overview
Emotet is an advanced, modular banking Trojan that primarily functions as a downloader or dropper of other banking Trojans. Emotet continues to be among the most costly and destructive malware affecting state, local, tribal, and territorial (SLTT) governments, and the private and public sectors.
This joint Technical Alert (TA) is the result of Multi-State Information Sharing & Analysis Center (MS-ISAC) analytic efforts, in coordination with the Department of Homeland Security (DHS) National Cybersecurity and Communications Integration Center (NCCIC).
Description
Emotet continues to be among the most costly and destructive malware affecting SLTT governments. Its worm-like features result in rapidly spreading network-wide infection, which are difficult to combat. Emotet infections have cost SLTT governments up to $1 million per incident to remediate.
Emotet is an advanced, modular banking Trojan that primarily functions as a downloader or dropper of other banking Trojans. Additionally, Emotet is a polymorphic banking Trojan that can evade typical signature-based detection. It has several methods for maintaining persistence, including auto-start registry keys and services. It uses modular Dynamic Link Libraries (DLLs) to continuously evolve and update its capabilities. Furthermore, Emotet is Virtual Machine-aware and can generate false indicators if run in a virtual environment.
Emotet is disseminated through malspam (emails containing malicious attachments or links) that uses branding familiar to the recipient; it has even been spread using the MS-ISAC name. As of July 2018, the most recent campaigns imitate PayPal receipts, shipping notifications, or “past-due” invoices purportedly from MS-ISAC. Initial infection occurs when a user opens or clicks the malicious download link, PDF, or macro-enabled Microsoft Word document included in the malspam. Once downloaded, Emotet establishes persistence and attempts to propagate the local networks through incorporated spreader modules.

Figure 1: Malicious email distributing Emotet
Currently, Emotet uses five known spreader modules: NetPass.exe, WebBrowserPassView, Mail PassView, Outlook scraper, and a credential enumerator.
NetPass.exe is a legitimate utility developed by NirSoft that recovers all network passwords stored on a system for the current logged-on user. This tool can also recover passwords stored in the credentials file of external drives.
Outlook scraper is a tool that scrapes names and email addresses from the victim’s Outlook accounts and uses that information to send out additional phishing emails from the compromised accounts.
WebBrowserPassView is a password recovery tool that captures passwords stored by Internet Explorer, Mozilla Firefox, Google Chrome, Safari, and Opera and passes them to the credential enumerator module.
Mail PassView is a password recovery tool that reveals passwords and account details for various email clients such as Microsoft Outlook, Windows Mail, Mozilla Thunderbird, Hotmail, Yahoo! Mail, and Gmail and passes them to the credential enumerator module.
Credential enumerator is a self-extracting RAR file containing two components: a bypass component and a service component. The bypass component is used for the enumeration of network resources and either finds writable share drives using Server Message Block (SMB) or tries to brute force user accounts, including the administrator account. Once an available system is found, Emotet writes the service component on the system, which writes Emotet onto the disk. Emotet’s access to SMB can result in the infection of entire domains (servers and clients).

Figure 2: Emotet infection process
To maintain persistence, Emotet injects code into explorer.exe and other running processes. It can also collect sensitive information, including system name, location, and operating system version, and connects to a remote command and control server (C2), usually through a generated 16-letter domain name that ends in “.eu.” Once Emotet establishes a connection with the C2, it reports a new infection, receives configuration data, downloads and runs files, receives instructions, and uploads data to the C2 server.
Emotet artifacts are typically found in arbitrary paths located off of the AppData\Local and AppData\Roaming directories. The artifacts usually mimic the names of known executables. Persistence is typically maintained through Scheduled Tasks or via registry keys. Additionally, Emotet creates randomly-named files in the system root directories that are run as Windows services. When executed, these services attempt to propagate the malware to adjacent systems via accessible administrative shares.
Note: it is essential that privileged accounts are not used to log in to compromised systems during remediation as this may accelerate the spread of the malware.
Example Filenames and Paths:
C:\Users\<username>\AppData \Local\Microsoft\Windows\shedaudio.exe
C:\Users\<username>\AppData\Roaming\Macromedia\Flash Player\macromedia\bin\flashplayer.exe
Typical Registry Keys:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\Software\Wow6432Node\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
System Root Directories:
C:\Windows\11987416.exe
C:\Windows\System32\46615275.exe
C:\Windows\System32\shedaudio.exe
C:\Windows\SysWOW64\f9jwqSbS.exe
Impact
Negative consequences of Emotet infection include
temporary or permanent loss of sensitive or proprietary information,
disruption to regular operations,
financial losses incurred to restore systems and files, and
potential harm to an organization’s reputation.
Solution
NCCIC and MS-ISAC recommend that organizations adhere to the following general best practices to limit the effect of Emotet and similar malspam:
Use Group Policy Object to set a Windows Firewall rule to restrict inbound SMB communication between client systems. If using an alternative host-based intrusion prevention system (HIPS), consider implementing custom modifications for the control of client-to-client SMB communication. At a minimum, create a Group Policy Object that restricts inbound SMB connections to clients originating from clients.
Use antivirus programs, with automatic updates of signatures and software, on clients and servers.
Apply appropriate patches and updates immediately (after appropriate testing).
Implement filters at the email gateway to filter out emails with known malspam indicators, such as known malicious subject lines, and block suspicious IP addresses at the firewall.
If your organization does not have a policy regarding suspicious emails, consider creating one and specifying that all suspicious emails should be reported to the security or IT department.
Mark external emails with a banner denoting it is from an external source. This will assist users in detecting spoofed emails.
Provide employees training on social engineering and phishing. Urge employees not to open suspicious emails, click links contained in such emails, or post sensitive information online, and to never provide usernames, passwords, or personal information in answer to any unsolicited request. Educate users to hover over a link with their mouse to verify the destination prior to clicking on the link.
Consider blocking file attachments that are commonly associated with malware, such as .dll and .exe, and attachments that cannot be scanned by antivirus software, such as .zip files.
Adhere to the principle of least privilege, ensuring that users have the minimum level of access required to accomplish their duties. Limit administrative credentials to designated administrators.
Implement Domain-Based Message Authentication, Reporting & Conformance (DMARC), a validation system that minimizes spam emails by detecting email spoofing using Domain Name System (DNS) records and digital signatures.
If a user or organization believes they may be infected, NCCIC and MS-ISAC recommend running an antivirus scan on the system and taking action to isolate the infected workstation based on the results. If multiple workstations are infected, the following actions are recommended:
Identify, shutdown, and take the infected machines off the network;
Consider temporarily taking the network offline to perform identification, prevent reinfections, and stop the spread of the malware;
Do not log in to infected systems using domain or shared local administrator accounts;
Reimage the infected machine(s);
After reviewing systems for Emotet indicators, move clean systems to a containment virtual local area network that is segregated from the infected network;
Issue password resets for both domain and local credentials;
Because Emotet scrapes additional credentials, consider password resets for other applications that may have had stored credentials on the compromised machine(s);
Identify the infection source (patient zero); and
Review the log files and the Outlook mailbox rules associated with the infected user account to ensure further compromises have not occurred. It is possible that the Outlook account may now have rules to auto-forward all emails to an external email address, which could result in a data breach.
Reporting
MS-ISAC is the focal point for cyber threat prevention, protection, response, and recovery for the nation’s SLTT governments. More information about this topic, as well as 24/7 cybersecurity assistance for SLTT governments, is available by phone at 866-787-4722, by email at SOC@cisecurity.org, or on MS-ISAC’s website at https://msisac.cisecurity.org/.
To report an intrusion and request resources for incident response or technical assistance, contact NCCIC by email at NCCICCustomerService@hq.dhs.gov or by phone at 888-282-0870.
Subscribe to:
Posts (Atom)