By Ionut Ilascu February 28, 2020 02:12 PM 0

A group of hackers is using the remote desktop ActiveX control in Word documents to automatically execute on Windows 10 a malware downloader called Ostap that was seen recently adopted by TrickBot for delivery.
Security researchers have found dozens of files that delivered the first malware payload, indicating a larger campaign.
Starts with phishing
Ostap, extensively analyzed by Bromium researchers, is delivered via a Word document laced with malicious macro code and including an image that allegedly showed encrypted content. This is the ruse to trick victims into enabling macros in the document.
The threat actor delivered the malicious documents via phishing emails disguised as notifications of a missing payment. In the attachment is the fake invoice referred to in the message.
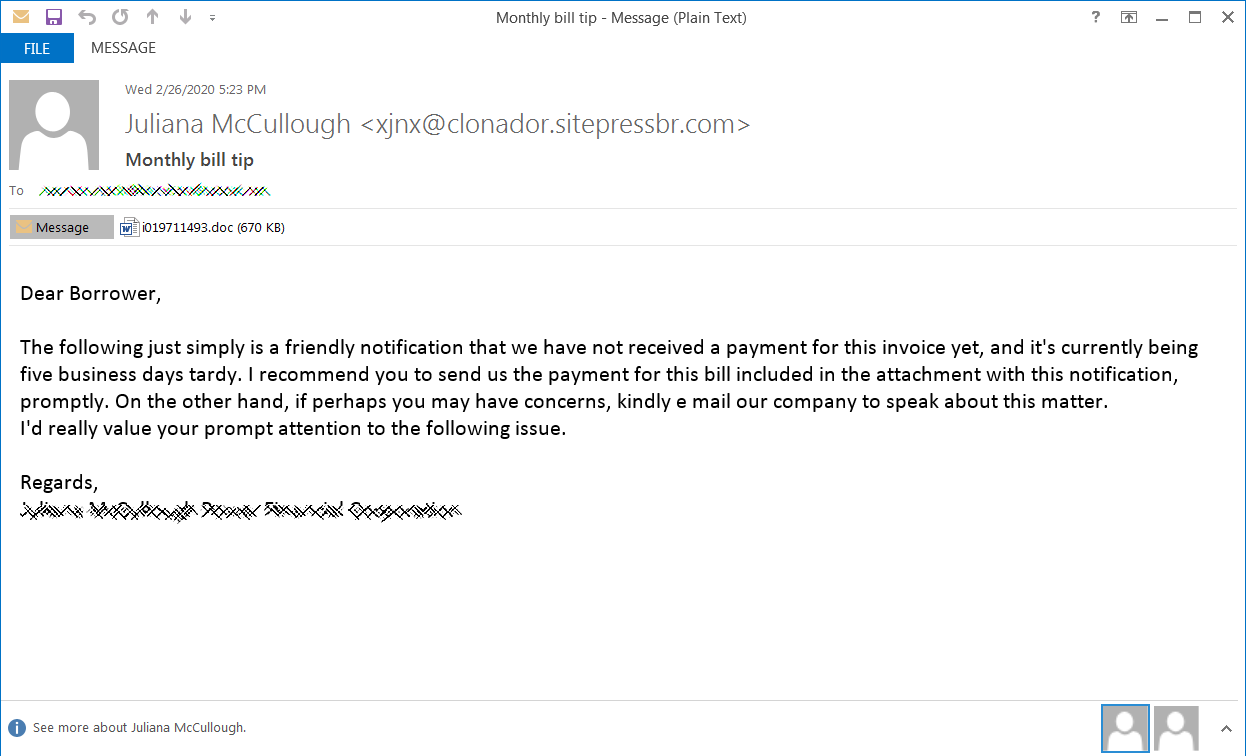
Security researchers at Morphisec analyzed the poisoned docs and noticed that there was an ActiveX control hidden below the embedded image.
A closer look revealed that the threat actor used the MsRdpClient10NotSafeForScripting class, which is used for remote control. Windows 10 is the minimum supported client and Windows Server 2016 is the minimum supported server.
ActiveX controls can be added to text or drawing layers in Word documents to make them interactive.
Clever delivery and execution
In a report today, Michael Gorelik of Morphisec writes that the JavaScript code for Ostap downloader is present in the document in font that has the same color as the background, making it invisible to the human eye.
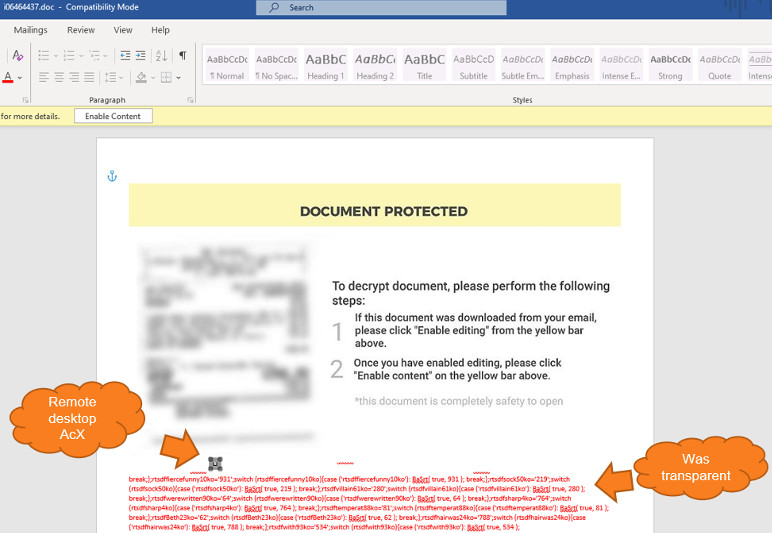
Another interesting finding is that the attackers did not populate the "server" field in the MsRdpClient10NotSafeForScripting class, needed to establish a connection with a remote desktop server.
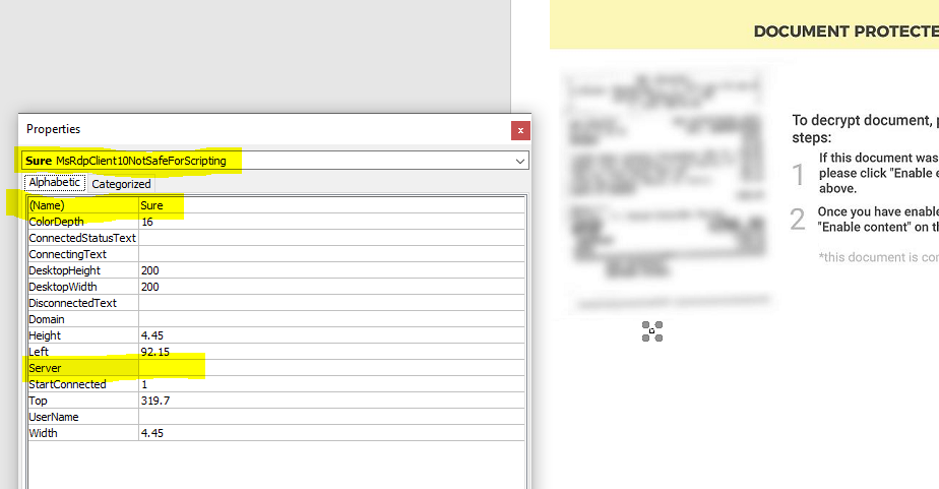
This was not a lapse from the attackers as the error that occurs helps execute their malicious code at a later time, thus evading detection.
When inspecting the macro, the researchers found that the "_OnDisconnected" function acts as a trigger but only after an error is returned for failing to connect to a non-existent server.
"The OSTAP will not execute unless the error number matches exactly to "disconnectReasonDNSLookupFailed" (260); the OSTAP wscript command is concatenated with a combination of characters that are dependent on the error number calculation." - Michael Gorelik, Morphisec
The backdoor is then executed immediately after taking the form of a .BAT file and the document form is closed.
Gorelik told BleepingComputer that this actor is not the only one relying on ActiveX control to execute malware. Other actors seen in January used the OnConnecting method that is easier to detect.
By contrast, the OnDiconnected method needs a specific return value and there is also a delay while the DNS lookup completes. This works to the attacker's advantage because scanners may miss the malicious activity and mark the file as benign.
[Update 02/28/2020, 16:01 EST]: Article updated to reflect a correction from Morphisec about misidentifying Ostap downloader with Griffon backdoor that is typically used by FIN7 threat actor.

A group of hackers is using the remote desktop ActiveX control in Word documents to automatically execute on Windows 10 a malware downloader called Ostap that was seen recently adopted by TrickBot for delivery.
Security researchers have found dozens of files that delivered the first malware payload, indicating a larger campaign.
Starts with phishing
Ostap, extensively analyzed by Bromium researchers, is delivered via a Word document laced with malicious macro code and including an image that allegedly showed encrypted content. This is the ruse to trick victims into enabling macros in the document.
The threat actor delivered the malicious documents via phishing emails disguised as notifications of a missing payment. In the attachment is the fake invoice referred to in the message.

Security researchers at Morphisec analyzed the poisoned docs and noticed that there was an ActiveX control hidden below the embedded image.
A closer look revealed that the threat actor used the MsRdpClient10NotSafeForScripting class, which is used for remote control. Windows 10 is the minimum supported client and Windows Server 2016 is the minimum supported server.
ActiveX controls can be added to text or drawing layers in Word documents to make them interactive.
Clever delivery and execution
In a report today, Michael Gorelik of Morphisec writes that the JavaScript code for Ostap downloader is present in the document in font that has the same color as the background, making it invisible to the human eye.

Another interesting finding is that the attackers did not populate the "server" field in the MsRdpClient10NotSafeForScripting class, needed to establish a connection with a remote desktop server.

This was not a lapse from the attackers as the error that occurs helps execute their malicious code at a later time, thus evading detection.
When inspecting the macro, the researchers found that the "_OnDisconnected" function acts as a trigger but only after an error is returned for failing to connect to a non-existent server.
"The OSTAP will not execute unless the error number matches exactly to "disconnectReasonDNSLookupFailed" (260); the OSTAP wscript command is concatenated with a combination of characters that are dependent on the error number calculation." - Michael Gorelik, Morphisec
The backdoor is then executed immediately after taking the form of a .BAT file and the document form is closed.
Gorelik told BleepingComputer that this actor is not the only one relying on ActiveX control to execute malware. Other actors seen in January used the OnConnecting method that is easier to detect.
By contrast, the OnDiconnected method needs a specific return value and there is also a delay while the DNS lookup completes. This works to the attacker's advantage because scanners may miss the malicious activity and mark the file as benign.
[Update 02/28/2020, 16:01 EST]: Article updated to reflect a correction from Morphisec about misidentifying Ostap downloader with Griffon backdoor that is typically used by FIN7 threat actor.
 Photo provided by Amelia
Photo provided by Amelia Photo provided by Amelia of xHelper running on mobile device
Photo provided by Amelia of xHelper running on mobile device
 Photos provided by Amelia
Photos provided by Amelia



