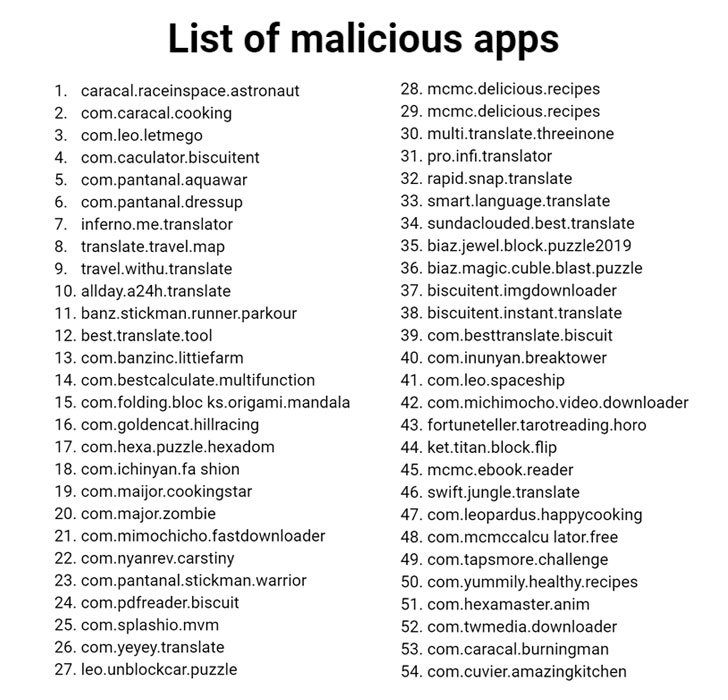
Zoombombing can be prevented, but it’s not as easy as it should be
By Casey Newton@CaseyNewton Mar 27, 2020, 3:37pm EDT
/cdn.vox-cdn.com/uploads/chorus_image/image/66566645/1212262073.jpg.0.jpg) Photo by Andrew Lichtenstein/Corbis via Getty Images
Photo by Andrew Lichtenstein/Corbis via Getty Images
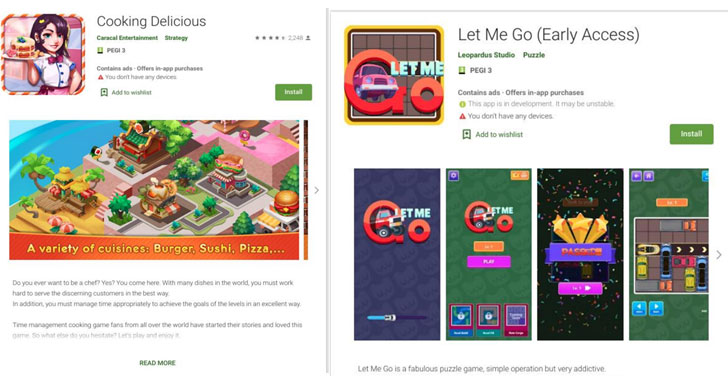
Zoom is an easy-to-use videoconferencing tool with a generous free tier. With people around the world isolating indoors to protect themselves against the spread of the coronavirus, it has never been more popular.
But its popularity has also attracted trolls. The phenomenon of “Zoombombing,” in which an uninvited guest uses Zoom’s screen-sharing feature to broadcast porn and shock videos, has been on the rise. Most Zoom meetings have a public link that, if clicked, allow anyone to join. Trolls have been collecting these links and sharing them in private chat groups, and then signing on to other people’s calls to cause mischief.
There’s an easy way to stop this from happening, but Zoom makes it needlessly difficult to find. If you schedule a meeting from the web interface, you won’t see the option to disable screen sharing. Instead:
Click on “Settings” in the left-hand menu
Scroll down to “Screen sharing” and under “Who can share?” click “Host Only”
Click on “Save”:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/19854779/Screen_Shot_2020_03_27_at_11.00.36_AM3_27.png)
Once you save your settings, future meetings that you start will have sharing disabled by default.
If you forget to change the setting before you start your meeting, there’s a way to modify your settings after it starts:
Once your Zoom meeting is running, click the caret to the right of the green “Share Screen” button in the center of the bottom row of icons
Click “Advanced Sharing Options...”
A dialog box will pop up allowing you to switch screen sharing availability from all participants to the host only.:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/19854787/Screen_Shot_2020_03_27_at_11.02.12_AM3_27.png)
And what if you’re creating a meeting from your mobile device?
To disable screen sharing after you’ve started your meeting:
Tap the More (...) button at the bottom right corner of the screen
Tap “Meeting Settings”
If you’re using an iPhone, scroll down to “Allow Participants to Share” and switch the toggle off.
By Casey Newton@CaseyNewton Mar 27, 2020, 3:37pm EDT
/cdn.vox-cdn.com/uploads/chorus_image/image/66566645/1212262073.jpg.0.jpg) Photo by Andrew Lichtenstein/Corbis via Getty Images
Photo by Andrew Lichtenstein/Corbis via Getty ImagesZoom is an easy-to-use videoconferencing tool with a generous free tier. With people around the world isolating indoors to protect themselves against the spread of the coronavirus, it has never been more popular.
But its popularity has also attracted trolls. The phenomenon of “Zoombombing,” in which an uninvited guest uses Zoom’s screen-sharing feature to broadcast porn and shock videos, has been on the rise. Most Zoom meetings have a public link that, if clicked, allow anyone to join. Trolls have been collecting these links and sharing them in private chat groups, and then signing on to other people’s calls to cause mischief.
There’s an easy way to stop this from happening, but Zoom makes it needlessly difficult to find. If you schedule a meeting from the web interface, you won’t see the option to disable screen sharing. Instead:
Click on “Settings” in the left-hand menu
Scroll down to “Screen sharing” and under “Who can share?” click “Host Only”
Click on “Save”
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/19854779/Screen_Shot_2020_03_27_at_11.00.36_AM3_27.png)
Once you save your settings, future meetings that you start will have sharing disabled by default.
If you forget to change the setting before you start your meeting, there’s a way to modify your settings after it starts:
Once your Zoom meeting is running, click the caret to the right of the green “Share Screen” button in the center of the bottom row of icons
Click “Advanced Sharing Options...”
A dialog box will pop up allowing you to switch screen sharing availability from all participants to the host only.
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/19854787/Screen_Shot_2020_03_27_at_11.02.12_AM3_27.png)
And what if you’re creating a meeting from your mobile device?
To disable screen sharing after you’ve started your meeting:
Tap the More (...) button at the bottom right corner of the screen
Tap “Meeting Settings”
If you’re using an iPhone, scroll down to “Allow Participants to Share” and switch the toggle off.
If you’re using an Android phone, find “Lock Share” and switch the toggle on.


 (Image credit: Malwarebytes)
(Image credit: Malwarebytes)